A global assessment of third-party connection tampering
Have you ever made a phone call, only to have the call cut as soon as it is answered, with no obvious reason or explanation? This analogy is the starting point for understanding connection tampering on the Internet and its impact.
We have found that 20 percent of all Internet connections are abruptly closed before any useful data can be exchanged. Essentially, every fifth call is cut before being used. As with a phone call, it can be challenging for one or both parties to know what happened. Was it a faulty connection? Did the person on the other end of the line hang up? Did a third party intervene to stop the call?
On the Internet, Cloudflare is in a unique position to help figure out when a third party may have played a role. Our global network allows us to identify patterns that suggest that an external party may have intentionally tampered with a connection to prevent content from being accessed. Although they are often hard to decipher, the ways connections are abruptly closed give clues to what might have happened. Sources of tampering generally do not try to hide their actions, which leaves hints of Continue reading
MSS, MSS Clamping, PMTUD, and MTU
Maximum Segment Size (MSS) and MSS clamping are concepts that can be confusing. How do they relate to the MTU (Maximum Transmission Unit)? Before we setup a lab to demonstrate these concepts, let’s give some background. Note that this entire post assumes a maximum frame size of 1518 bytes, the original Ethernet definition, and does not cover jumbo frames.
Ethernet frame
Almost all interfaces today are Ethernet. The original 802.3 standard from 1985 defined the minimum size- and maximum size frame as the following:
- minFrameSize – 64 octets.
- maxFrameSize – 1518 octets.
With a maximum frame size of 1518 octets (bytes), that leaves 1500 bytes of payload as the Ethernet frame adds 18 bytes, 14 bytes of header and 4 bytes of trailer. The Ethernet frame is shown below:
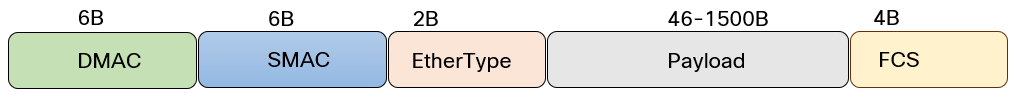
IP header
An IPv4 IP header adds at least 20 bytes to the frame. The IPv4 header is shown below:
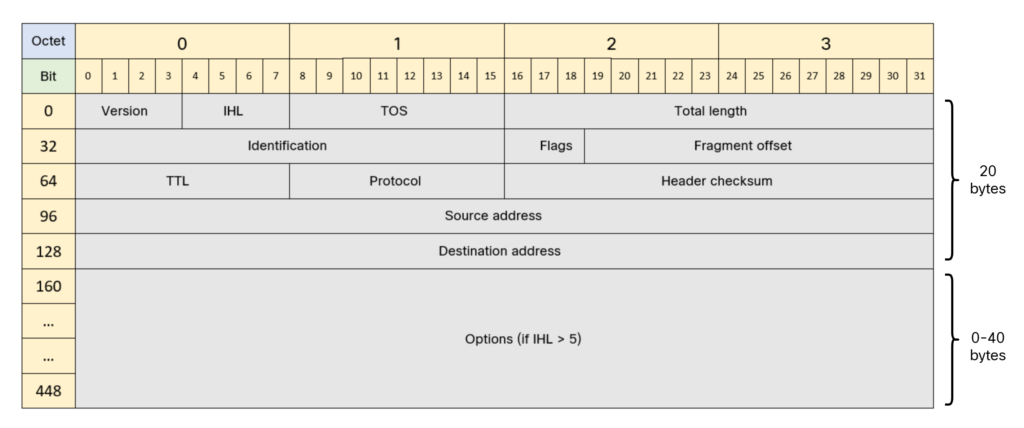
Note that more than 20 bytes can be used if the header has IP options. With no options in the IP header, there’s 1480 bytes remaining for the L4 protocol such as UDP or TCP.
TCP header
TCP also adds a minimum of 20 bytes, meaning that the maximum payload Continue reading
D2DO250: The Realities of Responsible Disclosure in the Cloud
Cloud security and responsible disclosure are the focus of today’s conversation with guest Kat Traxler. Kat shares her insights on identifying vulnerabilities in cloud services, particularly Google Cloud, and the importance of curiosity in her research. The episode explores the role of bug bounty programs and the shift towards issuing CVEs for cloud vulnerabilities. Lastly,... Read more »Routing Table and BGP RIB on SR Linux
Ages ago, I described how “traditional” network operating systems used the BGP Routing Information Base (BGP RIB), the system routing table (RIB), and the forwarding table (FIB). Here’s the TL&DR:
- Routes received from BGP neighbors are stored in BGP RIB.
- Routes redistributed into BGP from other protocols are (re)created in the BGP RIB.
- BGP selects the best routes in BGP RIB using its convoluted set of rules.
- Best routes from the BGP RIB are advertised to BGP neighbors
- Best routes from the BGP RIB compete (based on their administrative distance) against routes from other routing protocols to enter the IP routing table (system RIB)
- Routes from the system RIB are copied into FIB after their next hops are fully evaluated (a process that might involve multiple recursive lookups).
HW035: The Experience Paradox
In this episode of Heavy Wireless, host Keith Parsons and guest Tom Hollingsworth delve into the “experience paradox” in the tech industry: to get experience, you need to have experience. They highlight the disconnect between job requirements and candidates’ actual experience. Tom emphasizes the importance of hands-on learning, home labs, and making mistakes as essential... Read more »NB493: Cisco Acquires AI Startup to Police AI; Nvidia, Dell Ride GPU Profit Wave
Take a Network Break! This week we cover a couple of listener FUs, and then dive into the news. Attackers exploit a zero-day in Versa to harvest credentials, AT&T agrees to a fine of nearly $1 million for a network outage that affected 911 calls, and Intel and Broadcom tout integrated optics for more broadband... Read more »Tech Bytes: Smarter Networking and Automation With SuzieQ’s Network Observability (Sponsored)
Today on the Tech Bytes podcast: network observability. SuzieQ is an open-source project that collects, normalizes, stores, and analyzes multi-vendor network data. This data becomes a foundation for network observability and automation. We talk with Dinesh Dutt, creator of SuzieQ and founder of Stardust Systems, which makes a commercial version of SuzieQ. Stardust Systems is... Read more »PP029: Translating Security Objectives into Business Outcomes
On today’s Packet Protector we talk about how to talk about security objectives in ways that resonate with business and non-technical leaders in your organization. Tying security objectives to business outcomes can help you maintain (or increase) budgets, build trust and credibility with executives, and better align your risk management efforts with the organization’s broader... Read more »Repost: Why Are Layer-2 VPNs So Popular?
Béla Várkonyi wrote a succinct comment explaining why so many customers prefer layer-2 VPNs over layer-3 VPNs:
The reason of L2VPN is becoming more popular by service providers and customers is about provisioning complexity.
Making progress on routing security: the new White House roadmap
The Internet can feel like magic. When you load a webpage in your browser, many simultaneous requests for data fly back and forth to remote servers. Then, often in less than one second, a website appears. Many people know that DNS is used to look up a hostname, and resolve it to an IP address, but fewer understand how data flows from your home network to the network that controls the IP address of the web server.
The Internet is an interconnected network of networks, operated by thousands of independent entities. To allow these networks to communicate with each other, in 1989, on the back of two napkins, three network engineers devised the Border Gateway Protocol (BGP). It allows these independent networks to signal directions for IP prefixes they own, or that are reachable through their network. At that time, Internet security wasn’t a big deal — SSL, initially developed to secure websites, wasn’t developed until 1995, six years later. So BGP wasn’t originally built with security in mind, but over time, security and availability concerns have emerged.
Today, the White House Office of the National Cyber Director issued the Roadmap to Enhancing Internet Routing Security, and Continue reading
Python OOP – Method vs Function and the Mystery of ‘self’

I just realized how much I didn't know about Python Object-Oriented Programming. I thought I knew the basics, but a few days ago, while going through a Python course, I found out I was wrong. Before I forget what I’ve learned, I wanted to write this blog post and share it with you.
In this blog post, we’ll cover the difference between functions and methods, and what exactly ‘self’ means in Python. So, let’s get to it.
Functions vs Method
class MyClass:
def say_hello():
print('Hello')In this snippet, we’ve defined a Class called MyClass with a function named say_hello. But here’s a question for you - what do you call say_hello? Is it a function or a method?
It’s a common misconception to think that simply defining a function inside a Class automatically makes it a method. However, the distinction lies in how the function is accessed.

- Function - When you define a function inside a class, it’s just a regular function until it’s accessed through an instance of the class.
- Method - When you access that function via an instance of the class (e.g., `obj.say_hello'), it becomes a method. This is Continue reading
Cisco 1812 as Home Router
This lab delves into configuring a Cisco 1812 router, a legacy device with 100 Mbps […]
The post Cisco 1812 as Home Router first appeared on Brezular's Blog.
Poor man’s Traffic Engineering
Segment Routing allows the network operator to deploy Traffic Engineering even with the most basic routers that support the bare minimum of features.
What is traffic engineering
Traffic engineering is a set of techniques to influence the path a particular …
Worth Exploring: Free, OpenSource IPv6 Textbook
Nick Buraglio and Brian E. Carpenter published a free, open-source IPv6 textbook.
The book seems to be in an early (ever-evolving) stage, but it’s well worth exploring if you’re new to the IPv6 world, and you might consider contributing if you’re a seasoned old-timer.
It would also be nice to have a few online labs to go with it ;)
Napalm Configuration Management With Arista EOS

Hi all, welcome back to the Packetswitch blog. In today's post, we'll explore how to use NAPALM for managing device configurations. We'll focus on Arista EOS as our example. We'll cover the methods available in NAPALM and how to push, commit and revert configurations on Arista devices.
We'll start by explaining what NAPALM is and why you might want to use it. Then we'll move on to a few examples and take a look at what happens behind the scenes. This approach will give you a clear understanding of NAPALM's role in network configuration management and how it works with Arista EOS devices.
What is Napalm?
NAPALM stands for Network Automation and Programmability Abstraction Layer with Multivendor support. It's a Python library that helps network engineers manage and automate different network devices using a common set of functions. NAPALM solves the problem of dealing with multiple vendor-specific interfaces by providing a unified way to interact with network devices from various manufacturers. This means you can use the same code to manage devices from Cisco, Juniper, Arista, and others, saving time and reducing the complexity of network automation tasks.
An AX.25 implementation in Rust
After having written a user space AX.25 stack in C++, I got bitten by the Rust bug. So this is the third time I’ve written an AX.25 stack, and I’ve become exceedingly efficient at it.
Here it is:
The reason for a user space stack remains from last time, but this time:
- It’s written in Rust. Yay! I know people say Rust has a honeymoon period, but I guess that’s where I am, still.
- It’s a normal library first. The previous C++ implementation started off as microservices, which in retrospect was needlessly complex and put the cart before the horse.
I’ve added almost an excessive amount of comments to the code, to cross reference with the specs. The specs that have a few bugs, by the way.
Rust
I’m not an expert in Rust, but it allows for so much more confidence in your code than any other language I’ve tried.
I think I know enough Rust to know what I don’t fully know. Sure, I’ve successfully added lifetime annotations, created macros, and built async code, but I’m not fluent in those yet.
Interestingly, Continue reading
Fixing layout shifts caused by web fonts
In 2020, Google introduced Core Web Vitals metrics to measure some aspects of real-world user experience on the web. This blog has consistently achieved good scores for two of these metrics: Largest Contentful Paint and Interaction to Next Paint. However, optimizing the third metric, Cumulative Layout Shift, which measures unexpected layout changes, has been more challenging. Let’s face it: optimizing for this metric is not really useful for a site like this one. But getting a better score is always a good distraction. 💯
To prevent the “flash of invisible text” when using web fonts, developers should
set the font-display property to swap in @font-face rules. This method
allows browsers to initially render text using a fallback font, then replace it
with the web font after loading. While this improves the LCP score, it causes
content reflow and layout shifts if the fallback and web fonts are not
metrically compatible. These shifts negatively affect the CLS score. CSS
provides properties to address this issue by overriding font metrics when using
fallback fonts: size-adjust,
ascent-override, descent-override,
and line-gap-override.
Two comprehensive articles explain each property and their computation methods in detail: Creating Perfect Font Fallbacks in CSS and Improved Continue reading
Dell’s AI Server Business Now Bigger Than VMware Used To Be
We have been watching the big original equipment manufactures like a hawk to see how they are generating revenues and income from GPU-accelerated system sales. …
Dell’s AI Server Business Now Bigger Than VMware Used To Be was written by Timothy Prickett Morgan at The Next Platform.