Fortinet Weaves AccelOps Into Its Security Fabric
 The deal ties Fortinet into the SIEM crowd.
The deal ties Fortinet into the SIEM crowd.
No, Musky, Feudalism is best for Mars
Recently, the press fawned all over Elon Musk's comments at a conference. Among them was Musk's claim that "direct democracy" would be the best system, where citizen's vote directly for laws, rather than voting for (corrupt) representatives/congressmen. This is nonsense. The best political system would be feudalism.There is no such thing as "direct democracy". Our representatives in congress are only the first layer on top of a bureaucracy. Most rules that restrict us are not "laws" voted by congress but "regulations" decided by some bureaucrat.
Consider the BP Gulf Oil spill, as an example. It happened because oil companies got cozy with their regulators, the minerals Management Service (MMS), part of the Department of the Interior. The bureaucrats had a dual mandate: to protect the environment, and to promote economic activity. Oil companies lobbied them to risk the environment in favor of profits.
Consider Obamcare's controversial mandate that health insurers must pay for abortions. This was not part of the law pass by congress, but a decision by the bureaucrats in charge of all the little details in carrying out the law.
Consider the Federal Communication Commission (FCC) regulation of the Internet. It bases its Continue reading
Instrumenting masscan for AFL fuzzing
This blog post is about work in progress. You probably don't want to read it.So I saw this tweet today:
Fuzzing masscan by @ErrataRob with AFL by @lcamtuf.— Dr David D. Davidson (@dailydavedavids) June 5, 2016
Forgot to remove the crash-handler so crashes logged as hangs. pic.twitter.com/Yh5ElNyvOm
As it turns it, he's just fuzzing input files. This is good, he's apparently already found some bugs, but it's not a huge threat.
Instead, what really needs to be fuzzed is network input. This is chronic problem with AFL, which is designed for inserting files, not network traffic, into programs.
But making this work is actually pretty trivial. I just need to make a tiny change to masscan so that instead of opening a libpcap adapter, it instead opens a libpcap formatted file.
This change was trivial, successfully running it is tough. You have to configure the command-line so all IP addresses match up with the libpcap file content, which is a pain. I created a sample lipcap file and checked it into the project, along with a help document explaining it. Just git clone the project, run make, then run this command line to see it Continue reading
Micro-segmentation Defined – NSX Securing “Anywhere”
 The landscape of the modern data center is rapidly evolving. The migration from physical to virtualized workloads, move towards software-defined data centers, advent of a multi-cloud landscape, proliferation of mobile devices accessing the corporate data center, and adoption of new architectural and deployment models such as microservices and containers has assured the only constant in modern data center evolution is the quest for higher levels of agility and service efficiency. This march forward is not without peril as security often ends up being an afterthought. The operational dexterity achieved through the ability to rapidly deploy new applications overtakes the ability of traditional networking and security controls to maintain an acceptable security posture for those application workloads. That is in addition to a fundamental problem of traditionally structured security not working adequately in more conventional and static data centers.
The landscape of the modern data center is rapidly evolving. The migration from physical to virtualized workloads, move towards software-defined data centers, advent of a multi-cloud landscape, proliferation of mobile devices accessing the corporate data center, and adoption of new architectural and deployment models such as microservices and containers has assured the only constant in modern data center evolution is the quest for higher levels of agility and service efficiency. This march forward is not without peril as security often ends up being an afterthought. The operational dexterity achieved through the ability to rapidly deploy new applications overtakes the ability of traditional networking and security controls to maintain an acceptable security posture for those application workloads. That is in addition to a fundamental problem of traditionally structured security not working adequately in more conventional and static data centers.
Without a flexible approach to risk management, which adapts to the onset of new technology paradigms, security silos using disparate approaches are created. These silos act as control islands, making it difficult to apply risk-focused predictability into your corporate security posture, causing unforeseen risks to be realized. These actualized risks cause an organization’s attack surface to grow as the adoption of new compute Continue reading
Technology Short Take #67
Welcome to Technology Short Take #67. Here’s hoping something I’ve collected for you here proves useful!
Networking
- Anthony Burke has written a script that uses VMware NSX to protect VMware Log Insight instances. More information on the script is in his blog post.
- Russ White tackles the issue of networking engineers needing to learn to code. Is it necessary? Russ thinks so—but probably not for the reasons you might think. I tend to agree with Russ’ line of thinking.
- This article from Marcos Hernandez shows one way to do dynamic routing in OpenStack. It’s a bit of a hack, to be honest, but it gets the job done until dynamic routing makes its way into OpenStack Neutron (which looks like it may have landed in the Mitaka release—can anyone confirm?).
- Jason Messer has an article describing how networking works with Windows containers.
- Tom Hollingsworth discusses how the rise of overlay networks killed large layer 2 networks and tools for building large layer 2 networks, like TRILL.
- Dmitri Kalintsev examines some options for addressing storage-related connectivity in NSX environments.
Servers/Hardware
- Drew Conry-Murray shines a light on Intel’s network ambitions. This is something I’ve been watching for a couple of years, Continue reading
My fellow Republicans: don’t support Trump
Scott Adams, the creator of the Dilbert comic strip, has a post claiming a Trump presidency wouldn't be as bad as people fear. It's a good post. But it's wrong.Trump is certainly not as bad as his haters claim. Trump not only disables the critical-thinking ability of his supporters, but also of his enemies. In most conversations, I end up defending Trump -- not because I support him as a candidate, but because I support critical-thinking. He's only racist sometimes, most of the time I love his political incorrectness.
But with all that said, he would indeed be a horrible president. As a long-term Republican, I'd prefer a Hillary Clinton presidency, and I hate Hillary to the depths of my soul. She's corrupt, and worst of all, she's a leftist.
But there's a thing worse than being a leftist (or right-winger) and that's being a "populist demagogue". Populist demagogues tell you that all your problems are caused by them (you know, those people), and present unrealistic solutions to problems. They appeal to base emotion and ignorance.
When nations fail because of politics, it's almost always due to populist demagogues. Virtually all dictators are a "man of the people", protecting Continue reading
Drumpf: this is not how German works
In our willingness to believe any evil of Trump, some have claimed his original name was "Drumpf". This isn't true, this isn't how the German language works. Trump has the power to short-circuit critical thinking in both his supporters and his enemies. The "Drumpf" meme is just one example.There was no official pronunciation or spelling of German words/names until after Trump's grandfather was born. As this The Guardian article describes, in the city ("Kallstadt") where Trump's grandfather was born, you'll see many different spellings of the family name in the church's records. like "Drumb, Tromb, Tromp, Trum, Trumpff, Dromb" and Trump. A person might spell their name different ways on different documents, and the names of children might be spelled different than their parent's. It makes German genealogy tough sometimes.
During that time, different areas of German had different dialects that were as far apart as Dutch and German are today. Indeed, these dialects persist. Germans who grow up outside of cities often learn their own local dialect and standard German as two different languages. Everyone understands standard German, but many villagers cannot speak it. They often live their entire lives within a hundred kilometers of where they grew Continue reading
What Is Software-Defined Security?
Gabi Gerber is organizing a Software-Defined Security event in Zurich next week in which I’ll talk about real-life security solutions that could be called software defined for whatever reason, and my friend Christoph Jaggi sent me a few questions trying to explore this particular blob of hype.
For obvious reasons he started with “Isn’t it all just marketing?”
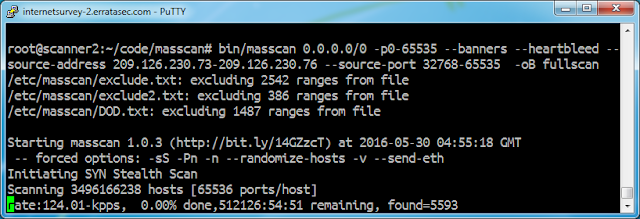
Read more ...From scratch: why these mass scans are important
The way the Internet works is that "packets" are sent to an "address". It's the same principle how we send envelopes through the mail. Just put an address on it, hand it to the nearest "router", and the packet will get forwarded hop-to-hop through the Internet in the direction of the destination.Doing a ‘full scan’ of the Internet right now
So I'm doing a "full" scan of the Internet, all TCP ports 0-65535 on all addresses. This explains the odd stuff you see from 209.126.230.7x.I'm scanning at only 125kpps from 4 source IP addresses, or roughly 30kpps from each source address. This is so that I'll get below many thresholds for IDSs, which trigger when they see fast scans from a single address. The issue isn't to avoid detection, but to avoid generating work for people who get unnecessarily paranoid about the noise they see in their IDS logs.
This scan won't finish at this speed, of course, it won't get even close. Technically, it'd take 50 years to complete at this rate.
The point isn't create a comprehensive scan, but to do sampling scan. I'll let it run a week like this, which will get 0.1% of the Internet, and then stop the scan.
What am I looking for? I don't know. I'm just doing something weird in order to see what happens. With that said, I am testing any port I connect to with Heartbleed. This should give us an estimation of how many Internet-of-Things devices are still vulnerable to that bug. I'm Continue reading
Hiroshima is a complex memorial
In the news is Obama's visit to the Hiroshima atomic bomb memorial. The memorial is more complex than you think. It's not a simple condemnation of the bomb. Instead, it's a much more subtle presentation of the complexity of what happened.I mention this because of articles like this one at Foreign Policy magazine, in which the author starts by claiming he frequently re-visits Hiroshima. He claims that the memorial has a clear meaning, a message, that he takes back from the site. It doesn't.
The museum puts the bombing into context. It shows how Japan had been in a constant state of war since the 1890s, with militaristic roots going back further in to Samurai culture. It showed how Japan would probably have continued their militaristic ways had the United States not demanded complete surrender, a near abdication of the emperor, and imposed a pacifist constitution on the country.
In other words, Japan accepts partial responsibility for having been bombed.
It doesn't shy away from the horror of the bomb. It makes it clear that such bombs should never again be used on humans. But even that has complexity. More people were killed in the Tokyo firebombing than Hiroshima Continue reading
The EFF is Orwellian as fuck
As this blog has documented many times * * * *, the Electronic Frontier Foundation (EFF) is exactly the populist demagogues that Orwell targets in his books 1984 and Animal Farm. Today, the EFF performed yet another amusingly Orwellian stunt. Urging the FCC to regulate cyberspace, it cites the exact law that it had previously repudiated.Specifically, the EFF frequently champions the document Declaration of Independence of Cyberspace, written by one of its founders, John Perry Barlow. This document says:
"Governments of the Industrial World, you weary giants of flesh and steel, I come from Cyberspace, the new home of Mind. On behalf of the future, I ask you of the past to leave us alone. You are not welcome among us. You have no sovereignty where we gather."Specifically, Barlow is talking about a then recent act of Congress:
In the United States, you have today created a law, the Telecommunications Reform Act, which repudiates your own Constitution and insults the dreams of Jefferson, Washington, Mill, Madison, DeToqueville, and Brandeis. These dreams must now be born anew in us.That 1996 Act adds sections to the telcom laws, such as this portion:
Continue reading
Verizon’s Test Lab Launches IoT Security Testing Program
 ICSA Labs lays claim to an IoT first.
ICSA Labs lays claim to an IoT first.
Palo Alto Networks Shares Sink Despite Strong Q3
 Investors wanted more, apparently.
Investors wanted more, apparently.
Docker Online Meetup #39: Docker Security
During this week’s Docker Online Meetup, Director of Security at Docker, Inc. Nathan McCauley joined us to discuss all things related to Docker security! The meetup started with Nathan presenting on securing the software supply chain with Docker (read this … ContinuedSecuring the Cloud With SDN
 An in depth analysis of the implications of increased threats for network virtualization, cloud & security.
An in depth analysis of the implications of increased threats for network virtualization, cloud & security.
Security Startup vArmour Raises a $41M Series D
 A lot more money for microsegmentation.
A lot more money for microsegmentation.
BGP Security and SPAM
Spam might seem like an annoyance in the US and other areas where bandwidth is paid for by the access rate—and what does spam have to do with BGP security? In many areas of the world, however, spam makes email practically unusable. When you’re paying for Internet access by the byte transmitted or received, spam costs real money. The normal process for combating spam involves a multi-step process, one step of which is to assess the IP address of the mail server’s previous activity for a history of originating spam. In order to avoid classifiers that rely on the source IP address, spammers have turned to hijacking IP address space for short periods of time. Since this address space is normally used for something other than email (or it’s not used at all), there is no history on which a spam detection system can rely.
The evidence for spam related hijacking, however, is largely anecdotal, primarily based in word of mouth and the rare widely reported incidents. How common are these hijacks, really? What sort of address space is really used? To answer this question, a group of researchers from Symantec and the Qatar Computing Research Center undertook a project Continue reading
Enhancing Network Security With SDN Automation
 Quarantine and monitoring can strengthen your SDN security position.
Quarantine and monitoring can strengthen your SDN security position.
2016 Next-gen Infrastructure Security Report Available Now
 Download now to learn the latest on security infrastructure.
Download now to learn the latest on security infrastructure.