Close to the Edge
PE-CE routing in MPLS L3VPN is an important topic which confuses a lot of people. Thanks to EVPN, it is now used not only in ISP but also DC networks.

Fundamentals of PE-CE routing
Usually either static routing or eBGP …
AWS Redirect URL with Route 53 and S3
How to redirect a URL using AWS Route 53 and S3.AWS Redirect URL with Route 53 and S3
I previously hosted my domains with GoDaddy. In their service it was pretty trivial to redirect a URL from one domain to another. I own the domain bradleysearle.com and I redirect it to https://codingpackets.com/about. The process to do this is not as simple with AWS so in this post I...Nvidia, Digital Realty Team Up on Enterprise AI
The new Data Hub product gives enterprises access to Nvidia’s AI infrastructure inside Digital...
Daily Roundup: Nutanix Furloughs CA Workforce
Nutanix furloughed 25% of its workforce; IBM targeted 5G and edge deployments; and Microsoft Azure...
Oracle Claims It Will Beat Salesforce at Cloud CRM
Much of that poise relies on the success of Oracle’s Gen 2 Cloud, a bare metal framework that it...
NVIDIA, Mellanox, and Cumulus
Recent press releases, Riding a Cloud: NVIDIA Acquires Network-Software Trailblazer Cumulus and NVIDIA Completes Acquisition of Mellanox, Creating Major Force Driving Next-Gen Data Centers, describe NVIDIA's moves to provide high speed data center networks to connect compute clusters that use of their GPUs to accelerate big data workloads, including: deep learning, climate modeling, animation, data visualization, physics, molecular dynamics etc.Real-time visibility into compute, network, and GPU infrastructure is required manage and optimize the unified infrastructure. This article explores how the industry standard sFlow technology supported by all three vendors can deliver comprehensive visibility.
Cumulus Linux simplifies operations, providing the same operating system, Linux, that runs on the servers. Cumulus Networks and Mellanox have a long history of working with the Linux community to integrate support for switches. The latest Linux kernels now include native support for network ASICs, seamlessly integrating with standard Linux routing (FRR, Quagga, Bird, etc), configuration (Puppet, Chef, Ansible, etc) and monitoring (collectd, netstat, top, etc) tools.
Linux 4.11 kernel extends packet sampling support describes enhancements to the Linux kernel to support industry standard sFlow instrumentation in network ASICs. Cumulus Linux and Mellanox both support the new Linux APIs. Cumulus Linux uses the open source Continue reading
Midrange All-Flash Storage Market, Meet Dell EMC PowerStore
The new storage systems come with built-in vSphere integration enabling VMware virtualized...
Coalition Forms to Address Open RAN Policies
The Open RAN Policy Coalition has support from seven operators and 24 vendors, though it's...
Microsoft Azure Sentinel Powers Open Systems’ Threat Detection
Open Systems’ customers liked the Sentinel technology, but wanted the threat detection and...
Cinco de Mayo – What are we celebrating anyway?

Greetings from Latinflare, Cloudflare’s LatinX Employee Resource Group, with members all over the US, the UK, and Portugal. Today is Cinco de Mayo! Americans everywhere will be drinking margaritas and eating chips and salsa. But what is this Mexican holiday really about and what exactly are we celebrating?
About Cinco de Mayo
Cinco de Mayo, Spanish for "Fifth of May", is an annual celebration held in Mexico on May 5th. The date is observed to commemorate the Mexican Army's victory over the French Empire at the Battle of Puebla, on May 5, 1862, under the leadership of General Ignacio Zaragoza. The victory of the smaller Mexican force against a larger French force was a boost to morale for the Mexicans. Zaragoza died months after the battle due to illness. A year after the battle, a larger French force defeated the Mexican army at the Second Battle of Puebla, and Mexico City soon fell to the invaders.
In the United States, Cinco de Mayo has taken on a significance beyond that in Mexico. More popularly celebrated in the United States than Mexico, the date has become associated with the celebration of Continue reading
Automate file uploads to your Cisco Nexus switches

If you have more than three Cisco Nexus switches in nx-os mode, and you are not using Cisco DCNM or any other similar tool, you probably already have encountered this question: How to automate file uploads to your Cisco Nexus switches? Here is a turnkey Python script using Netmiko’s SCP function to do this. This script is very simple, it relies only on Netmiko functions and SCP. But it does its job very well and I share it here because it can certainly help you to save time. What…
The post Automate file uploads to your Cisco Nexus switches appeared first on AboutNetworks.net.
Former Check Point Execs Score $20M for Orca Security
With the Series A round, in addition to $6.5 million in seed funding, Orca plans to double its team...
Setting up Cloudflare for Teams as a Start-Up Business
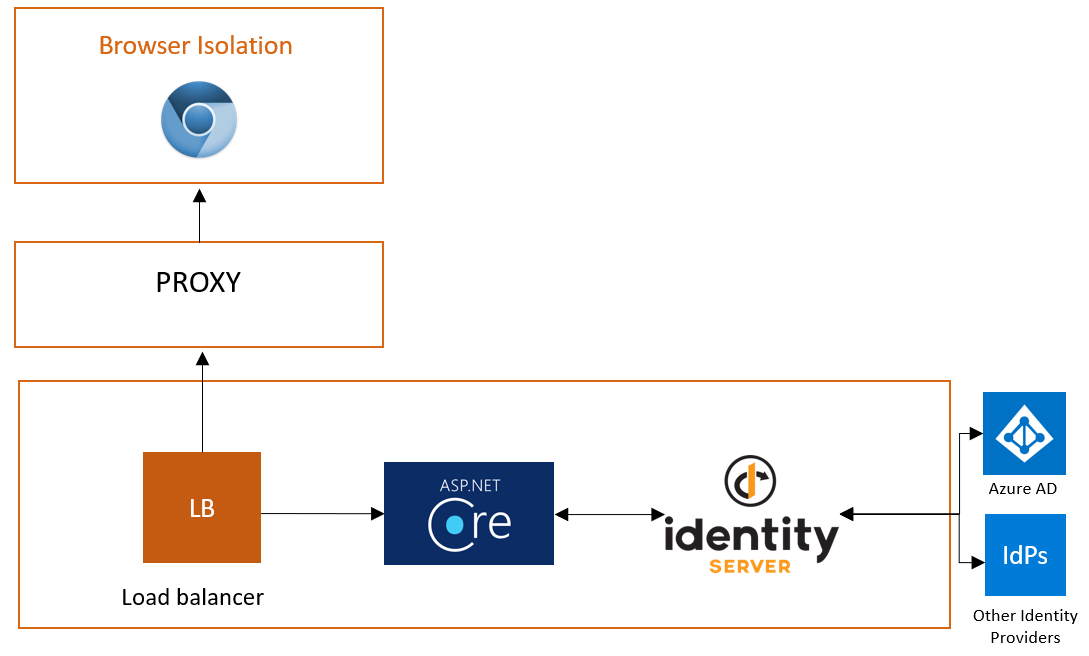
Earlier this year, Cloudflare acquired S2 Systems. We were a start-up in Kirkland, Washington and now we are home to Cloudflare’s Seattle-area office.
Our team developed a new approach to remote browser isolation (RBI), a technology that runs your web browser in a cloud data center, stopping threats on the Internet from executing any code on your machine. The closer we can bring that data center to the user, the faster we can make that experience. Since the acquisition, we have been focused on running our RBI platform in every one of Cloudflare’s data centers in 200 cities around the world.
The RBI solution will join a product suite that we call Cloudflare for Teams, which consists of two products: Access and Gateway.
Those two products solve a number of problems that companies have with securing users, devices, and data. As a start-up, we struggled with a few of these challenges in really painful ways:
- How do we let prospects securely trial our RBI platform?
- How do we keep our small office secure without an IT staff?
- How can we connect to the powerful, but physically clunky and heavy development machines, when we are not in that office?
Dogfooding Continue reading
Dictionary: fauxpology

Define fauxpology
The post Dictionary: fauxpology appeared first on EtherealMind.
