Day Two Cloud 029: Kubernetes Needs To Disappear
This is a special holiday episode of Day Two Cloud with guest Kelsey Hightower, a Kubernetes evangelist and contributor. We discuss the current state of Kubernetes and the future for this orchestration platform, including how it will address networking, should you get certified, and will Kubernetes eventually fade into the background as hidden infrastructure you don't have to think about so much.
The post Day Two Cloud 029: Kubernetes Needs To Disappear appeared first on Packet Pushers.
Merry Christmas and Happy New Year 2020!
Dear friend,
The year 2019 is almost over and it is a time to sincerely thank you for the time you spend reading this blog, for all your questions, ideas and suggestions. All these things gives us inspiration to continue blogging about new things for you, dear friend!
We wish you jolly time over the holidays period with your families and friends. We wish you to achieve all your professional and personal goals in 2020! Let the year be successful for you and your loved ones!
Merry Christmas and Happy New 2020 Year!
BR, Anton
This holiday’s biggest online shopping day was… Black Friday
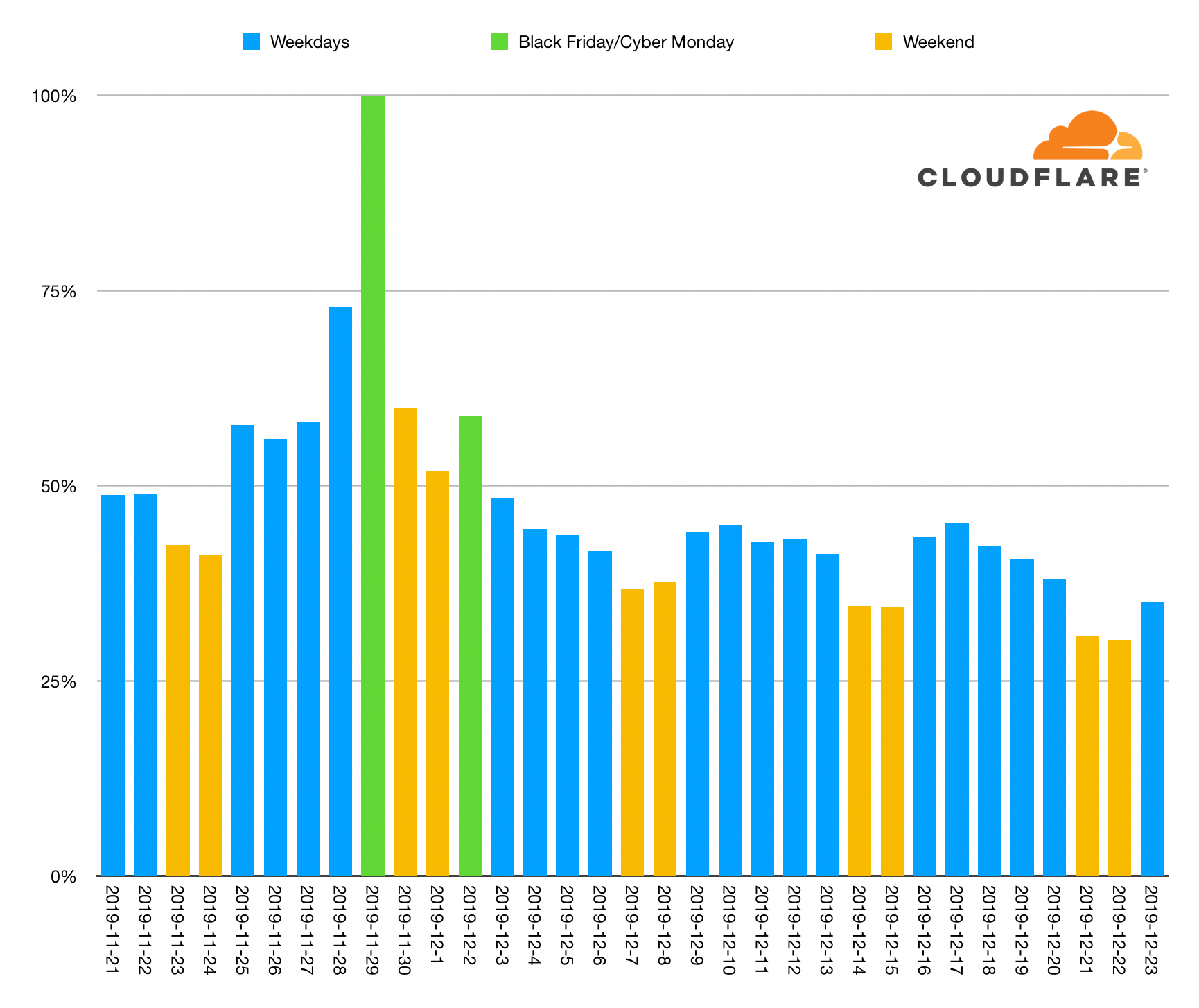
What’s the biggest day of the holiday season for holiday shopping? Black Friday, the day after US Thanksgiving, has been embraced globally as the day retail stores announce their sales. But it was believed that the following Monday, dubbed “Cyber Monday,” may be even bigger. Or, with the explosion of reliable 2-day and even 1-day shipping, maybe another day closer to Christmas has taken the crown. At Cloudflare, we aimed to answer this question for the 2019 holiday shopping season.
Black Friday was the biggest online shopping day but the second biggest wasn't Cyber Monday... it was Thanksgiving Day itself (the day before Black Friday!). Cyber Monday was the fourth biggest day.
Here's a look at checkout events seen across Cloudflare's network since before Thanksgiving in the US.
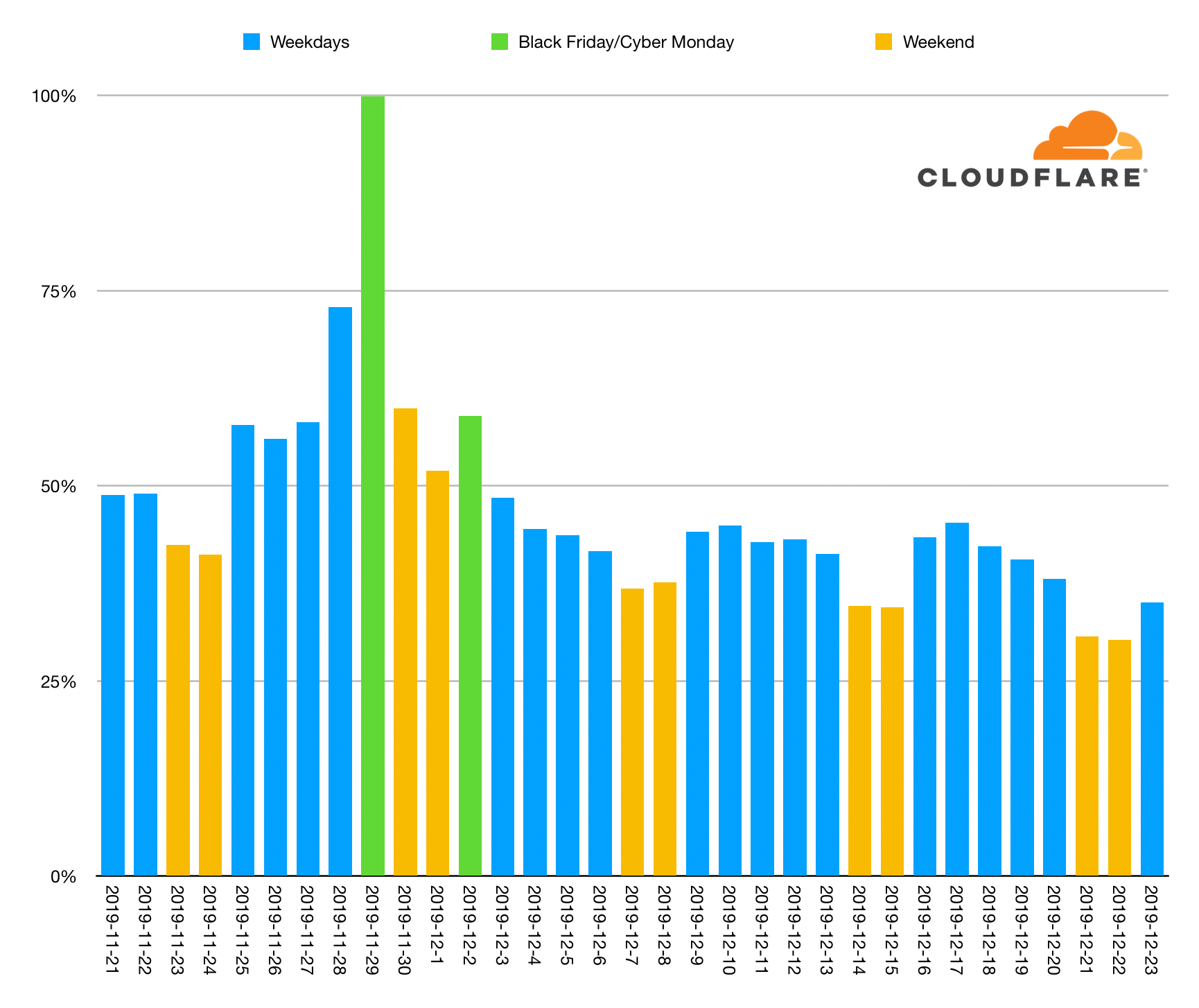
The weekends are shown in yellow and Black Friday and Cyber Monday are shown in green. You can see that checkouts ramped up during Thanksgiving week and then continued through the weekend into Cyber Monday.
Black Friday had twice the number of checkouts as the preceding Friday and the entire Thanksgiving week dominates. Post-Cyber Monday, no day reached 50% of the Continue reading
Lessons Learned from the Multistakeholder Process in the Philippines

In 2018, we began collaborating with the Philippines’ Department of Information and Communications Technology (DICT) to develop the country’s National ICT Ecosystem Framework (NICTEF), a successor to the Philippine Digital Strategy for 2011-2016.
The DICT, like all Philippine government agencies, is mandated by law to hold open consultations as a means of improving transparency and encouraging public involvement in the policymaking process. But it took this initiative further by ensuring that NICTEF is fully reflective of the needs and priorities of different sectors across the archipelago. For one year, the DICT led capacity building workshops, focus group discussions, writeshops, an online public survey, and regional consultations in each of the country’s major island groups, localizing the multistakeholder approach in the process to reach important and difficult decisions.
The NICTEF is now an authoritative guide on the Philippines’ digital ecosystem, and a roadmap to harmonize and coordinate the country’s ICT programs. The multistakeholder process adopted by NICTEF has been documented in a case study, offering other countries in the region a reference in developing public policies that are forward-thinking, inclusive, and suited to the needs of a steadily-interconnected world.
Below are some of our key takeaways from the process:
Develop Continue reading
Chipmakers’ Biggest Buys and Sells of 2019
Billions of dollars changed hands this year as industry giants attempted to bolster their positions...
Matt Oswalt – Portfolio
Short Bio Matt Oswalt hails from Portland, OR, and focuses on the intersection of network infrastructure, automation, systems, and software engineering. He’s passionate about enabling engineers to evolve their careers to the next level, and sharing the bright spots that exist within the technology industry with the masses. You can often find him speaking at conferences or meetups about these topics, as well as writing about them on his blog (https://keepingitclassless.About Matt
My name is Matt Oswalt, and I have a fairly eclectic background. When I was 14, I created my first program - an alien shooter on my TI-82 calculator. Since then, I’ve enjoyed building new things and showing them to anyone who will listen. This passion continues to this day, as you’ll find with projects like ToDD and NRE Labs, I just really enjoy building cool stuff. You can explore these and all my other open source projects on my GitHub profile.The Bookshelf
I am a big fan of Audible for books. Every once in a while I have time and patience to read a physical book, but often times I find myself needing to do things like washing dishes, going on a long walk or drive, and Audible has made it so much easier for me to get back into “reading”. Since I started doing this, I’d like to share the books that I’ve been able to get through this way.DC. Part 16. Microsoft Azure SONiC on the Mellanox switches in data centre (with Cisco XR an Nokia SR OS for inter-OP).
Hello my friend,
The Christmas and New Year is coming, so it is typically the time to think about the future and plan ahead. And today we look into future by reviewing the new network operation system deployed in the data centres hosting Microsoft Azure clouds. This operation system is called SONiC: Software for Open Networking in the Cloud.
2
3
4
5
retrieval system, or transmitted in any form or by any
means, electronic, mechanical or photocopying, recording,
or otherwise, for commercial purposes without the
prior permission of the author.
Discalimer
If you even more interested in your future, join our network automation training we start on 18th and 22nd of January, where we cover the details of the data modelling, NETCONF/YANG, REST API, Python and Ansible in the multivendor environment with Cisco, Nokia, Arista and Cumulus Linux as network functions.
Thanks
Special thanks for Avi Alkobi from Mellanox for providing me the Mellanox SN2010 for tests and initial documentation for Microsoft Azure SONiC setup.
Brief description
Everyone talks about the clouds. You can hear about public clouds, private clouds, hybrid clouds, clouds interconnection Continue reading
5G Gains US Foothold in 2019
5G is available from sea to shining sea — with many pockets of 4G LTE remaining in between.
Cisco Warns About Ongoing Security Exploit
The bug was initially spotted by Cisco in June 2018 and given a “critical” rating.
The Week in Internet News: India Sets Record for Longest Internet Shutdown in a Democracy

The longest ever: The 130-day-plus shutdown of the Internet in the Indian region of Kashmir is now the longest ever in a democracy, the Washington Post notes. The Kashmir Chamber of Commerce estimates $1.4 billion in losses due to the shutdown. Meanwhile, the Indian government is stepping up its shutdown efforts in response to protests across the country, TechCrunch reports. The protests are largely focused on a new citizenship law, which creates a path to citizenship for immigrants of all the major religions except Islam.
Another encryption fight: There’s a battle brewing over the encryption of Internet traffic being pushed by Google and Cloudflare, the ACLU says in a blog post. Some U.S. telecom carriers are calling on Congress to stop the encryption efforts. The blog post has a good explanation of the technical issues, while taking sides in the debate.
New standards for the IoT: Amazon, Apple, Google, and the Zigbee Alliance are working on a new open-source networking standard for home Internet of Things connected devices, ZDNet reports. The Connected Home over IP standard aims to make it easier for various IoT devices to communicate with each other.
Protesting social media bill: Thousands of people in Continue reading
Is AI the Antidote to Network Complexity?
While 5G and industrial IoT are still years from maturity, that's not stopping companies from...
