From Python To Go 001. Get Started.
Dear friend,
As mentioned in previous blogpost, I’ve kicked the new series of blog posts related to Go (Golang programming language) and how to pick that up. Originally my idea was just to explain some concepts, pretty much I’ve done back in past with Code eXpress (CEX) for Python. But then I’ve thought through it further and decided to write a side-by-side guide with Python and Go together, exactly as I’ve done before with multi vendor network automation, when started writing about Nokia SR OS and Cisco IOS XR back in 2016.
Do I Need Both Python And Go?
In our opinion, yes, you do need both. Each of these programming languages shines in some areas more than another. And both of them are applicable to network and infrastructure automation. As such, we recommend to study both, but to start with Python as it is easier and at this stage is wider used than Go. So we encourage you to start with our Network Automation Trainings:
We offer the following training programs in network automation for you:
HN756: Alkira Enhances Its Multi-Cloud Networking With ZTNA and Security (Sponsored)
Alkira provides a Multi-Cloud Networking Service (MCNS) that lets you connect public cloud and on-prem locations using a cloud-delivered, as-a-service approach. But Alkira offers more than just multi-cloud connectivity. On today’s sponsored episode of Heavy Networking, we dig into Alkira’s full set of offerings, which include networking, visibility, governance, and security controls such as firewalls... Read more »TNO007: Good Foundations Are Key To Leveraging AI for Network Operations
In this episode of Total Network Operations the conversation focuses on the impact and implementation of AI on network operations. Host Scott Robohn is joined by guest Michael Wynston to discuss the foundational requirements for AI implementation, such as well-documented processes, version control, and lab testing. Michael also talks about the need for lifelong learning... Read more »Hedge 249: FR Routing Update
Alistair Woodman joins Tom and Russ to talk about the current state of the FR Routing open source routing stack project. Like all software projects, FR Routing has entered a bit of a “middle phase,” with a focus on maintenance and stability rather than new features and protocols.
download
Wake on LAN: Linux, Windows and Routers
Wake-on-LAN (WoL) is a feature that lets you turn on computers remotely. This can be […]
The post Wake on LAN: Linux, Windows and Routers first appeared on Brezular's Blog.
IPB163: Know Your Options: DHCP vs. DHCPv6
If you’re going to use DHCPv6, you have options, but there are some things you need to know in order to be able to build out your DHCPv6 configuration properly. Today’s IPv6 Buzz explores similarities and differences between DHCP and DHCPv6, particularly the operational model. And as always, you’ll want to verify and test before... Read more »Worth Reading: Creating a Tech Blog
Would you like to start a tech blog but don’t know how to do it? Ethan Banks put together a phenomenal how-to guide in his Developing Content & Gathering Research For Your Tech Blog article.
Oh, and please use Hugo (or similar) and use walled gardens like LinkedIn solely to post summaries and links to your content. You want to be in control and retain ownership of your work, right?
N4N001: Frames and Packets: What’s the Difference?
Frames and packets: how are they different and why is it important to know those differences? On this first episode of N Is For Networking, join co-hosts Holly Metlitzky and Ethan Banks to learn the fundamentals about frames and packets, plus some bonus material on layers and addresses. N Is For Networking is the newest... Read more »Workers Builds: integrated CI/CD built on the Workers platform
During 2024’s Birthday Week, we launched Workers Builds in open beta — an integrated Continuous Integration and Delivery (CI/CD) workflow you can use to build and deploy everything from full-stack applications built with the most popular frameworks to simple static websites onto the Workers platform. With Workers Builds, you can connect a GitHub or GitLab repository to a Worker, and Cloudflare will automatically build and deploy your changes each time you push a commit.
Workers Builds is intended to bridge the gap between the developer experiences for Workers and Pages, the latter of which launched with an integrated CI/CD system in 2020. As we continue to merge the experiences of Pages and Workers, we wanted to bring one of the best features of Pages to Workers: the ability to tie deployments to existing development workflows in GitHub and GitLab with minimal developer overhead.
In this post, we’re going to share how we built the Workers Builds system on Cloudflare’s Developer Platform, using Workers, Durable Objects, Hyperdrive, Workers Logs, and Smart Placement.
The core problem for Workers Builds is how to pick up a commit from GitHub or GitLab and start a Continue reading
Moving Baselime from AWS to Cloudflare: simpler architecture, improved performance, over 80% lower cloud costs
When Baselime joined Cloudflare in April 2024, our architecture had evolved to hundreds of AWS Lambda functions, dozens of databases, and just as many queues. We were drowning in complexity and our cloud costs were growing fast. We are now building Baselime and Workers Observability on Cloudflare and will save over 80% on our cloud compute bill. The estimated potential Cloudflare costs are for Baselime, which remains a stand-alone offering, and the estimate is based on the Workers Paid plan. Not only did we achieve huge cost savings, we also simplified our architecture and improved overall latency, scalability, and reliability.
Cost (daily) | Before (AWS) | After (Cloudflare) |
Compute | $650 - AWS Lambda | $25 - Cloudflare Workers |
CDN | $140 - Cloudfront | $0 - Free |
Data Stream + Analytics database | $1,150 - Kinesis Data Stream + EC2 | $300 - Workers Analytics Engine |
Total (daily) | $1,940 | $325 |
Total (annual) | $708,100 | $118,625 (83% cost reduction) |
Table 1: AWS vs. Workers Costs Comparison ($USD)
When we joined Cloudflare, we immediately saw a surge in usage, and within the first week following the announcement, we were processing over a billion events daily and our weekly active users tripled.
As the platform grew, so did the challenges Continue reading
Ethernet at NANOG 92
Ethernet has been the mainstay of much of the networking environment for almost 50 years now, but that doesn't mean that it’s remained unchanged over that period. The evolution of this technology has featured continual increases in the scale of Ethernet networks, increasing in capacity, reach and connections. I’d like to report on a couple of Ether-related presentations that took place at the recent NANOG 92 meeting, held in Toronto in October 2024 that described some recent developments in Ethernet.D2DO255: Is AI the Magic Solution for Refactoring Legacy Code?
AI is being integrated and adopted across much of the IT world, but can it work magic in transforming old legacy code into shiny modern code? When it comes to this magic trick, it’s important to look behind the curtain. On today’s Day Two DevOps podcast we discuss the reality of AI in refactoring code... Read more »DEEP: a Boutique Security Conference
Last week, I had the privilege of discussing Disaster Recovery Myths at the DEEP Conference. I also took the opportunity to attend several other presentations covering topics such as eBPF, open-source supply pipelines, tips for bug bounty hunters, and SSE.
TL&DR: I loved the experience ;)
Installing Certificate on ISE Lab Server
When ISE is installed, all the certificates used for different services such as EAP, Admin portal, etc., are self signed. Below is a short summary of the certificates that ISE uses:
- Admin – Authentication of the ISE admin portal (GUI).
- EAP Authentication – EAP protocols that use SSL/TLS tunneling.
- RADIUS DTLS – RADsec server (encrypted RADIUS).
- pxGrid – pxGrid controller.
- SAML – For SAML signing.
- Portal – For portals.
The certificates can be seen by going to Administration -> System -> Certificates:
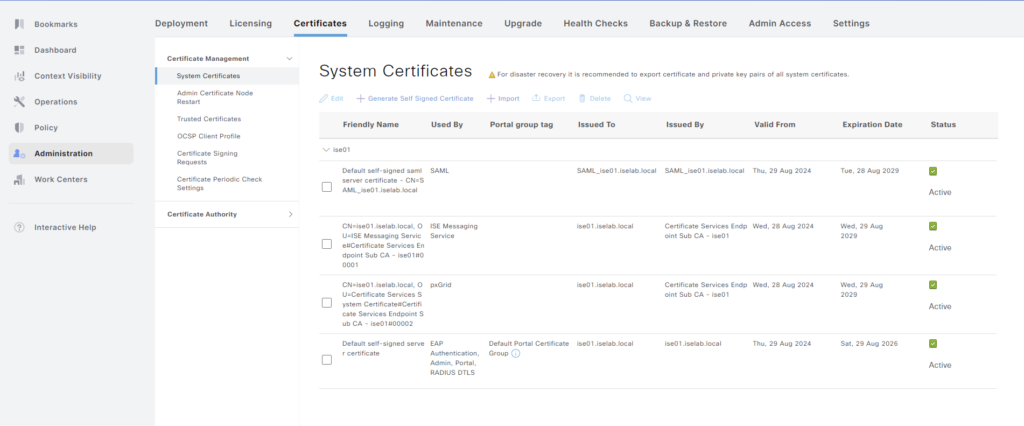
A certificate can be viewed by selecting the checkbox and clicking View:
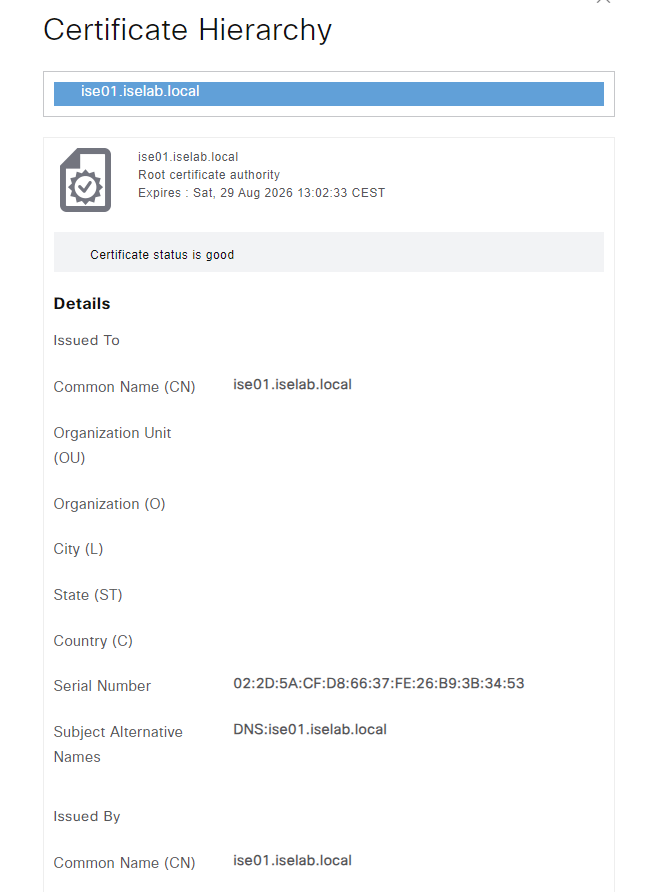
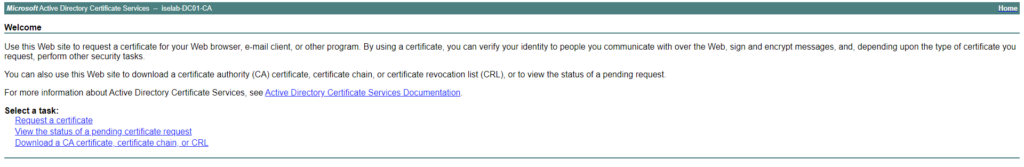
Self-signed certificates aren’t good. Certificates should be signed by a trusted CA. That could be a public root CA, or more commonly, especially for labs, an internal CA. Before such a certificate can be installed, ISE must be configured to trust that CA. This is done by importing the root CA certificate. I’ll download the certificate from the web service on the ADCS server. The web service is reachable on https:://<IP of ADCS server>/certsrv/. Click Download a CA certificate, certificate chain or CRL:
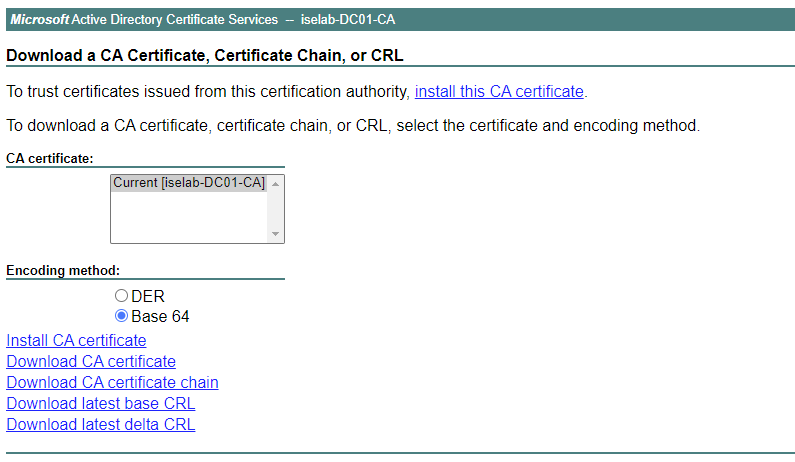
On the next page, change to Base 64 and then click Download CA certificate:
The file is downloaded Continue reading
Cloudflare’s perspective of the October 30 OVHcloud outage
On October 30, 2024, cloud hosting provider OVHcloud (AS16276) suffered a brief but significant outage. According to their incident report, the problem started at 13:23 UTC, and was described simply as “An incident is in progress on our backbone infrastructure.” OVHcloud noted that the incident ended 17 minutes later, at 13:40 UTC. As a major global cloud hosting provider, some customers use OVHcloud as an origin for sites delivered by Cloudflare — if a given content asset is not in our cache for a customer’s site, we retrieve the asset from OVHcloud.
We observed traffic starting to drop at 13:21 UTC, just ahead of the reported start time. By 13:28 UTC, it was approximately 95% lower than pre-incident levels. Recovery appeared to start at 13:31 UTC, and by 13:40 UTC, the reported end time of the incident, it had reached approximately 50% of pre-incident levels.

Traffic from OVHcloud (AS16276) to Cloudflare
Cloudflare generally exchanges most of our traffic with OVHcloud over peering links. However, as shown below, peered traffic volume during the incident fell significantly. It appears that some small amount of traffic briefly began to flow over transit links from Cloudflare to OVHcloud due to sudden Continue reading
HW039: Demystifying Private Mobile Networks
What is a private mobile network and how does it work? Guest Jeremy Rollinson, an expert in private cellular networks, joins host Keith Parsons to clarify misconceptions about private mobile networks, from terminology to spectrum allocations. They explore the differences between public and private networks, the evolution of private mobile networks, the importance of understanding... Read more »HS087: Alkira’s Multi-Cloud NaaS Bridges Networking and Security (Sponsored)
Startup Alkira has built a Network as a Service (NaaS) offering that extends from on prem to public cloud and multi-cloud. Today’s sponsored episode of Heavy Strategy digs in to Alkira’s capabilities in multi-cloud networking, security, automation, and cost transparency. Guest Manan Shah, SVP of Product at Alkira, explains how Alkira simplifies network management, enhances... Read more »PP037: From Supply Chain Security to Post-Quantum Cryptography – Live from XFD!
This episode was recorded live at Security Field Day (XFD) 12 in October, 2024. As delegates at the event, JJ and Drew heard presentations from DigiCert, Dell Technologies, SonicWall, and Citrix. These presentations covered topics including digital certificate management, post-quantum cryptography, supply chain security, recovering from ransomware, Zero Trust Network Access (ZTNA), and Secure Service... Read more »Migrating billions of records: moving our active DNS database while it’s in use
According to a survey done by W3Techs, as of October 2024, Cloudflare is used as an authoritative DNS provider by 14.5% of all websites. As an authoritative DNS provider, we are responsible for managing and serving all the DNS records for our clients’ domains. This means we have an enormous responsibility to provide the best service possible, starting at the data plane. As such, we are constantly investing in our infrastructure to ensure the reliability and performance of our systems.
DNS is often referred to as the phone book of the Internet, and is a key component of the Internet. If you have ever used a phone book, you know that they can become extremely large depending on the size of the physical area it covers. A zone file in DNS is no different from a phone book. It has a list of records that provide details about a domain, usually including critical information like what IP address(es) each hostname is associated with. For example:
example.com 59 IN A 198.51.100.0
blog.example.com 59 IN A 198.51.100.1
ask.example.com 59 IN A 198.51.100.2It is not unusual Continue reading
