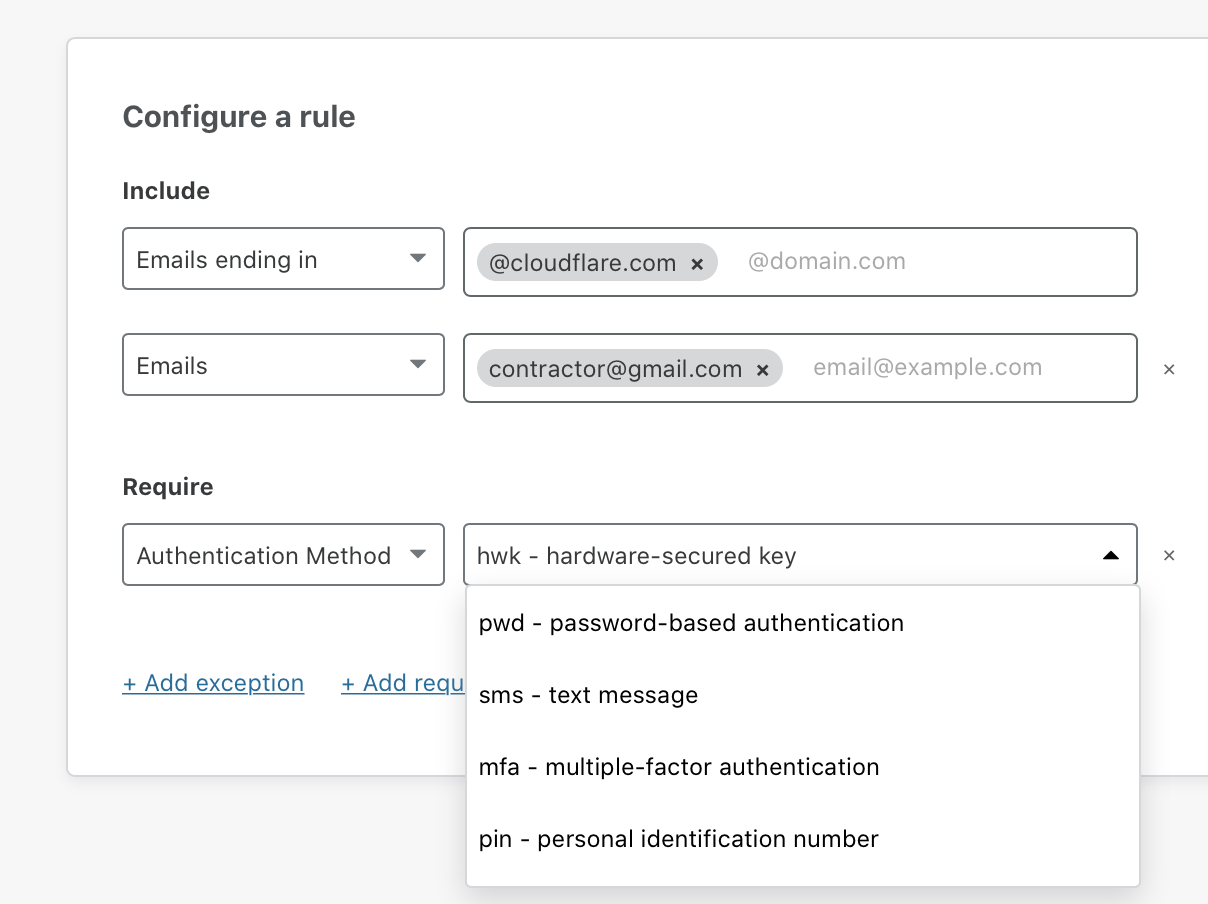
Require hard key auth with Cloudflare Access
Last month, attackers compromised a Twitter team member’s access to an internal administrative panel in order to take over high-profile accounts. Full details of the breach are still pending, but Twitter has shared that the attackers stole credentials through a coordinated spear phishing attack.
The attackers convinced a team member to share login permissions, giving the attackers the ability to access the Twitter control plane. Once authenticated, they sent password reset flows to email accounts they controlled in order to hijack the Twitter accounts.
Administrative panels like Twitter’s are a rich target for phishing attacks because they give attackers a backdoor to privileged systems. Customer-facing teams at SaaS companies rely on these administrative panels to update end-user data and troubleshoot user account issues. If an attacker can compromise a single team member’s account they can potentially impact thousands of end users.
We have our own administrative panel at Cloudflare and we’ve deployed a number of safeguards over the last several years to keep it secure from phishing attacks. However, we had no way to enforce the security feature we think would most insulate us from phishing attacks: physical hard keys.
With hard keys, users can only login when they use Continue reading
Orange Clouding with Secondary DNS
What is secondary DNS?
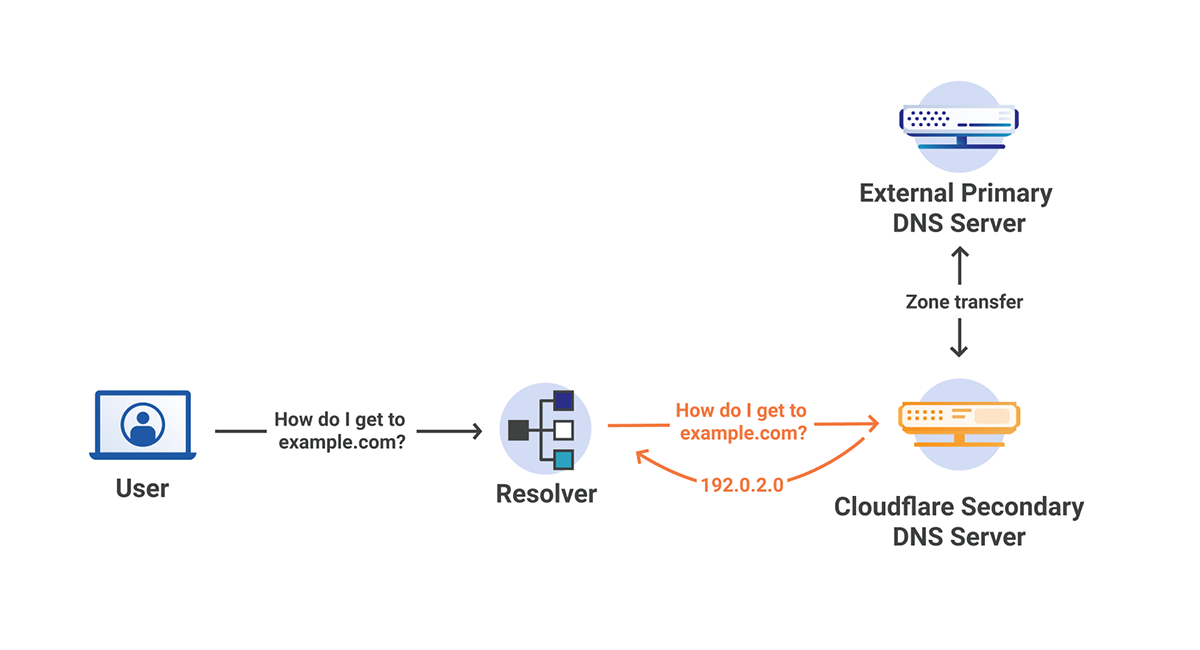
In a traditional sense, secondary DNS servers act as a backup to the primary authoritative DNS server. When a change is made to the records on the primary server, a zone transfer occurs, synchronizing the secondary DNS servers with the primary server. The secondary servers can then serve the records as if they were the primary server, however changes can only be made by the primary server, not the secondary servers. This creates redundancy across many different servers that can be distributed as necessary.
There are many common ways to take advantage of Secondary DNS, some of which are:
- Secondary DNS as passive backup - The secondary DNS server sits idle until the primary server goes down, at which point a failover can occur and the secondary can start serving records.
- Secondary DNS as active backup - The secondary DNS server works alongside the primary server to serve records.
- Secondary DNS with a hidden primary - The nameserver records at the registrar point towards the secondary servers only, essentially treating them as the primary nameservers.
What is secondary DNS Override?
Secondary DNS Override builds on the Secondary DNS with a hidden primary model by allowing our Continue reading
Doing Good for the Internet – Alex Band, Director @ NLnet Labs
NLnet Labs is a not-for-profit foundation with a long heritage in research and development, Internet architecture and governance, as well as stability and security in the area of DNS and inter-domain routing.
In this episode you will hear all about doing good for the internet with open source, DNS and RPKI.
In this episode you will hear all about doing good for the internet with open source, DNS and RPKI.

Which Public Cloud Should I Master First?
I got a question along these lines from a friend of mine:
Google recently announced a huge data center build in country to open new GCP regions. Does that mean I should invest into mastering GCP or should I focus on some other public cloud platform?
As always, the right answer is “it depends”, for example:
Vrnetlab – Run virtual routers in Docker containers
It’s time to have a look at some Network Automation tools. Today I want to introduce you to Vrnetlab, great piece of software that allows you to run virtual routers inside Docker containers. We’ll talk about what Vrnetlab does and what are its selling points. Then we’ll see how to bring up lab devices by hand and how to use them.
Contents
- Vrnetlab overview
- Installing Vrnetlab and its dependencies
- Building images with virtual devices
- Launching virtual devices
- Helper bash functions
- Accessing devices
- Connecting devices together
- Bring up pre-defined topology with Docker Compose
- Conclusion
- References
- GitHub repository with resources for this post
Vrnetlab overview
Vrnetlab provides convenient way of building virtualized network environments by leveraging existing Docker ecosystem.
This means that you can take image of virtual appliance provided by the vendor and use Vrnetlab to create containers for it. The selling point here is that the whole tool-chain was created with automation in mind, that is you can build your network automation CI pipeline on top of Vrnetlab and no human is needed to spin up the environment, and run Continue reading
ESXi VM – The CPU has been disabled by the guest operating system
For some weeks now, a couple of my virtual machines on ESXi would stop working out of nowhere. They were completely unresponsive (including via the ESXi VM Console). Nothing would help, except a shutdown / start of the VM. Just to find out later that, randomly, the VM would become unresponsive again. The only human … Continue reading ESXi VM – The CPU has been disabled by the guest operating systemSplit-tunnel VPNs—friend or foe?
Virtual private networks (VPNs) provide security when remote workers access corporate networks, but they’re notoriously slow. Backhauling all traffic for all remote users through the corporate data center just isn’t practical when work from home really starts to scale. Fortunately, VPNs can be configured to operate in more than one way.
Today, most organizations—regardless of size—use some combination of on-premises and public cloud computing. This means that some requests need to go to one or more corporate data centers, while some need to find their way to the Internet.
Traditional VPNs send all requests—both corporate-bound and Internet-bound—through the corporate network because that’s where the corporate information security defenses are located. Today, this approach is causing significant performance problems.
Scaling …
The most popular traditional solution to the problem of VPN performance problems was to just buy a bigger router or firewall. The overhead of the VPN tunnel on throughput isn’t that large, and many traditional corporate applications weren’t latency sensitive. This meant that performance problems usually occurred because the device where the VPNs terminated—the router or firewall—just didn’t have enough processing power to handle the required number of concurrent sessions at the current level of throughput usage.
Times have changed, Continue reading
Day Two Cloud 062: What Do Words Mean?
Some words mean different things to different IT disciplines. And tech vendors often twist the meaning of technical terms to suit their own purposes. On today's Day Two Cloud, guest Karen Lopez helps us sort out the semantics of IT language and discusses why accuracy matters.Day Two Cloud 062: What Do Words Mean?
Some words mean different things to different IT disciplines. And tech vendors often twist the meaning of technical terms to suit their own purposes. On today's Day Two Cloud, guest Karen Lopez helps us sort out the semantics of IT language and discusses why accuracy matters.
The post Day Two Cloud 062: What Do Words Mean? appeared first on Packet Pushers.
The Hedge Podcast 48: Chris Romeo and the State of Security
Chris Romeo is a famous application security expert who has spent the last several years building a consulting and training company called Security Journey. Chris joins Tom and Russ to talk about the state of security and what network engineers need to know about security from an application perspective.
Perimeter Security is Changing
The long standing tradition of having a secure network perimeter and a lightly protected interior has been going by the wayside for quite some time now. But the introduction of new models of connectivity are forcing us to change the way we look at security all together and invent whole new models for protecting our networks. In today’s episode we’re going to be exploring how these changes are impacting security and talk about some of these new models that meet the needs of modern networks.
 |
Network Collective thanks NVIDIA for sponsoring today’s episode. NVIDIA is positioned as the leader in open networking and provides end-to-end solutions at all layers of the software and hardware stack. You can experience NVIDIA Cumulus in the Cloud for free! Head on over to:
https://cumulusnetworks.com/automationpod |
Outro Music:
Danger Storm Kevin MacLeod (incompetech.com)
Licensed under Creative Commons: By Attribution 3.0 License
http://creativecommons.org/licenses/by/3.0/
The post Perimeter Security is Changing appeared first on Network Collective.
Chapterthon 2020: A Time for Internet Society Chapters and SIGs to Shine

The Internet Society 2020 Chapterthon is live and moving fast! We’re so excited to see the applications that have already ticked in.
What is Chapterthon?
Chapterthon is an opportunity for Chapters and Special Interest Groups (SIGs) to engage their members in a worldwide Internet Society competition. Out of dozens of applicants, one Chapterthon winner is selected and awarded prize money. But the real winner is the global community, who benefit from projects that help people connect to the Internet and help them do it securely.
This year is different – one that’s been full of difficulties, but also tenacity, creativity, and uplift. So we’re doing Chapterthon a little differently, too. We’re dedicating it to the people and the medium helping us through.
I Heart the Internet
Internet Society Chapters and SIGs have developed innovative solutions to help their communities through COVID-19. We want to shine a light on their work and make sure it becomes a resource for all. So we’re asking Chapterthon participants to submit tutorials and manuals for their creative and impactful projects. These blueprints will become part of the “I Heart the Internet Knowledge Hub,” a resource for peers and partners around the world to broaden the Continue reading
Virtual Open Office Hours – Late August 2020
 Virtual Open Office is a chance for people to gather and discuss any topics you find interesting. Open to Anyone. No cost or commitment. I’ll be there with a coffee/tea or a beer/cocktail (as appropriate) Tuesday, Aug 25, 1000BST/0900UTC intended for European, Australia/Oceania and East Asian Friday, Aug 28 2000BST/1900UTC which might suit people in […]
Virtual Open Office is a chance for people to gather and discuss any topics you find interesting. Open to Anyone. No cost or commitment. I’ll be there with a coffee/tea or a beer/cocktail (as appropriate) Tuesday, Aug 25, 1000BST/0900UTC intended for European, Australia/Oceania and East Asian Friday, Aug 28 2000BST/1900UTC which might suit people in […]
New and improved Workers Docs
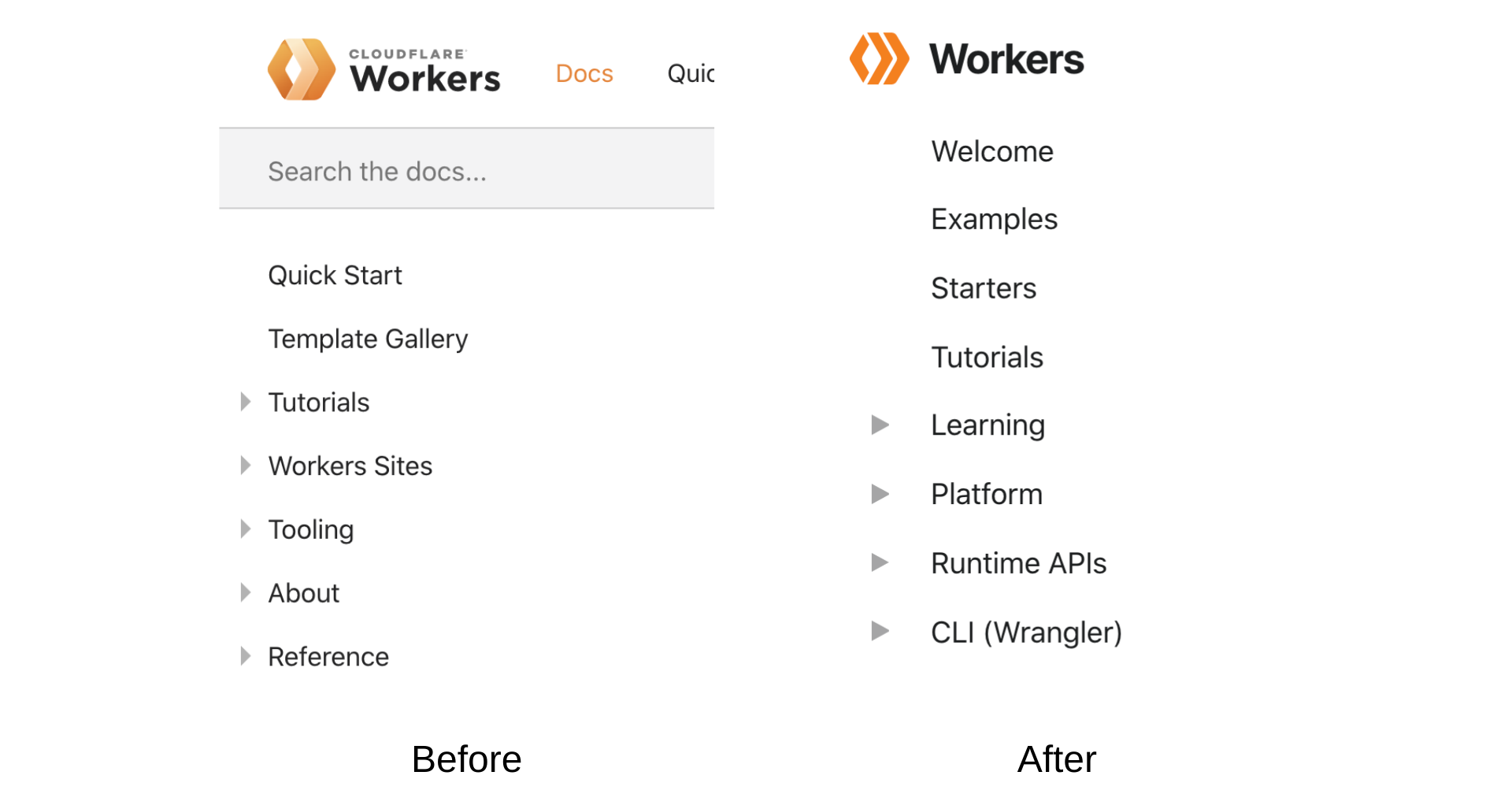
I’m happy to announce several updates to the Workers Docs that will allow you to take full advantage of our Workers platform. We integrated your feedback about the Docs user experience and design. We reorganized and reformatted all of our content. We upgraded the Docs engine to add new UI components. The documentation is now intuitive to navigate and the content is now easy and enjoyable to read.
You can find our new and improved documentation site here and can find the docs engine on our repo.
We hope this creates a better developer experience for you and makes the Docs more approachable to beginners. We plan to use our work and improvements for the Workers Docs to revamp docs for other Cloudflare products too.
Here’s a more detailed breakdown of the Workers Docs update.
Content Organization: We reorganized site content into four categories to make it easier for you to read and find content: Tutorials, How-to guides, Technical reference, and Learning. The new content structure is heavily inspired by Divio’s documentation system.
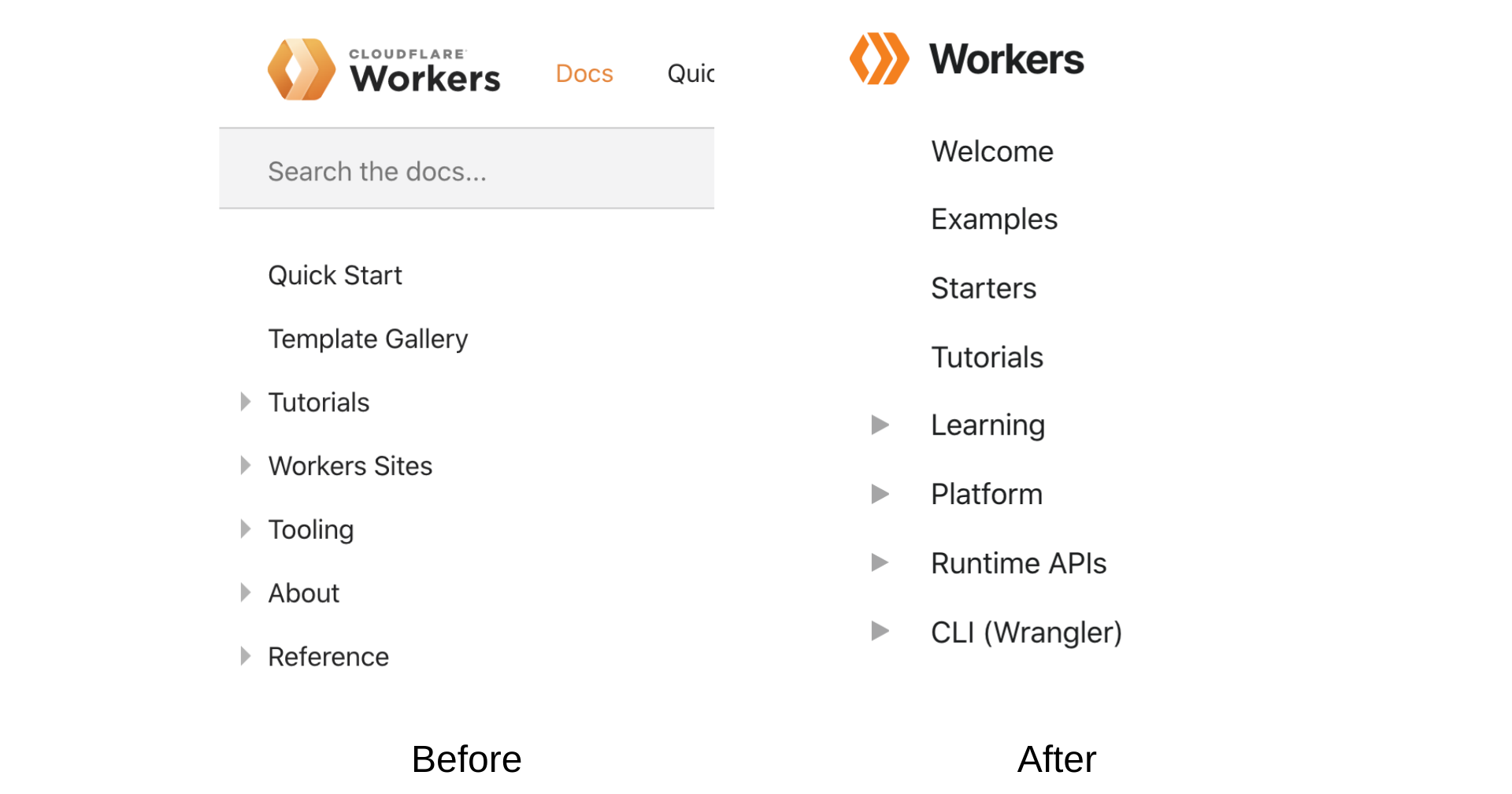
The tutorials section groups together step by step guides for building a specific project on Workers (e.g. teaching a beginner how to cook). The how-to guides Continue reading
Opinion: You Represent Your Employer When ….
 Your bio says "words are mine" but your feed has company content all over it.
Your bio says "words are mine" but your feed has company content all over it.
Worth Reading: NetDevOps Concepts – Minimum Viable Product
Brett Lykins published an excellent description of what an automation Minimum Viable Product could be.
Not surprisingly, he’s almost perfectly in sync with what we’ve been telling networking engineers in ipSpace.net Network Automation online course:
- Start small
- Go for quick wins
- Do read-only stuff before modifying device configurations
- Test, test, test…