Segment Routing explained – Julian Lucek, Distinguished Engineer @ Juniper Networks
In this episode of The Routing Table Podcast Rick and Melchior ask Juniper Networks Distinguished Engineer Julian Lucek everything about Segment Routing.
We start with some basics and discuss differences between SR-MPLS, SRv6 and SRm6. We also look into why choosing one over the other.

Azure Networking 101
A few weeks ago I described the basics of AWS networking, now it’s time to describe how different Azure is.
As always, it would be best to watch my Azure Networking webinar to get the details. This blog post is the abridged CliffsNotes version of the webinar (and here‘s the reason I won’t write a similar blog post for other public clouds ;).
Nokia Cries Foul on Rivals’ 800G Claims
"Carriers should expect 100-220 kilometer optical reach in most wave division multiplexing...
Daily Roundup: IBM Slashes Jobs
IBM slashed thousands of jobs; Juniper claimed wins over Cisco; and Nokia made moves on Open RAN.
Make Metadata Active Again
Metadata must move from laying dormant in a passive state and become active. Active metadata,...
7 Layers: IoT Part 1 — You, Me, and IoT
This week is the first in a two-part series on the Internet of Things. We answer: What is IoT? And...
Test your home network performance
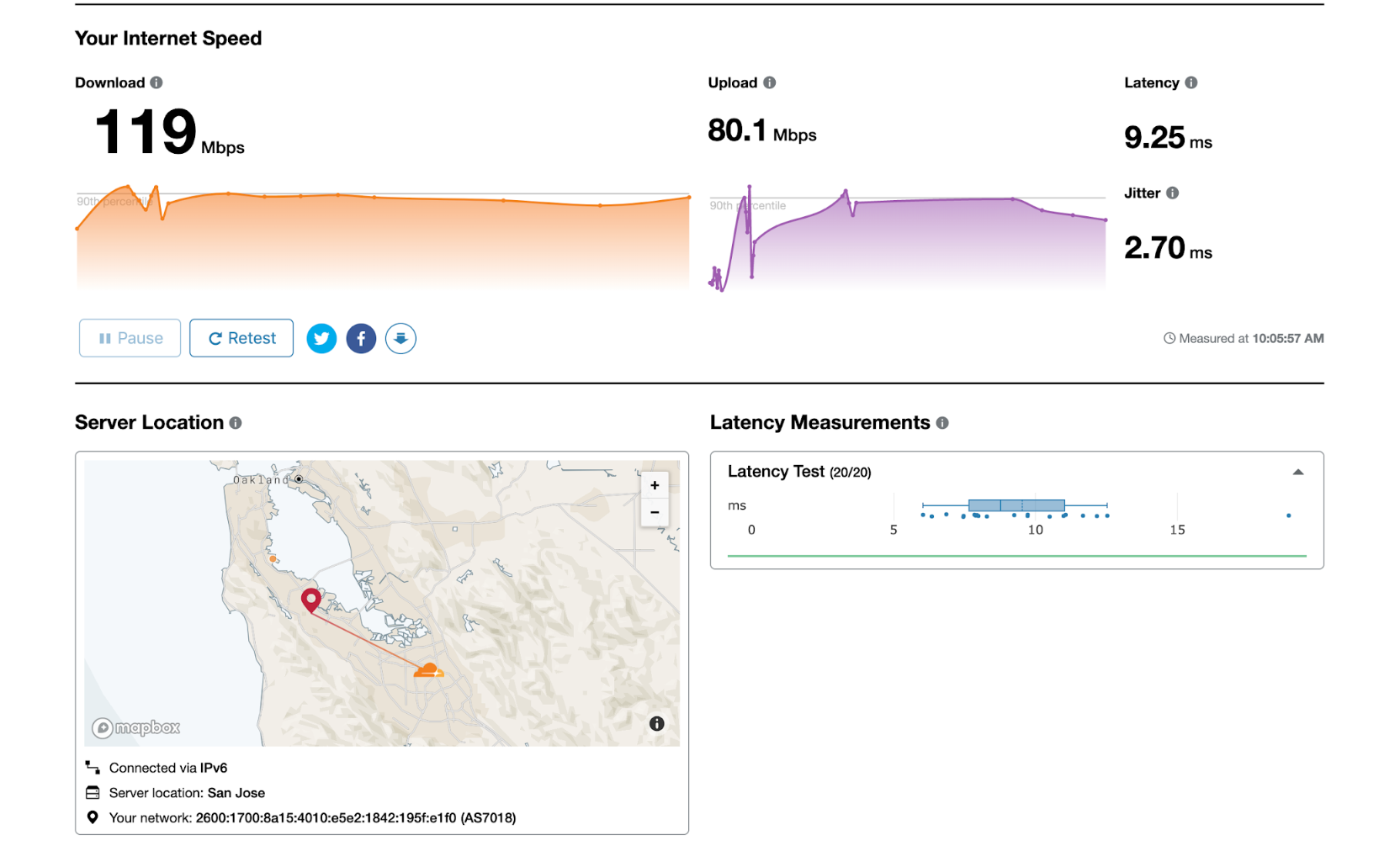
With many people being forced to work from home, there’s increased load on consumer ISPs. You may be asking yourself: how well is my ISP performing with even more traffic? Today we’re announcing the general availability of speed.cloudflare.com, a way to gain meaningful insights into exactly how well your network is performing.
We’ve seen a massive shift from users accessing the Internet from busy office districts to spread out urban areas.
Although there are a slew of speed testing tools out there, none of them give you precise insights into how they came to those measurements and how they map to real-world performance. With speed.cloudflare.com, we give you insights into what we’re measuring and how exactly we calculate the scores for your network connection. Best of all, you can easily download the measurements from right inside the tool if you’d like to perform your own analysis.
We also know you care about privacy. We believe that you should know what happens with the results generated by this tool. Many other tools sell the data to third parties. Cloudflare does not sell your data. Performance data is collected and anonymized and is governed by the terms of Continue reading
The History of LINX with Keith Mitchell
LINX is one of the first European Internet Exchanges created. Keith Mitchel joins the History of Networking to talk about the origins of LINX, and the important decisions that shaped it success and the IX community throughout Europe.
Is Nokia Serious About Open RAN?
Nokia continues to stand out in supporting open RAN efforts by joining more collaborative bodies...
IBM Reportedly Cuts Thousands of Jobs
The cuts, which were first reported by Bloomberg, are tied to the ongoing coronavirus pandemic.
Akamai Puts Script Attacks in Its Crosshairs
“The evolution of web applications has not gone unnoticed by attackers, and web defenders...
SNMP is still dominant

Sad but true.
The post SNMP is still dominant appeared first on EtherealMind.
Webinars in June 2020
Here’s the final push before we hit the summer break at the end of June (and recover a bit from the relentless production of new content we had throughout the first half of 2020):
- I finished the Introduction to Containers and Docker update just in time to cover the nuances of Docker Networking before the summer break. The first live session will take place today, the second one on June 11th.
- Later this week (May 28th) we’ll have some fun with routing protocol basics.
- Dinesh Dutt covered Vagrant in his last live session and plans to cover other network simulation tools on June 2nd.
- We did a “should I use VMware NSX or Cisco ACI” webinar a few years ago. In the meantime both vendors launched major new features, so it’s high time for a thorough refresh starting on June 9th.
- Mario Rosi will continue the Cisco ACI Introduction series on June 16th.
- David Barroso described the basics of Nornir in our network automation course. We’ll turn that material into an independent webinar (available with standard ipSpace.net subscription) and David plans to augment it with a deep dive into Nornir internals in a live session on Continue reading
Ruminating on SOS
Many years ago I attended a presentation by Dave Meyers on network complexity—which set off an entire line of thinking about how we build networks that are just too complex. While it might be interesting to dive into our motivations for building networks that are just too complex, I starting thinking about how to classify and understand the complexity I was seeing in all the networks I touched. Of course, my primary interest is in how to build networks that are less complex, rather than just understanding complexity…
This led me to do a lot of reading, write some drafts, and then write a book. During this process, I ended coining what I call the complexity triad—State, Optimization, and Surface. If you read the book on complexity, you can see my views on what the triad consisted of changed through in the writing—I started out with volume (of state), speed (of state), and optimization. Somehow, though, interaction surfaces need to play a role in the complexity puzzle.
First, you create interaction surface when you modularize anything—and you modularize to control state (the scope to set apart failure domains, the speed and volume to enable scaling). Second, adding interaction surfaces Continue reading
The Week in Internet News: Hong Kong Residents Flock to VPNs

Surveillance is coming: Hong Kong residents are rushing to download virtual private network apps after the Chinese government announced it intends to pass a new national security law covering the region, the South China Morning Post reports. Residents are worried that the Chinese government will restrict Internet access and put new surveillance measures in place in the quasi-independent region.
Fastest Internet ever: A team of researchers in Australia has logged data speeds of a blazing 44.2 terabits per second, claiming the fastest Internet speeds ever, the BBC reports. Researchers set the new record speed by using a device that replaces around 80 lasers found in some existing telecom hardware with a single piece of equipment called a “micro-comb.”
AI vs. coronavirus: Chinese ride-hailing provider Didi Chuxing says it will start using artificial intelligence to verify if drivers in its Latin American markets wear masks and disinfect cars to keep riders safe during the coronavirus pandemic, Al Jazeera says. Beginning on May 22, Didi’s drivers in Latin America needed to take a selfie with mask on to pass the AI verification, and starring in June they will need to report their body temperature to the phone app and upload Continue reading
Network Break 285: 37,000 Kilometers Of Undersea Cable Coming To Africa; Cisco Announces ACI 5.0
Lots to cover in this week's Network Break podcast, including a consortium of telcos and Facebook laying new undersea cable in Africa, new features for service providers and enterprises in Cisco's ACI 5.0, why Intel bought Rivet Networks, software and Wi-Fi for contact tracing, AT&T getting called on misleading 5G advertising, and more.
The post Network Break 285: 37,000 Kilometers Of Undersea Cable Coming To Africa; Cisco Announces ACI 5.0 appeared first on Packet Pushers.