Full Stack Journey 042: How An IT Specialist Chooses Adjacent Competencies
David Klee is a SQL database expert, but he's also knowledgeable about virtualization, networking, and infrastructure. In today's Full Stack Journey podcast, host Scott Lowe talks with David about how and why IT specialists should be competent in other disciplines, how to decide which areas to branch out into, and how adjacent competencies enrich can enrich your specialization.
The post Full Stack Journey 042: How An IT Specialist Chooses Adjacent Competencies appeared first on Packet Pushers.
Full Stack Journey 042: How An IT Specialist Chooses Adjacent Competencies
David Klee is a SQL database expert, but he's also knowledgeable about virtualization, networking, and infrastructure. In today's Full Stack Journey podcast, host Scott Lowe talks with David about how and why IT specialists should be competent in other disciplines, how to decide which areas to branch out into, and how adjacent competencies enrich can enrich your specialization.Resolve internal hostnames with Cloudflare for Teams
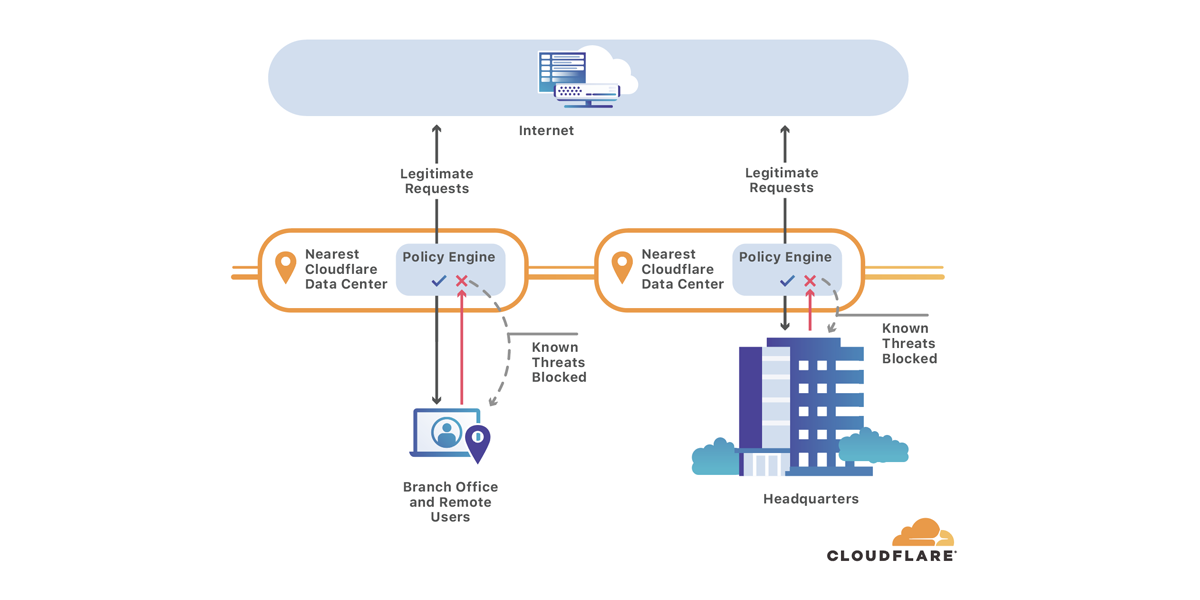
Phishing attacks begin like any other visit to a site on the Internet. A user opens a suspicious link from an email, and their DNS resolver looks up the hostname, then connects the user to the origin.
Cloudflare Gateway’s secure DNS blocks threats like this by checking every hostname query against a constantly-evolving list of known threats on the Internet. Instead of sending the user to the malicious host, Gateway stops the site from resolving. The user sees a “blocked domain” page instead of the malicious site itself.
As teams migrate to SaaS applications and zero-trust solutions, they rely more on the public Internet to do their jobs. Gateway's security works like a bouncer, keeping users safe as they navigate the Internet. However, some organizations still need to send traffic to internal destinations for testing or as a way to make the migration more seamless.
Starting today, you can use Cloudflare Gateway to direct end user traffic to a different IP than the one they originally requested. Administrators can build rules to override the address that would be returned by a resolver and send traffic to a specified alternative.
Like the security features of Cloudflare Gateway, the redirect function is Continue reading
Musings on IP Packet Reordering
During the Comparing Transparent Bridging and IP Routing part of How Networks Really Work webinar I said something along the lines of:
While packets should never be reordered in transit in transparent bridging, there’s no such guarantee in IP networks, and IP applications should tolerate out-of-order packets.
One of my regular readers who designs and builds networks supporting VoIP applications disagreed with that citing numerous real-life examples.
Of course he was right, but let’s get the facts straight first:
Starship Prompt Install and Configure
Install and configure the Starship prompt.Calico Enterprise 3.0 with Calico Multi-Cluster Management
As our enterprise customers build out large, multi-cluster Kubernetes environments, they are encountering an entirely new set of security challenges, requiring solutions that operate at scale and can be deployed both on-premises and across multiple clouds.
Today we are thrilled to announce the release of Calico Enterprise 3.0 and the availability of Calico Multi-Cluster Management, a game-changing solution that provides centralized management for network security across every Kubernetes cluster in your organization.
Calico Multi-Cluster Management
Calico Multi-Cluster Management provides a centralized management plane and single point of control for multi-cluster and multi-cloud environments. Calico Enterprise’s centralized control simplifies and speeds routine maintenance, leaving more time for your platform team to address other important tasks.
For example, instead of logging in to 50 clusters one-at-a-time to make a policy change, with a single log-in to Calico Enterprise you can apply policy changes consistently across all 50 clusters. You can also automatically apply existing network security controls to new clusters as they are added.

Calico Multi-Cluster Management includes centralized log management, troubleshooting with Flow Visualizer, and cluster-wide IDS (intrusion detection). It also provides compliance reporting, and alerts on non-compliance and indicators of compromise. Alerts are sent to SIEMs, including Splunk and Continue reading
Learning from the Post-Mortem
Post-mortem reviews seem to be quite common in the software engineering and application development sides of the IT world—but I do not recall a lot of post-mortems in network engineering across my 30 years. This puzzling observation sprang to mind while I was reading a post over at the ACM this last week about how to effectively learn from the post-mortem exercise.
The common pattern seems to be setting aside a one hour meeting, inviting a lot of people, trying to shift blame while not actually saying you are shifting blame (because we are all supposed to live in a blame-free environment now—fix the problem, not the blame!), and then … a list is created on a whiteboard, pictures are taken, and everyone walks away with a rock-solid plan to never do that again.
In a few months’ time, the same team will be in the same room, draw the same drawings, and say the same things all over again. At least that is the way it seems to me. If there is an effective post-mortem process in use by a company someplace, I do not think I have seen it.
From the article—
Are We Ready to Work from Home in the Middle East?

Even before COVID-19, political and economic scenes within the MENA region were changing. Differences across economies, politics, religion, and even the weather kept governments occupied.
Amid all that, the region has been shaken by COVID-19 as nations have moved operations into the home.
Looking at this from a technology perspective, we must ask ourselves: Are we ready for this? Are we able to transfer all our businesses and schools to our homes? Do we have an adequate Internet-based economy and good quality connectivity to back up the huge demand?
There’s no question that the Internet provides significant economic and social benefits. COVID-19 has made that especially clear. For many parts of the world, it has allowed us to carry on. But for the first time, governments have had to face the reality that there is no time for pilot projects. This is happening and it is happening now.
COVID-19 has opened the world’s eyes to how critical the Internet is for the economy. How can the Middle East build on what COVID-19 has taught us about the Internet and connectivity? The Internet Society has released two papers that can help develop the answers: “Middle East & North Africa Internet Continue reading
Build an OpenStack/Ceph cluster with Cumulus Networks in GNS3: part 2
Adding virtual machine images to GNS3
I’m going to assume that at this stage, you’ve got a fully working (and tested) GNS3 install on a suitably powerful Linux host. Once that is complete, the next step is to download the two virtual machine images we discussed in part 1 of this blog, and integrate them into GNS3.
In my setup, I downloaded the Cumulus VX 4.0 QCOW2 image (though you are welcome to try newer releases which should work), which you can obtain by visiting this link: https://cumulusnetworks.com/accounts/login/?next=/products/cumulus-vx/download/
I also downloaded the Ubuntu Server 18.04.4 QCOW2 image from here: https://cloud-images.ubuntu.com/bionic/current/bionic-server-cloudimg-amd64.img
Once you have downloaded these two images, the next task is to integrate them into GNS3. To do this:
- Select Edit > Preferences in the GNS3 interface.
- When the Preferences dialog pops up, from the left pane select QEMU VMs, then click New.
- Enter a name for the Image (e.g. Cumulus VM 4.0)
- Select the Qemu binary, and specify default RAM size for each instance (I used 1024MB). You can override this for each VM you create on the GNS3 canvas, so don’t worry too much about it.
- Select the Continue reading
Network Break 284: Dell Technologies Announces SONiC Distro; Microsoft Acquires Metaswitch Networks
Today's Network Break asks if enterprises want a supported SONiC network OS, Microsoft acquires Metaswitch Networks, VMware buys Kubernetes security platform Octarine, Cisco announces quarterly results, and more tech news.Network Break 284: Dell Technologies Announces SONiC Distro; Microsoft Acquires Metaswitch Networks
Today's Network Break asks if enterprises want a supported SONiC network OS, Microsoft acquires Metaswitch Networks, VMware buys Kubernetes security platform Octarine, Cisco announces quarterly results, and more tech news.
The post Network Break 284: Dell Technologies Announces SONiC Distro; Microsoft Acquires Metaswitch Networks appeared first on Packet Pushers.
The Week in Internet News: COVID-19 Tracing Creates Opportunities, Raises Concerns

Electronic doorman: In many restaurants, offices, and other locations in China, visitors must now show their COVID-19 risk status through a phone app before they are allowed entry, reports Agence-France Presse on Yahoo News. “A green light lets you in anywhere. A yellow light could send you into home confinement. The dreaded red light throws a person into a strict two-week quarantine at a hotel.” This use of contact tracing is raising privacy alarms in other countries.
Conflicting apps: Meanwhile, the Australian government’s new COVID-19 tracing app may interfere with Bluetooth-connected medical devices, including those used by people with diabetes, the Sydney Morning Herald reports. Diabetes Australia has warned users of continuous glucose monitoring apps that there may be connection problems.
Keeping track of yourself: In Japan, a 16-year-old student has designed an app that allows users to keep track of their whereabouts on their mobile phones, to help with contact tracing, The Associated Press reports on Japan Times. If a user is diagnosed with COVID-19, the Asiato app can tell them where they’ve been in recent weeks. This allows users to reach out to people they may have infected or to inform health authorities.
A digital human touch: Continue reading
DeepLinks and ScrollAnchor
What are DeepLinks?

To directly quote Wikipedia:
“Deep linking is the use of a hyperlink that links to a specific, generally searchable or indexed, piece of web content on a website (e.g. http://example.com/path/page), rather than the website's home page (e.g., http://example.com). The URL contains all the information needed to point to a particular item.”
Why DeepLinks in Dashboard?
There are many user experiences in Cloudflare’s Dashboard that are enhanced by the use of deep linking, such as:
- We’re able to direct users from marketing pages directly into the Dashboard so they can interact with new/changed features.
- Troubleshooting docs can have clearer, more intently directions. e.g. “Enable SSL encryption here” vs “Log into the Dashboard, choose your account and zone, navigate to the security tab, change SSL encryption level, blah blah blah”.
One of the interesting challenges with deep linking in the Dashboard is that most interesting resources are “locked” behind the context of an account and a zone/domain/website. To illustrate this, look at a tree of possible URL paths into Cloudflare’s Dashboard:
dash.cloudflare.com/ -> root-level resources: login, sign-up, forgot-password, two-factor
dash.cloudflare.com/<accountId>/ -> account-level resources: analytics, workers, Continue readingOpinion: Facebook Buys Giphy

Giphy is in places that Facebook isn't, so its competitive data
The post Opinion: Facebook Buys Giphy appeared first on EtherealMind.
Intent-Based Networking: Another Victim of Sturgeon’s Law
A few days ago Greg Ferro published an interesting post claiming DHCP is an example of intent-based networking (a bit less tongue-in-cheek than my “so is OSPF configuration” rant from 2017). BTW, so is RADIUS or TACACS+ ;)
He got quickly “corrected” by Phil Gervasi who loosely relied on Gartner’s definition of Intent-Based Networking, and claimed that an intent-based networking system should have three major components:
GNMI. Part 2. Decoding Protobuf messages with Python.
Hello my friend,
In the previous blogpost we started the discussion about the gNMI/Protobof approach to network automation by creating the Protobuf message. Today we continue it showing read the Protobuf messages.
2
3
4
5
retrieval system, or transmitted in any form or by any
means, electronic, mechanical or photocopying, recording,
or otherwise, for commercial purposes without the
prior permission of the author.
Network automation training – self-paced and live online
Network automation is a must-have technology set in all the industries these days. It is no more the matter of innovation, it is a matter of normal business operation. And we are happy to help you and your company with automation by providing the necessary holistic knowledge, skills and tools to make your automation journey successful:
At this training we teach you all the necessary concepts such as YANG data modelling, working with JSON/YAML/XML/Protobuf data formats, Linux administration basics, programming in Bash/Ansible/Python for multiple network operation systems including Cisco IOS XR, Nokia SR OS, Arista EOS and Cumulus Linux. All the most useful things such as NETCONF/RESTCONF, REST API, gNMI, OpenConfig and many others. Don’t miss Continue reading