Bill Krause | Zero to a Million Ethernet Ports + The Epiphany
Hosts Brandon and Derick have the honor of interviewing Bill Krause and hearing some fascinating stories about the early days of Silicon Valley, including the origins of HP's first computer division, and how Bill (along with previous podcast guest Bob Metcalfe) took Ethernet from zero to one million ports ahead of their already-ambitious timeline.
Bill is a tech luminary, having served as the CEO and President, and then Board Chairman, of 3Com, growing the business from a VC-backed startup to a publicly traded $1B company with global operations. Prior to 3Com, Bill was the GM of HP's first personal computer division, and grew that business exponentially as well. He's currently a board partner with Andreessen Horowitz as well as Chairman of the Board at Veritas, and he also serves on the boards of CommScope, SmartCar, and Forward Networks. Bill is a noted philanthropist; he and his wife Gay Krause have funded many national and local programs focusing on education, leadership, and ethics.
Tune in and join us to hear Bill's amazing stories, his lessons learned, and his profound advice to young entrepreneurs.
The Hedge Podcast #69: Container Networking Done Right
Everyone who’s heard me talk about container networking knows I think it’s a bit of a disaster. This is what you get, though, when someone says “that’s really complex, I can discard the years of experience others have in designing this sort of thing and build something a lot simpler…” The result is usually something that’s more complex. Alex Pollitt joins Tom Ammon and I to discuss container networking, and new options that do container networking right.
Safety Planning for the Data Center
Why safety is rapidly becoming a key feature of data centers and how to make it part of yours.Technology Must Be Net Pain Negative – Video
Day Two Cloud podcast co-host Ned Bellavance asks Envoy creator Matt Klein about the tipping point for certain tech. When do you need an API gateway? Egress control? A service mesh? Matt is a “keep it as simple as you can for as long as you can” sort of guy. Why adopt technology that doesn’t […]
The post Technology Must Be Net Pain Negative – Video appeared first on Packet Pushers.
Day Two Cloud 083: Should Cloud Be A Public Utility?
Computing power is a vital part of modern life. Should access to that power be more equitably distributed? Is there a role for a public-utility-style cloud that could make computing more cost-effective and accessible to a broader number of constituencies? These are the starting questions for today's episode of Day Two Cloud. Our guest is Dwayne Monroe, a cloud architect, consultant, and author.Day Two Cloud 083: Should Cloud Be A Public Utility?
Computing power is a vital part of modern life. Should access to that power be more equitably distributed? Is there a role for a public-utility-style cloud that could make computing more cost-effective and accessible to a broader number of constituencies? These are the starting questions for today's episode of Day Two Cloud. Our guest is Dwayne Monroe, a cloud architect, consultant, and author.
The post Day Two Cloud 083: Should Cloud Be A Public Utility? appeared first on Packet Pushers.
The effect of switching to TCMalloc on RocksDB memory use
In previous posts we wrote about our configuration distribution system Quicksilver and the story of migrating its storage engine to RocksDB. This solution proved to be fast, resilient and stable. During the migration process, we noticed that Quicksilver memory consumption was unexpectedly high. After our investigation we found out that the root cause was a default memory allocator that we used. Switching memory allocator improved service memory consumption by almost three times.
Unexpected memory growth
After migrating to RocksDB, the memory used by the application increased significantly. Also, the way memory was growing over time looked suspicious. It was around 15GB immediately after start and then was steadily growing for multiple days, until stabilizing at around 30GB. Below, you can see a memory consumption increase after migrating one of our test instances to RocksDB.
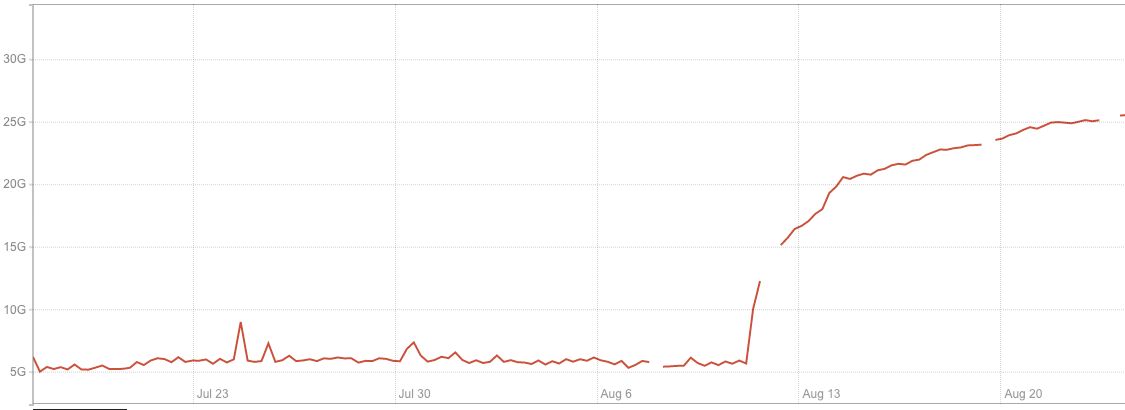
We started our investigation with heap profiling with the assumption that we had a memory leak somewhere and found that heap size was almost three times less than the RSS value reported by the operating system. So, if our application does not actually use all this memory, it means that memory is ‘lost’ somewhere between the system and our application, which points to possible problems with Continue reading
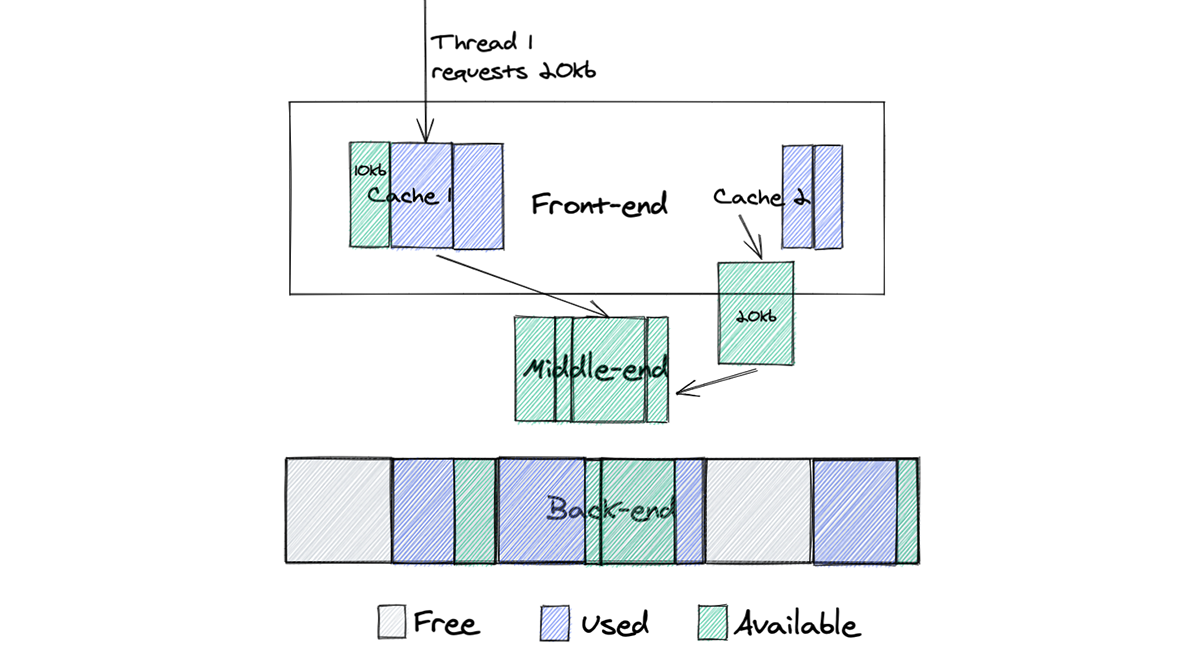
Impact of Centralized Control Plane Partitioning
A long-time reader sent me a series of questions about the impact of WAN partitioning in case of an SDN-based network spanning multiple locations after watching the Architectures part of Data Center Fabrics webinar. He therefore focused on the specific case of centralized control plane (read: an equivalent of a stackable switch) with distributed controller cluster (read: switch stack spread across multiple locations).
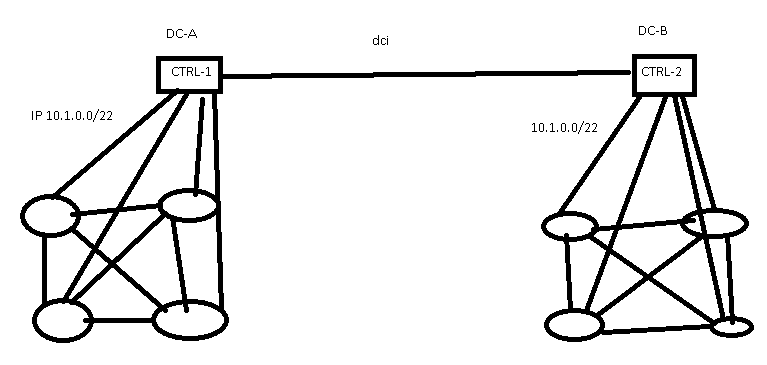
SDN controllers spread across multiple data centers
Impact of Centralized Control Plane Partitioning
A long-time reader sent me a series of questions about the impact of WAN partitioning in case of an SDN-based network spanning multiple locations after watching the Architectures part of Data Center Fabrics webinar. He therefore focused on the specific case of centralized control plane (read: an equivalent of a stackable switch) with distributed controller cluster (read: switch stack spread across multiple locations).

SDN controllers spread across multiple data centers
The Internet of Trash
It's often a clear signal that we’re in in deep trouble when politicians believe that they need to lend a hand and help out with regulations. Either the actions of the market have failed consumers and some form of public action is necessary to address aspects of this failure, or the situation is so desperately broken and beyond help that the legislature is performing a largely ineffectual action that serves more to disclaim any residual responsibility on the part of the public sector for the mess that we’ve created.Missing Cron Email When Restarting smtpd
I have a cron job that renews an SSL
certificate from Let's
Encrypt, and then restarts the smtpd daemon so that the new certificate is
picked up. This all works fine--as proven by both the presence of a new, valid
cert on disk, and smtpd successfully restarting--but cron never sends an email
with the output of the job. What gives?
azruntime: Manage Azure Infrastructure with Python
I wrote a new Python script called azruntime. It helps me manage my Azure VMs. The script is open-source and should work for anyone who also uses the Azure CLI. azruntime is available on my azure-scripts GitHub repository.

I learned a lot about the Azure Python SDK while working on the azruntime project. In this post, I share what I learned and highlight the more interesting topics like how to find information faster in the Azure Python SDK documentation, Azure authorization, and sorting nested lists by key.
Learning the Azure Python SDK and API
Microsoft offers excellent documentation of all its Azure services, including detailed documentation for the Azure Python SDK. The problem may be that there is so much documentation it is hard to know where to start.
In my opinion, the best place to start is to look at the Azure sample scripts available at the following URL:
Search by keyword or category. When you find a script that appears to display some of the functionality you want to implement, use a search engine to search for the Azure Python SDK classes and functions you see used in the sample scripts.
This is a faster Continue reading