Day Two Cloud 087: Inside The World Of A Technical Marketer
Engineers are skeptical of vendor marketing, which is typically heavy on buzzwords and light on actual information. But technical marketing tries to change that dynamic by creating collateral to help engineers and practitioners understand a product. We get into this world with guest Martez Reed, Director of Technical Marketing at Morpheus Data.
The post Day Two Cloud 087: Inside The World Of A Technical Marketer appeared first on Packet Pushers.
3 Security Issues Overlooked By the NIST Framework
The NIST Cybersecurity Framework has some omissions but is still great. It should be considered the start of a journey and not the end destination.MANRS Fellowship 2021 Now Open

The MANRS (Mutually Agreed Norms for Routing Security) Fellowship Program 2021 is now accepting applications. If you are an emerging leader eager to improve the well-being of the Internet’s global routing system, apply now.
The program gives highly motivated individuals the chance to work alongside MANRS Ambassadors – industry leaders participating in the associated Ambassador Program that invited applications last month (details here).
Together, they will train diverse communities on good routing practices, analyze routing incidents, research into ways to secure routing, and survey the global policy landscape.
You can read about the 13 Fellows in last year’s inaugural program, which proved highly popular. The Internet Society supports this program as part of its work to reduce common routing threats and establish norms for network operations.
You can apply for a MANRS Fellowship in three different areas: training, research, and policy. Each Fellow will receive a stipend of $750 a month. The program will start in mid-April and run for up to eight months. You can apply for more than one category but will only be selected for one of them.
Online Training
Responsible for: Conducting MANRS online tutorial and virtual hands-on workshops, helping improve existing training and workshop Continue reading
Using the Python Rich library to display status indicators
I recently added a status indicator to my azruntime application. If users have a lot of VMs in their subscriptions, the azruntime application can take a long time to run. Users will appreciate seeing the status so they know the program is still running and is not hung up.

I used the Rich library to implement a status indicator. I had to learn more about Python context managers to understand how the Rich library’s progress bar and status indicators work. The Rich library’s documentation is aimed at intermediate-to-advanced programmers and the Rich tutorials I found on the web did not cover using the Rich library’s status update features.
In this post, I will share what I learned while adding a status indicator to my program and show you how to implement the same in your projects.
Rich library overview
The Rich library makes it easy to add color and style to terminal output. Rich can also render pretty tables, progress bars, markdown, syntax highlighted source code, tracebacks, and more.1
This post focuses only on creating a status indicator. To learn more about what Rich can do for you, I encourage you to read one of the excellent Rich overviews Continue reading
Chasing Anycast IP Addresses
One of my readers sent me this question:
My job required me to determine if one IP address is unicast or anycast. Is it possible to get this information from the bgp dump?
TL&DR: Not with anything close to 100% reliability.
If you’re not familiar with IP anycast: it’s a brilliant idea of advertising the same prefix from multiple independent locations, or the same IP address from multiple servers. Works like a charm for UDP (that’s how all root DNS servers are built) and supposedly pretty well across distant-enough locations for TCP (with a long list of caveats when used within a data center).
Chasing Anycast IP Addresses
One of my readers sent me this question:
My job required me to determine if one IP address is unicast or anycast. Is it possible to get this information from the bgp dump?
TL&DR: Not with anything close to 100% reliability. An academic research paper (HT: Andrea di Donato) documents a false-positive rate of around 10%.
If you’re not familiar with IP anycast: it’s a brilliant idea of advertising the same prefix from multiple independent locations, or the same IP address from multiple servers. Works like a charm for UDP (that’s how all root DNS servers are built) and supposedly pretty well across distant-enough locations for TCP (with a long list of caveats when used within a data center).
SEC 4. Complete guide for integrating Nokia, Arista, Cumulus, as well as CentOS and Raspberry PI Linux in your own PKI
Hello my friend,
In one of the previous blogposts we have share the details how you can build the containerised PKI relying Docker, Alpine Linux and OpenSSL. Today we’ll show how you can use it.
2
3
4
5
retrieval system, or transmitted in any form or by any
means, electronic, mechanical or photocopying, recording,
or otherwise, for commercial purposes without the
prior permission of the author.
How automation can increase the security?
In one of the recent articles dedicated to threats to the national security with respect to 5G caused by the current operation models in the big service providers, one the network automation were named as one of the key mitigation approaches. The reason is very simple: network automation allows you to keep (or even increase) the pace of the network changes with increasing the stability without increasing the size of your network operation teams.
We absolutely agree with this statement. We have observed ourselves that in many cases the key technical competence for service providers is being outsourced and in certain cases the service providers have to rely on the external parties to perform Continue reading
Tigera and Microsoft Extend the Power of Calico for Windows to AKS
Tigera, in collaboration with Microsoft, is thrilled to announce the public preview of Calico for Windows on Azure Kubernetes Service (AKS). While Calico has been available for self-managed Kubernetes workloads on Azure since 2018, many organizations are migrating their .NET and Windows workloads to the managed Kubernetes environment offered by AKS. Now the leading open-source Kubernetes network policy and security solution for Kubernetes enables Windows users to fulfill their policy and compliance requirements on Azure Kubernetes Service.
With the availability of Calico for Windows on AKS in public preview, enterprises can leverage the power and simplicity of Calico to enable a single solution that provides uniform Kubernetes network policy and security for their clusters across AKS, other clouds and on-premises, as well as across their choice of Windows, Linux, and mixed-node environments.
Project Calico is the most widely adopted open-source solution for Kubernetes networking and security, used on more than 1 million nodes across 166 countries. However, thousands of our users want to be sure that choosing Calico is the right decision for many years to come. Calico is the only solution that offers a pluggable data plane supporting Windows, standard Linux and eBPF, thus future-proofing their decision Continue reading
Why AI is Eating Networking
Networking teams are just starting their AIOps journey. In the next five years, AI assistants will be considered integral members.Betting On Virtual Events In A Post-Covid World
In-person events will return some day. In the meantime, a huge crop of tech companies and investors are betting that virtual events can thrive not just during a pandemic, but beyond.
The post Betting On Virtual Events In A Post-Covid World appeared first on Packet Pushers.
Cloudflare recognized as a ‘Leader’ in The Forrester Wave for DDoS Mitigation Solutions
We’re thrilled to announce that Cloudflare has been named a leader in The Forrester WaveTM: DDoS Mitigation Solutions, Q1 2021. You can download a complimentary copy of the report here.
According to the report, written by, Forrester Senior Analyst for Security and Risk, David Holmes, “Cloudflare protects against DDoS from the edge, and fast… customer references view Cloudflare’s edge network as a compelling way to protect and deliver applications.”
Unmetered and unlimited DDoS protection for all
Cloudflare was founded with the mission to help build a better Internet — one where the impact of DDoS attacks is a thing of the past. Over the last 10 years, we have been unwavering in our efforts to protect our customers’ Internet properties from DDoS attacks of any size or kind. In 2017, we announced unmetered DDoS protection for free — as part of every Cloudflare service and plan including the Free plan — to make sure every organization can stay protected and available.
Thanks to our home-grown automated DDoS protection systems, we’re able to provide unmetered and unlimited DDoS protection for free. Our automated systems constantly analyze traffic samples asynchronously as to avoid impact to performance. They scan for Continue reading
HTTP Protocol, Web Page Waterfalls and Complexity
 One aspect of networking is that some understanding of the protocols using the network is required. As HTTPS replaces nearly all other protocols I would suggest that everyone needs a working understanding of how a web page is fetched by a web browser. WebPageTest is a community tool that reads web pages and then displays […]
One aspect of networking is that some understanding of the protocols using the network is required. As HTTPS replaces nearly all other protocols I would suggest that everyone needs a working understanding of how a web page is fetched by a web browser. WebPageTest is a community tool that reads web pages and then displays […]
How to execute an object file: Part 1
Calling a simple function without linking
When we write software using a high-level compiled programming language, there are usually a number of steps involved in transforming our source code into the final executable binary:
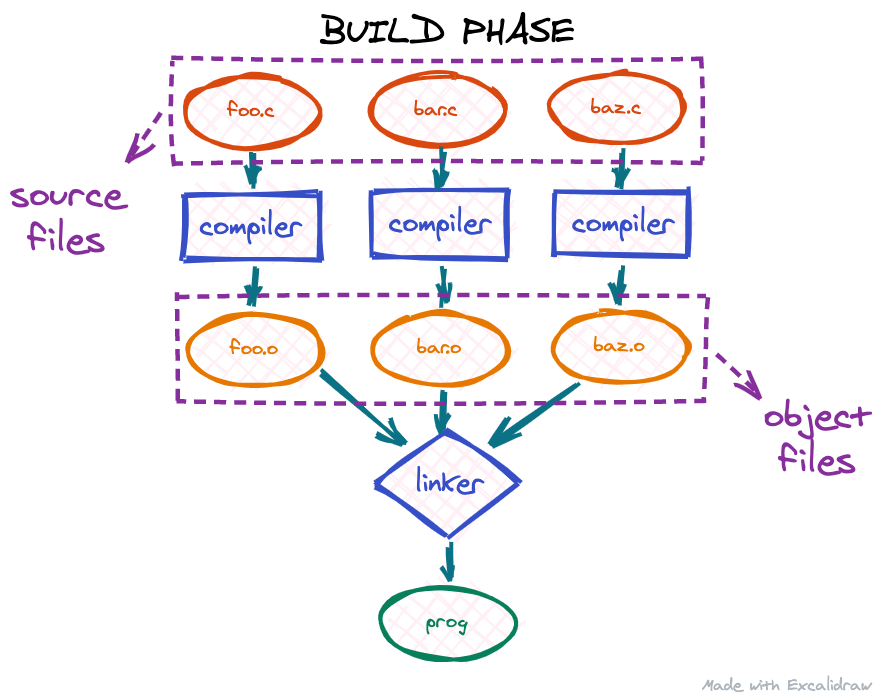
First, our source files are compiled by a compiler translating the high-level programming language into machine code. The output of the compiler is a number of object files. If the project contains multiple source files, we usually get as many object files. The next step is the linker: since the code in different object files may reference each other, the linker is responsible for assembling all these object files into one big program and binding these references together. The output of the linker is usually our target executable, so only one file.
However, at this point, our executable might still be incomplete. These days, most executables on Linux are dynamically linked: the executable itself does not have all the code it needs to run a program. Instead it expects to "borrow" part of the code at runtime from shared libraries for some of its functionality:
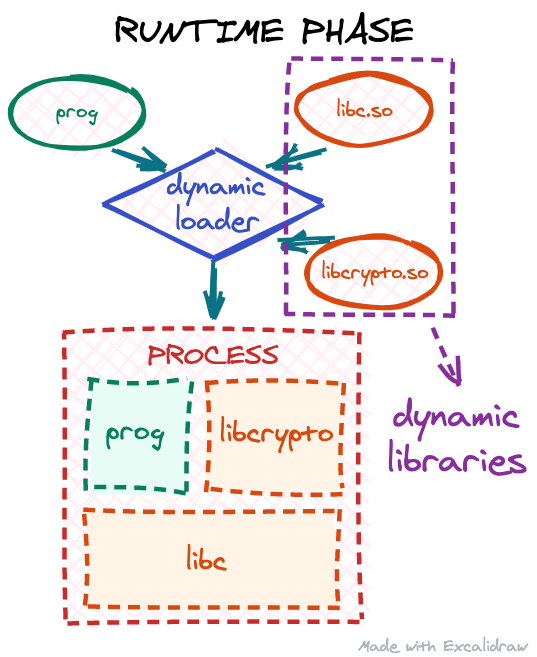
This process is called runtime linking: when our executable is being started, the operating system will invoke the dynamic Continue reading
Impact of Azure Subnets on High Availability Designs
Now that you know all about regions and availability zones (AZ) and the ways AWS and Azure implement subnets, let’s get to the crux of the original question Daniel Dib sent me:
As I understand it, subnets in Azure span availability zones. Do you see any drawback to this? You mentioned that it’s difficult to create application swimlanes that way. But does subnet matter if your VMs are in different AZs?
It’s time I explain the concepts of application swimlanes and how they apply to availability zones in public clouds.
Impact of Azure Subnets on High Availability Designs
Now that you know all about regions and availability zones (AZ) and the ways AWS and Azure implement subnets, let’s get to the crux of the original question Daniel Dib sent me:
As I understand it, subnets in Azure span availability zones. Do you see any drawback to this? You mentioned that it’s difficult to create application swimlanes that way. But does subnet matter if your VMs are in different AZs?
It’s time I explain the concepts of application swimlanes and how they apply to availability zones in public clouds.