Cisco Live: Can Tech Win Against a Pandemic, Systematic Racism?
CEO Chuck Robbins unveiled Cisco’s new purpose statement at Cisco Live: To power an inclusive...
Seeing the Future with Mathematical Network Verification
Network verification is more important than ever. Here's how Forward Networks is revolutionizing...
Introducing Cache Analytics
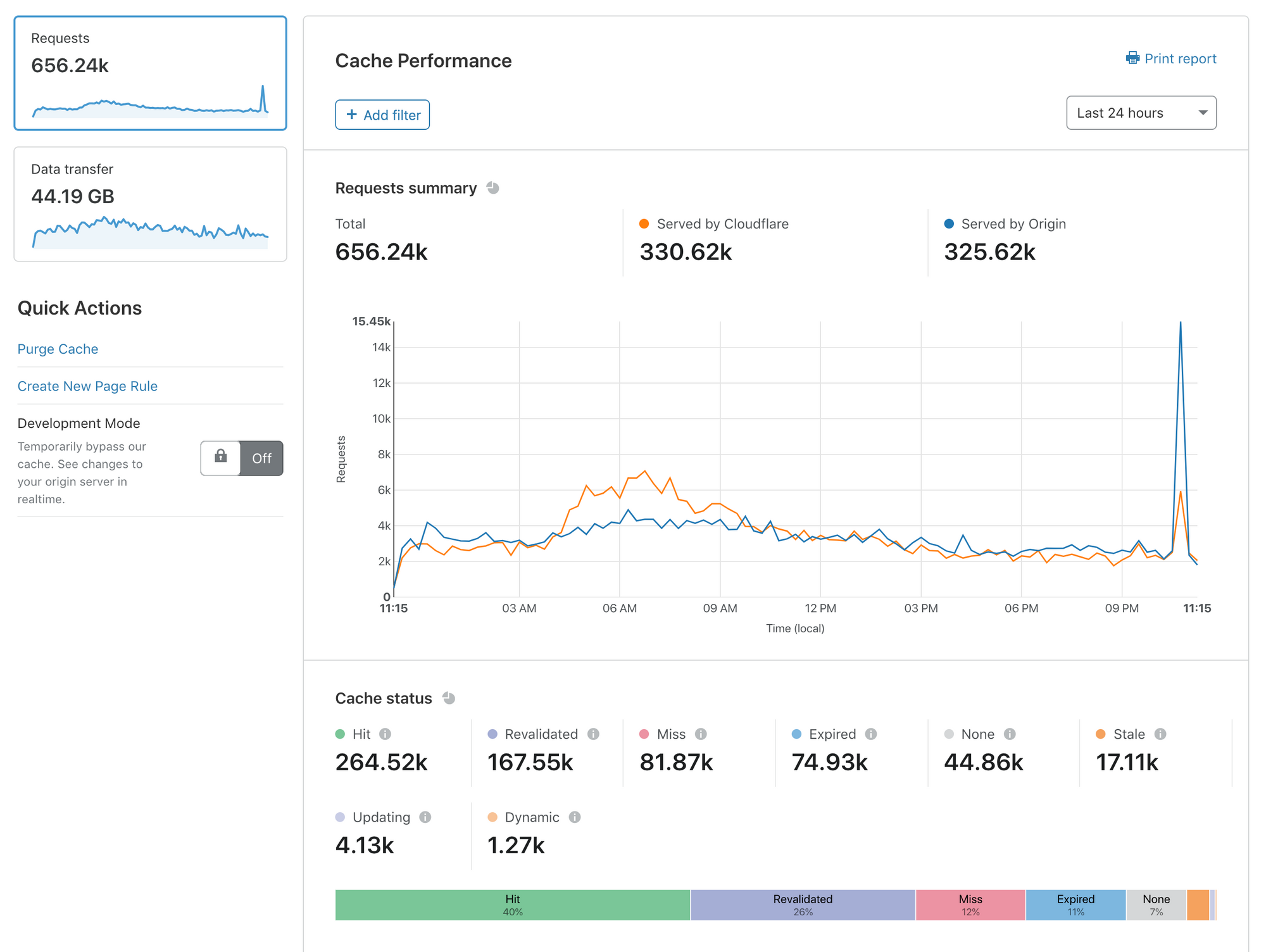
Today, I’m delighted to announce Cache Analytics: a new tool that gives deeper exploration capabilities into what Cloudflare’s caching and content delivery services are doing for your web presence.
Caching is the most effective way to improve the performance and economics of serving your website to the world. Unsurprisingly, customers consistently ask us how they can optimize their cache performance to get the most out of Cloudflare.
With Cache Analytics, it’s easier than ever to learn how to speed up your website, and reduce traffic sent to your origin. Some of my favorite capabilities include:
- See what resources are missing from cache, expired, or never eligible for cache in the first place
- Slice and dice your data as you see fit: filter by hostnames, or see a list of top URLs that miss cache
- Switch between views of requests and data Transfer to understand both performance and cost
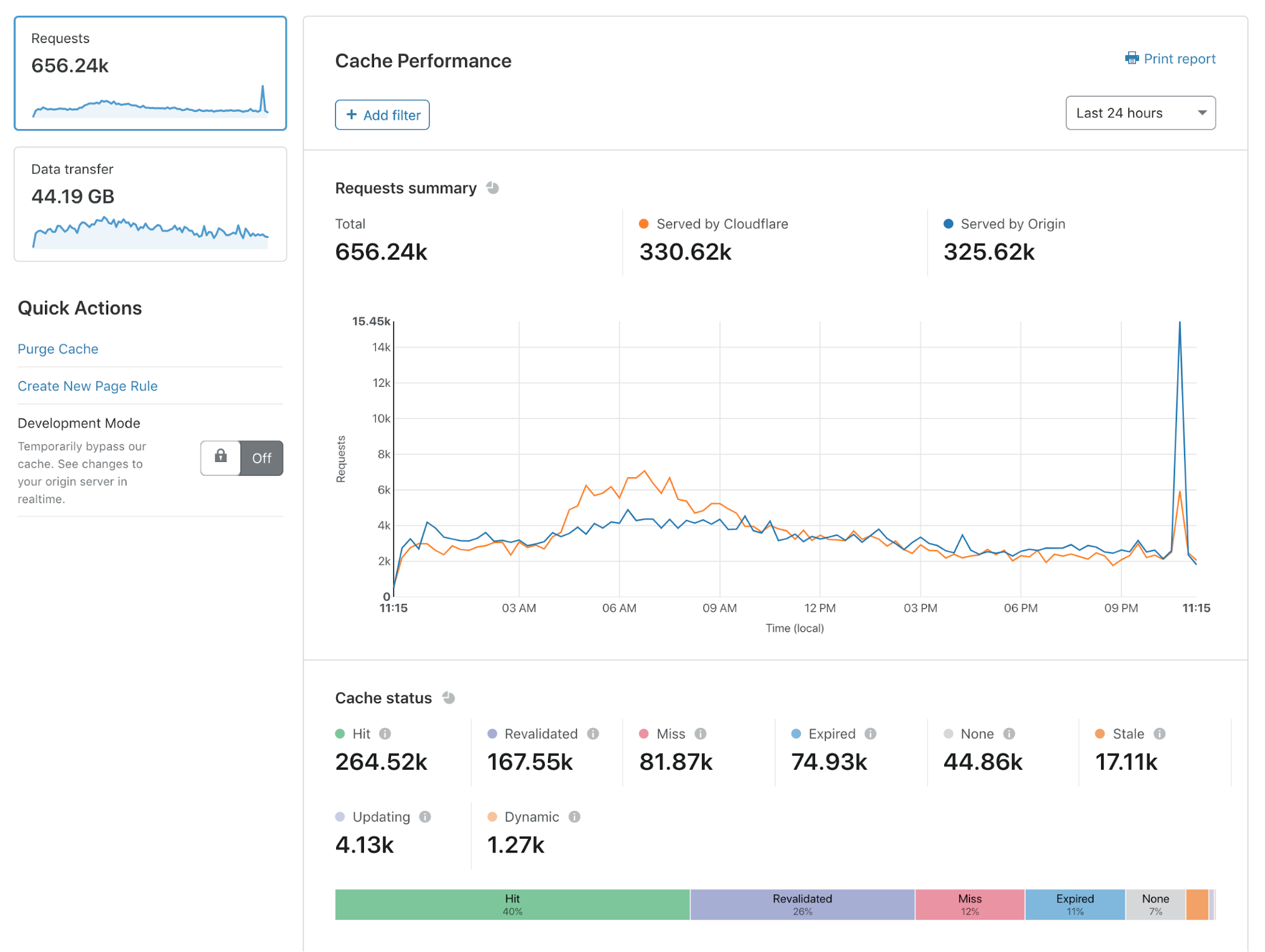
Cache Analytics is available today for all customers on our Pro, Business, and Enterprise plans.
In this blog post, I’ll explain why we built Cache Analytics and how you can get the most out of it.
Why do we need analytics focused on caching?
If you want Continue reading
7 Layers Interview: Rahul Subramany of SimpliSafe on IoT Security ‘It is a pretty complicated world out there’
Listen to this Q&A session between Senior Product Manager at SimpliSafe, Rahul Subramany, and...
AT&T Delays Nationwide 5G Back to ‘End of the Year’
The operator, as recently as last month, said it was on track to deploy nationwide 5G this summer.
Google Filestore Primed to Tackle HPC Workloads, Fight COVID-19
Google Cloud added a new high-performance computing tool to the therapeutics research arsenal with...
Cumulus Networks’ President and Chief Product Officer, Partho Mishra, on the NVIDIA-Cumulus acquisition.
With the acquisition of Cumulus Networks and Mellanox by NVIDIA, there have been a lot of questions regarding the strategic focus of the new networking business unit at NVIDIA and the future of the open networking approach that Cumulus Networks pioneered.
The open networking journey continues
Mellanox and Cumulus are absolutely committed to open networking and allowing our customers to pick best-of-breed solutions. Cumulus will continue to support all of the hardware platforms on our Hardware Compatibility List (HCL) and to add new hardware platforms from multiple hardware partners to the HCL. Mellanox already offers multiple Network-Operating-Systems — ONYX, SONIC, Cumulus Linux – to customers and this continues unchanged. In terms of total code commits to open source projects, such as FRR, SONIC and the Linux networking kernel, Cumulus+Mellanox have contributed very heavily in the past and will continue to do so in the future. This is an integral part of our DNA.
Check out the latest episode of Kernel of Truth to hear me and Amit Katz discuss more about the future of open networking including how SONIC and Cumulus Linux will work together, what happens to open “campus” networking and the next generation of in-band telemetry.
The next Continue reading
Cisco Security Biz Gets New Chief, New Name, Unified Platform
SecureX integrates all of Cisco’s network, endpoint, cloud, and application security products, as...
HPE Edge Orchestrator Targets Telco 5G, Edge Plans
The platform is designed to allow telecom operators to maintain more control over their edge...
Telefónica’s ElevenPaths Taps Fortinet for Industrial Security
Fortinet’s platform provides visibility and management across IT and OT devices, which allows...
Internet Society and Alliance for Affordable Internet Partner to Promote Community Networks and Expand Access for All

The Internet Society and the Alliance for Affordable Internet (A4AI), an initiative of the World Wide Web Foundation, have entered into a Memorandum of Understanding (MoU) to further their existing partnership to collaborate on promoting community networks to expand meaningful connectivity, and other areas of joint interest.
A4AI is a global coalition working to drive down the cost of Internet access in low- and middle-income countries through policy and regulatory reform. The Internet Society is a member of A4AI, and the two organizations share a vision of an open, globally connected, secure, and trustworthy Internet for everyone.
Both organizations have emphasized the importance of solid research, capacity building, and advocacy to develop the policies needed to reduce the cost to connect and enable everyone, everywhere to access Internet connectivity. A4AI and ISOC believe community networks provide a sustainable solution to address connectivity gaps that exist in underserved urban, remote, and rural areas around the world.
This MoU formalizes a longstanding relationship between the two organizations. In the past, we’ve worked together to collaborate on common policy and regulatory objectives across numerous UN and international fora to promote and advocate for the expansion of public access solutions through community networks, Continue reading
Full Stack Journey 043: Lighting Up The Firecracker Project For Serverless Computing
Firecracker is an open-source project, launched by AWS, for serverless computing. On today's Full Stack Journey podcast, Michael Hausenblas of AWS joins host Scott Lowe to talk about Firecracker, how it works, its adoption, and more. They also touch on EKS, Fargate, and Lambda.Full Stack Journey 043: Lighting Up The Firecracker Project For Serverless Computing
Firecracker is an open-source project, launched by AWS, for serverless computing. On today's Full Stack Journey podcast, Michael Hausenblas of AWS joins host Scott Lowe to talk about Firecracker, how it works, its adoption, and more. They also touch on EKS, Fargate, and Lambda.
The post Full Stack Journey 043: Lighting Up The Firecracker Project For Serverless Computing appeared first on Packet Pushers.
Automate Image Compression for Blogging

Adding images and screenshots to posts is good but size is a consideration
The post Automate Image Compression for Blogging appeared first on EtherealMind.
EVPN: The Great Unifying Theory of VPN Control Planes?
I claimed that “EVPN is the control plane for layer-2 and layer-3 VPNs” in the Using VXLAN and EVPN to Build Active-Active Data Centers interview a long long while ago and got this response from one of the readers:
To me, that doesn’t compute. For layer-3 VPNs I couldn’t care less about EVPN, they have their own control planes.
Apart from EVPN, there’s a single standardized scalable control plane for layer-3 VPNs: BGP VPNv4 address family using MPLS labels. Maybe EVPN could be a better solution (opinions differ, see EVPN Technical Deep Dive webinar for more details).
Dell PowerScale Restores Order to Unstructured Data
In addition to the new unstructured data storage systems, Dell unveiled intelligent data software...
Extreme’s New Normal Looks Like Unlimited Cloud Data, WiFi 6
The networking vendor is set to begin offering unlimited data to its cloud customers for the...
China Unicom Selects Nokia Core Networking Products for 5G
Deal includes multiple Nokia Software, ION products, including Unified Data Management, User Plane...