Getting Started with Cluster API using Docker
Cluster API (CAPI) is a relatively new project aimed at deploying Kubernetes clusters using a declarative API (think YAML). The official documentation (a.k.a. the Cluster API book), does a very good job explaining the main concepts and goals of the project. I always find that one of the best ways to explore new technology is to see how it works locally, on my laptop, and Cluster API has a special “Docker” infrastructure provider (CAPD) specifically for that. However, the official documentation for how to setup a docker managed cluster is very poor and fractured. In this post, I’ll try to demonstrate the complete journey to deploy a single CAPI-managed k8s cluster and provide some explanation of what happens behind the scene so that its easier to troubleshoot when things go wrong.
Prerequisites
Two things must be pre-installed before we can start building our test clusters:
- kind - a tool to setup k8s clusters in docker containers, it will be used as a management (a.k.a. bootstrap) cluster.
- clusterctl - a command line tool to interact with the management cluster.
We’re gonna need run a few scripts from the Cluster API Github repo, so let’s get a copy Continue reading
Heavy Networking 515: A Decade of Network Podcasting
In this brief chat, Ethan & Greg discuss where we came from and where we are going. Note the retro music we used and check out outtro too.
The post Heavy Networking 515: A Decade of Network Podcasting appeared first on Packet Pushers.
Heavy Networking 515: A Decade of Network Podcasting
In this brief chat, Ethan & Greg discuss where we came from and where we are going. Note the retro music we used and check out outtro too.CloudGenix Key to Palo Alto Networks SASE Play
Palo Alto networks purchased CloudGenix at the end of March for $420 million in a bid to bolster...
Our Work to Make the Internet for Everyone Marches On

Over the past several months the Internet Society has been working on a transaction to sell Public Interest Registry (PIR), operator of .ORG and other top-level domains, to Ethos Capital. Under PIR’s registry agreements, the Internet Corporation for Assigned Names and Numbers (ICANN) had to consent to this indirect change of control. ICANN has now announced that it does not consent to the transaction.
I am, of course, disappointed by ICANN’s decision, though I am pleased it was finally reached. ICANN took much longer than it should have done to vote on the transaction. In my view, ICANN stepped outside its remit by acting as a regulator it was never intended to be. What began as a routine change of indirect control – the type ICANN has expeditiously approved on multiple occasions in the past – resulted in months and months of review and analysis. The outcome does not seem consistent with ICANN’s prior decisions in similar cases. It should concern the Internet community that ICANN has shown itself to be much more susceptible to political pressure than its limited mandate would recommend.
Nevertheless, ICANN has now rendered a clear decision. This brings to a close a period Continue reading
Daily Roundup: AWS Q1 Tops $10B Revenue
AWS topped $10 billion in Q1; Cisco squashed yet another SD-WAN bug; and Fortinet CISO talked...
Verizon Virtualization Efforts Vanquished COVID-19 Chaos
“If we hadn't done virtualization, this would have been a multi-week, multi-month effort to bring...
Cisco Squashes Yet Another SD-WAN Bug
While Cisco says it is not aware of any malicious use of the vulnerability, with 20,000 customers...
AWS Revenue Tops $10B in Q1, Bezos Pledges Q2 Profit on COVID-19 Spend
Amazon CEO Jeff Bezos said that the company will spend $4 billion or more — all of its expected...
Heavy Networking 514: Aruba’s Vision Extends From The Data Center To The Edge (Sponsored)
On today's sponsored Heavy Networking we talk about building a unified network infrastructure with Aruba. Best known for wireless, Aruba also has a portfolio of data center and campus switches, SD-WAN, and an access control and policy enforcement system to bring it all together. Our guests are Keerti Melkote, Aruba President and Founder; and Michael Dickman, Senior Vice President and GM of Switching.Heavy Networking 514: Aruba’s Vision Extends From The Data Center To The Edge (Sponsored)
On today's sponsored Heavy Networking we talk about building a unified network infrastructure with Aruba. Best known for wireless, Aruba also has a portfolio of data center and campus switches, SD-WAN, and an access control and policy enforcement system to bring it all together. Our guests are Keerti Melkote, Aruba President and Founder; and Michael Dickman, Senior Vice President and GM of Switching.
The post Heavy Networking 514: Aruba’s Vision Extends From The Data Center To The Edge (Sponsored) appeared first on Packet Pushers.
DNS over email or twitter – Cloudflare Resolver

It could be useful for certain field work
The post DNS over email or twitter – Cloudflare Resolver appeared first on EtherealMind.
Nominations Open! Jonathan B. Postel Service Award 2020

Do you know someone who has made an outstanding contribution to Internet development?
Nominate them for this year’s Jonathan B. Postel Service Award!
Each year, the Internet Society presents the prestigious award to an individual or organization that, like Jon Postel, has made significant contributions to the technological development of the Internet.
The award commemorates Jon Postel’s extraordinary stewardship in the course of his 30-year career in networking.
The chosen candidate will be presented with a USD20,000 honorarium and the signature crystal engraved globe at a global conference with Internet technical leaders later this year.
Previous award winners include Steven Huter for fostering local Internet communities globally, Kimberly Claffy for her contribution to Internet measurement, Kanchana Kanchanasut for accelerating Internet development in Thailand, and Nii Quaynor for driving the spread of the Internet across Africa.
Special emphasis is placed on candidates who have supported and enabled others in addition to their own contributions.
Help us recognize the extraordinary people who have committed themselves to the technological development, growth, and strength of the Internet!
Nomination period ends on 5 June 2020. For questions, email [email protected].
Image of Community Network Champions ©Atul Loke/Panos Pictures for the Internet Society.
How Rakuten Mobile Overcame First-of-its-Kind Network Challenges
“You need to be the owner of your own destiny and this disaggregation strategy needs to be looked...
Failure Is Fine, Learning Is Mandatory

“Failure is a harsh teacher because it gives the test first and the lesson afterward.” — Vernon Law
I’m seeing a thread going around on Twitter today that is encouraging people to share their stories of failure in their career. Maybe it was a time they created a security hole in a huge application. Perhaps it was creating a routing loop in a global corporation. Or maybe it was something as simple as getting confused about two mailboxes and deleting the wrong one and realizing your mail platform doesn’t have undelete functionality.
We fail all the time. We try our hardest and whatever happens isn’t what we want. Some of those that fail just give up and assume that juggling isn’t for them or that they can never do a handstand. Others keep persevering through the pain and challenge and eventually succeed because they learn what they need to know in order to complete their tasks. Failure is common.
What is different is how we process the learning. Some people repeat the same mistakes over and over again because they never learn from them. In a professional setting, toggling the wrong switch when you create someone’s new account has Continue reading
SDxCentral’s Top 10 Articles — April 2020
VMware claimed SD-WAN dominance over Cisco; Cisco SD-WAN struck back against VMware; and Nokia...
Weekly Wrap: Facebook, Cisco, Verizon Give Glimpse Into Future of Networks
SDxCentral Weekly Wrap for May 1, 2020: The ongoing COVID-19 outbreak is stressing networks;...
Now Is Not the Time to Put Everyone’s Security on the Line

This opinion piece was originally published in SC Magazine.
With social distancing the norm, we’re spending more time on the Internet doing more important things than ever – eg, working, learning, banking, trading, shopping, seeing the doctor and having family time – as well as streaming, gaming and interacting with our connected speakers.
Shouldn’t we be certain, especially now, that no one is eavesdropping, stealing or modifying our data?
Encryption is the primary means of accomplishing that goal. Using encryption, data is scrambled so that only the intended people can see the data. It’s right there under the covers most of the time when you’re on Wi-Fi, Bluetooth, 4G and browsing most websites.
Unfortunately, most online services today still do encryption in a piecemeal manner. Sections along the path are encrypted, but typically there are points along the way where the data is unencrypted and processed in some way before being re-encrypted and sent along.
The good news is that many messaging services – eg, WhatsApp, Telegram and Signal – offer end-to-end encryption, where only the sender and intended recipient can “see” the message. Everyone else along the path – even the company providing the service – can’t see inside. The Continue reading
When people pause the Internet goes quiet
Recent news about the Internet has mostly been about the great increase in usage as those workers who can have been told to work from home. I've written about this twice recently, first in early March and then last week look at how Internet use has risen to a new normal.
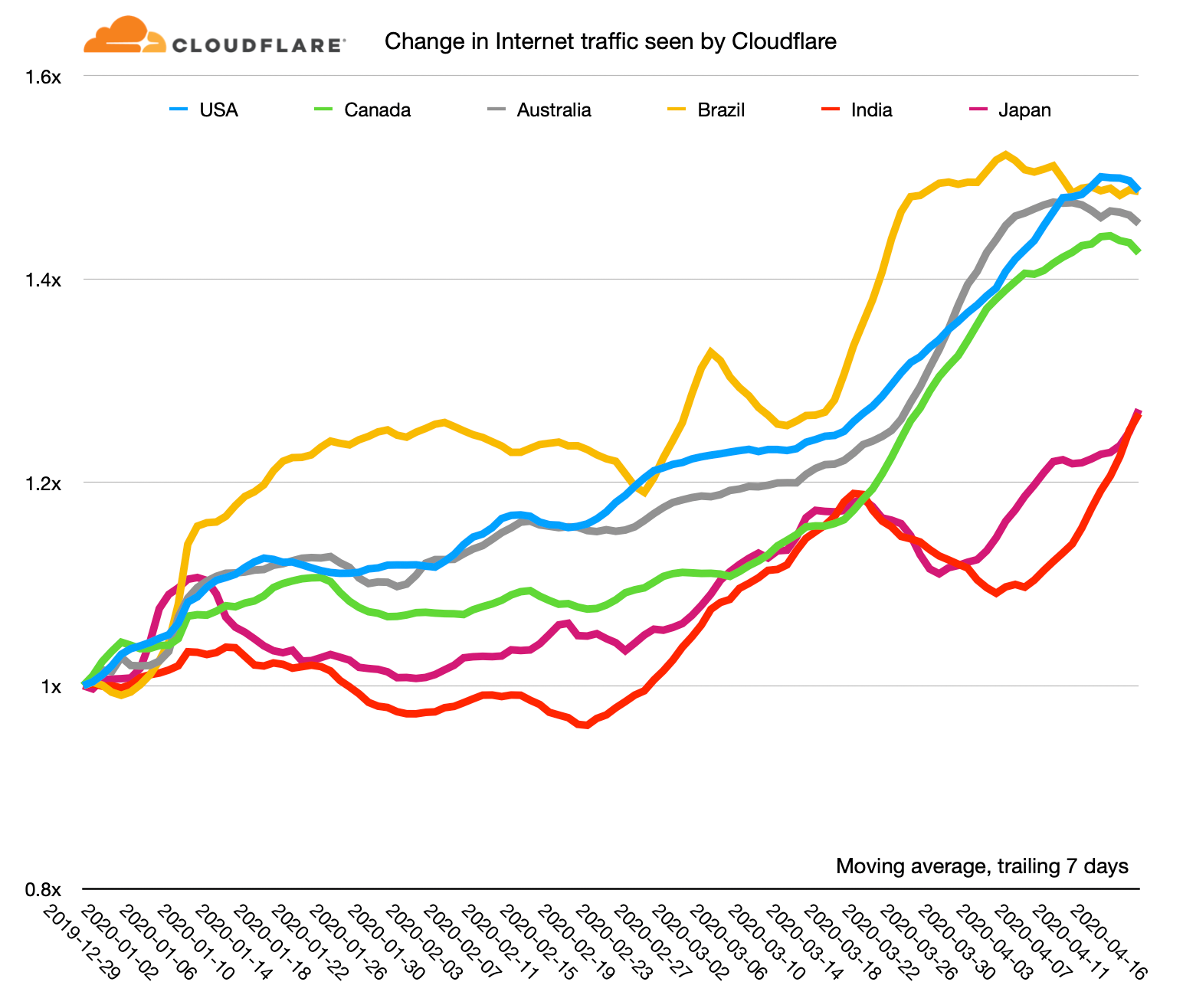
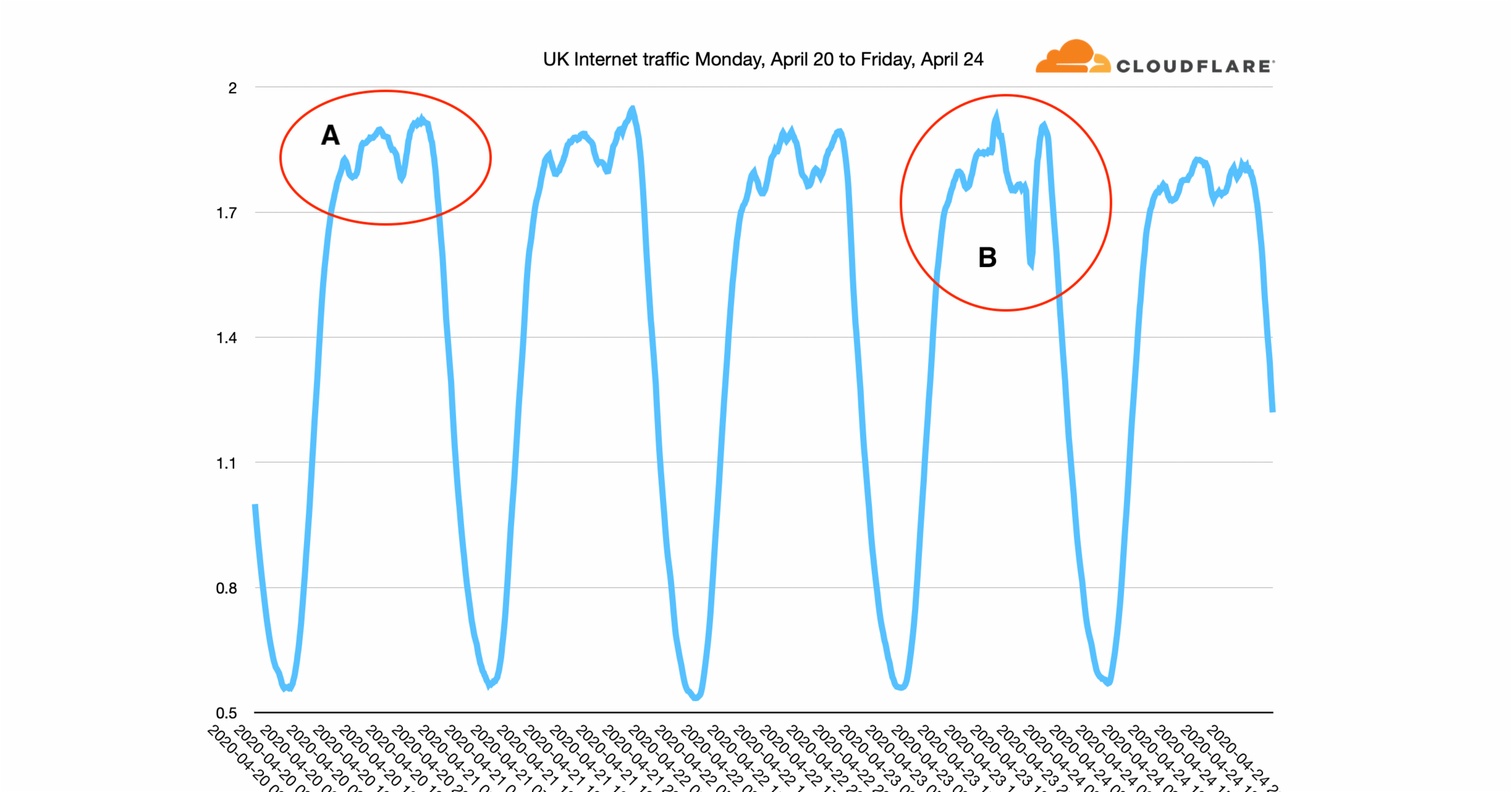
As human behaviour has changed in response to the pandemic, it's left a mark on the charts that network operators look at day in, day out to ensure that their networks are running correctly.
Most Internet traffic has a fairly simple rhythm to it. Here, for example, is daily traffic seen on the Amsterdam Internet Exchange. It's a pattern that's familiar to most network operators. People sleep at night, and there's a peak of usage in the early evening when people get home and perhaps stream a movie, or listen to music or use the web for things they couldn't do during the workday.
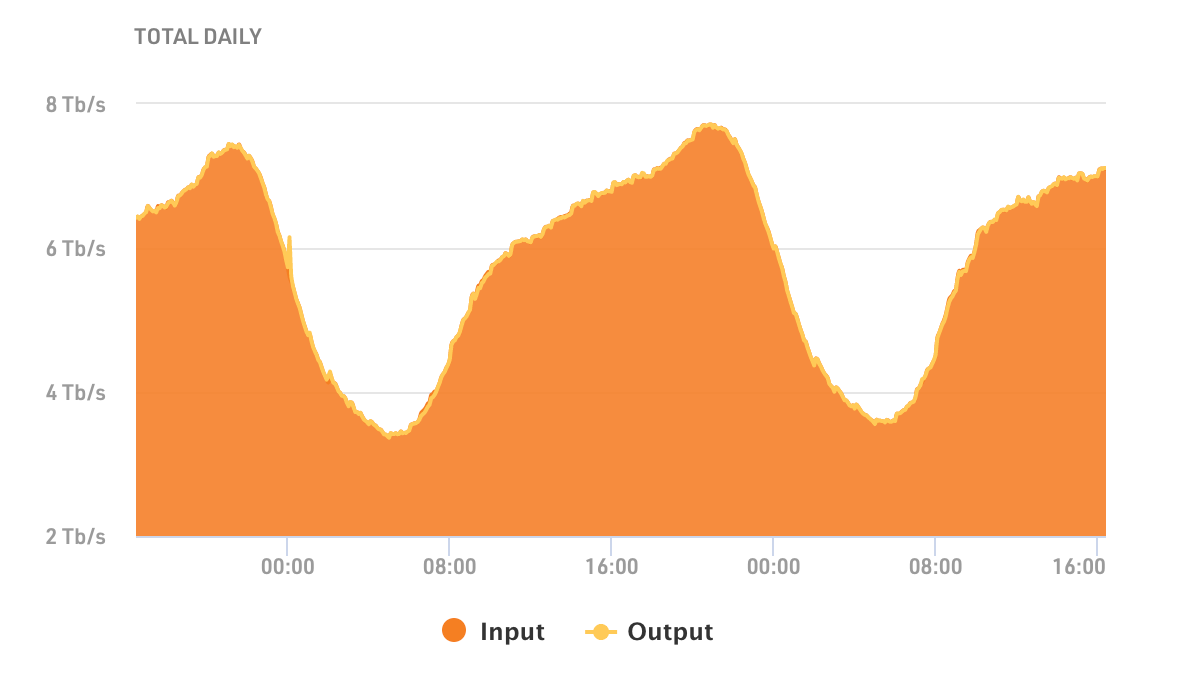
But sometimes that rhythm get broken. Recently we've seen the evening peak by joined by morning peaks as well. Here's a graph from the Milan Internet Exchange. There are three peaks: morning, afternoon and evening. These peaks seem to be caused by people working from Continue reading