Securing the SDDC with VMware NSX – Light Board Series
Is VMware the first company that springs to mind when you think about securing your software-defined data center (SDDC)? It should be.
In this new light board series, learn about the unique capabilities that VMware NSX brings to your SDDC for securing your virtualized environment.
Start out with some context on why networking and security go hand-in hand with the Network Virtualization is Inevitable video. Then, move on to the NSX as a Security Platform video, to learn why VMware can offer security options not possible in tradition environments.
But how to install NSX in an environment? Check out Hadar Freehling’s Castle Security with VMware NSX video. Curious about why the firewall in NSX is special? Watch the VMware NSX Distributed Firewall video. And finally, secure a VDI environment with Hadar’s VMware NSX and VDI video.
As your SDDC evolves, stay up-to-date with NSX and how it can help secure your assets. Any burning questions on securing your virtualized environment you don’t see addressed in the videos, and want to see? Let us know; and don’t be surprised if you see it addressed in a future video.
Julie
The post Securing the SDDC with VMware NSX – Light Board Series Continue reading
Micro-segmentation with Service Insertion – NSX Securing “Anywhere” Part IV
 Welcome to part 4 in the Micro-Segmentation Defined– NSX Securing “Anywhere” blog series. Today we will cover the role of NSX as a foundational security platform through NSX Micro-segmentation with Service Insertion. Previous topics covered in this series includes
Welcome to part 4 in the Micro-Segmentation Defined– NSX Securing “Anywhere” blog series. Today we will cover the role of NSX as a foundational security platform through NSX Micro-segmentation with Service Insertion. Previous topics covered in this series includes
- Part I – Micro-segmentation Defined
- Part II – Securing Physical environments
- Part III –Operationalizing Micro-segmentation
This blog covers the following topics:
- Defining Service Insertion
- The Role of Service Insertion in Micro-segmentation
- Network and Guest Introspection
- NSX Service Insertion
Defining Service Insertion
In modern datacenters, network and compute services either have been or are being decoupled from the physical appliances on which they have traditionally run. In the past, a datacenter service required traffic to be steered through a series of such appliances in order to be serviced appropriately, through services such as firewalls, intrusion detection and prevention, and load balancing services. As infrastructure services transition from physical appliances to software functions, it becomes possible to deploy these services with greater granularity by inserting them into a specific forwarding path. Combining multiple functions in this manner is generally referred to as a service chain or service graph.
 Figure 1: Two distinct service chains utilizing different functions
Figure 1: Two distinct service chains utilizing different functions
Once infrastructure Continue reading
5 Funding Insights from a Silicon Valley Venture Capitalist
 Network monitoring could be ripe for startups.
Network monitoring could be ripe for startups.
NYTimes vs. DNCleaks
People keep citing this New York Times article by David Sanger that attributes the DNCleaks to Russia. As I've written before, this is propaganda, not journalism. It's against basic journalistic ethics to quote anonymous "federal officials" in a story like this. The Society of Professional Journalists repudiates this [1] [2]. The NYTime's own ombudsman has itself criticized David Sanger for this practice, and written guidelines to specifically ban it.Quoting anonymous federal officials is great, when they disagree with government, when revealing government malfeasance, when it's something that people will get fired over.
But the opposite is happening here. It's either Obama himself or some faction within the administration that wants us to believe Russia is involved. They want us to believe the propaganda, then hide behind anonymity so we can't question them. This evades obvious questions, like whether all their information comes from the same public sources that already point to Russia, or whether they have their own information from the CIA or NSA that points to Russia.
Everyone knows the Washington press works this way, and that David Sanger in particular is a journalistic whore. The NetFlix series House of Cards portrays this accurately in its Continue reading
Intel Puts Numbers on the Security Talent Shortage
 25% of organizations have lost proprietary data to cyberattacks.
25% of organizations have lost proprietary data to cyberattacks.
Security & Gross Margins Dampen Juniper’s Q2 Earnings
 Juniper's CEO isn't happy with security revenues.
Juniper's CEO isn't happy with security revenues.
RCN Business Chooses Versa’s Software-Defined Security
 No on-premises equipment is required.
No on-premises equipment is required.
SoftLayer’s Founder Aims to Build a Security-as-a-Service Powerhouse
 Another startup, but this one claims 30,000 customers.
Another startup, but this one claims 30,000 customers.
Operationalizing Micro-segmentation – NSX Securing “Anywhere” – Part III
 Welcome to part 3 of the Micro-Segmentation Defined – NSX Securing “Anywhere” blog series. This installment covers how to operationalize NSX Micro-Segmentation. Be sure to check out Part 1 on the definition of micro-segmentation and Part 2 on securing physical workloads with NSX.
Welcome to part 3 of the Micro-Segmentation Defined – NSX Securing “Anywhere” blog series. This installment covers how to operationalize NSX Micro-Segmentation. Be sure to check out Part 1 on the definition of micro-segmentation and Part 2 on securing physical workloads with NSX.
This blog covers the following topics:
- Micro-segmentation design patterns
- Determining appropriate security groups and policies
- Deploying micro-segmentation
- Application lifecycle management with vRealize Automation and NSX
- Day 2 operations for micro-segmentation
Micro-segmentation design patterns
Micro-segmentation can be implemented based on various design patterns reflecting specific requirements. The NSX Distributed Firewall (DFW) can be used to provide controlled communication between workloads independent of their network connectivity. These workloads can, for example, all connect to a single VLAN. Distributed logical switches and routers can be leveraged to provide isolation or segmentation between different environments or application tiers, regardless of the underlying physical network, as well as many other benefits. Furthermore, the NSX Edge Service Gateway (ESG) can provide additional functionality such as NAT or load balancing and the NSX Service Insertion framework enables partner services such as L7 firewalling, agent-less anti-virus or IPS/IDS applied to workloads that need additional security controls.
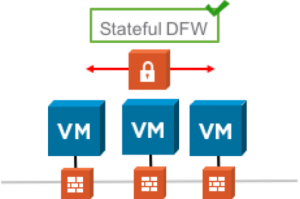
Figure 1: Leveraging the DFW to provide Continue reading
Speed Bumps Ahead for Network Security
 Traffic volumes are growing exponentially across every segment.
Traffic volumes are growing exponentially across every segment.
My Raspeberry Pi cluster
So I accidentally ordered too many Raspberry Pi's. Therefore, I built a small cluster out of them. I thought I'd write up a parts list for others wanting to build a cluster.To start with is some pics of the cluster What you see is a stack of 7 RPis. At the bottom of the stack is a USB multiport charger and also an Ethernet hub. You see USB cables coming out of the charger to power the RPis, and out the other side you see Ethernet cables connecting the RPis to a network. I've including the mouse and keyboard in the picture to give you a sense of perspective.
Here is the same stack turn around, seeing it from the other side. Out the bottom left you see three external cables, one Ethernet to my main network and power cables for the USB charger and Ethernet hub. You can see that the USB hub is nicely tied down to the frame, but that the Ethernet hub is just sort jammed in there somehow.
The concept is to get things as cheap as possible, on per unit basis. Otherwise, one might as well just buy more expensive computers. My parts Continue reading
Technology Short Take #69
Welcome to Technology Short Take #69! In this post, I’ve collected a variety of links related to major data center technology areas. This episode is a bit long; sorry about that!
Networking
- Lindsay Hill recently noted that he’s been working to add support to netmiko for the Brocade ICX and MLXe, and is looking into support for VDX. Netmiko, if you haven’t heard, is a fantastic Python library that’s really useful when writing Python-based network automation scripts.
- I mentioned a while back that I was taking a deeper look at MPLS (to which my colleague Bruce Davie—one of the creators of MPLS—jokingly quipped, “Why are you looking at legacy tech?”). Honestly, I haven’t had a great deal of time to make much progress, but I did come across this article by Sudeep Goyal which helped reinforce some of the basics I already knew. It may prove useful to others who are also seeking to improve their knowledge of MPLS.
- Peter Phaal has been writing some really interesting stuff (interesting to me, at least). First up, there’s a great article on using IPVLAN with Docker and Cumulus Linux (with a tie back to sFlow, naturally!). I’m really eager to Continue reading
Focusing on Security in the SGiLAN
 Virtualization of the SGiLAN in mobile networks through the use of converged platforms can improve security.
Virtualization of the SGiLAN in mobile networks through the use of converged platforms can improve security.
F5 CEO to Retire (Again) as New ADCs Emerge
 The Shuttle series points to the future as John McAdam points toward the exit.
The Shuttle series points to the future as John McAdam points toward the exit.
Intel Forecasts a Rebound Driven by Data Centers & IoT
 The company reported revenues of $13.5 billion in 2Q.
The company reported revenues of $13.5 billion in 2Q.
Siemplify Helps Set Up Security Playbooks
 Siemplify says it can find breaches. The question is what to do next.
Siemplify says it can find breaches. The question is what to do next.
Security Startup GuardiCore Raises $20M
 A case where deception is on your side.
A case where deception is on your side.
Ethernet-over-VPN: What Could Possibly Go Wrong?
One of my readers sent me a link to SoftEther, a VPN solution that
[…] penetrates your network admin's troublesome firewall for overprotection. […] Any deep-packet inspection firewalls cannot detect SoftEther VPN's transport packets as a VPN tunnel, because SoftEther VPN uses Ethernet over HTTPS for camouflage.
What could possibly go wrong with such a great solution?
Read more ...Network Break 96: News From Cisco Live; A Security Debate
The latest Network Break delves into news from Cisco Live US, including new security products, a potential ACI/NSX roadmap, a call for network engineers to move away from the CLI and more! The post Network Break 96: News From Cisco Live; A Security Debate appeared first on Packet Pushers.
AT&T’s Threat Intellect Combines Security & SDN
 The new service is a brew of machine learning, big data, and network policy.
The new service is a brew of machine learning, big data, and network policy.
