Shields up: free Cloudflare services to improve your cyber readiness

Since our founding, Cloudflare's mission has been to "help build a better Internet," and we take it to heart. It used to be that the services required to adequately secure an online presence were only available to the largest of enterprises — organizations big enough to afford both the technology itself and the teams to manage it.
We've worked hard over the years to level the playing field. This has meant making more and more of the essential tools for protecting an online presence available to as many people as possible. Cloudflare offers unmetered DDoS protection — for free. We were the first to introduce SSL at scale — for free. And it’s not just protection for your external-facing infrastructure: we have a free Zero Trust plan that enables teams to protect their internal-facing infrastructure, too.
These types of tools have always been important for the billions of people on the Internet. But perhaps never as important as they've become this week.
Concurrent with the Russian invasion of Ukraine, we've seen increasing cyberattacks on the Internet, too. Governments around the world are encouraging organizations to go “shields up” — with warnings coming from the United States’ Cybersecurity & Infrastructure Security Continue reading
Cloudflare re-enforces commitment to security in Germany via BSIG audit


As a large data processing country, Germany is at the forefront of security and privacy regulation in Europe and sets the tone for other countries to follow. Analyzing and meeting the requirements to participate in Germany’s cloud security industry requires adherence to international, regional, and country-specific standards. Cloudflare is pleased to announce that we have taken appropriate organizational and technical precautions to prevent disruptions to the availability, integrity, authenticity, and confidentiality of Cloudflare’s production systems in accordance with BSI-KritisV. TÜViT, the auditing body tasked with auditing Cloudflare and providing the evidence to BSI every two years. Completion of this audit allows us to comply with the NIS Directive within Germany.
Why do cloud companies operating in Germany need to go through a BSI audit?
In 2019, Cloudflare registered as an Operator of Essential Services’ under the EU Directive on Security of Network and Information Systems (NIS Directive). The NIS Directive is cybersecurity legislation with the goal to enhance cybersecurity across the EU. Every member state has started to adopt national legislation for the NIS Directive and the criteria for compliance is set individually by each country. As an ‘Operator of Essential Services’ in Germany, Cloudflare is regulated by the Federal Continue reading
BGP security and confirmation biases


This is not what I imagined my first blog article would look like, but here we go.
On February 1, 2022, a configuration error on one of our routers caused a route leak of up to 2,000 Internet prefixes to one of our Internet transit providers. This leak lasted for 32 seconds and at a later time 7 seconds. We did not see any traffic spikes or drops in our network and did not see any customer impact because of this error, but this may have caused an impact to external parties, and we are sorry for the mistake.
Timeline
All timestamps are UTC.
As part of our efforts to build the best network, we regularly update our Internet transit and peering links throughout our network. On February 1, 2022, we had a “hot-cut” scheduled with one of our Internet transit providers to simultaneously update router configurations on Cloudflare and ISP routers to migrate one of our existing Internet transit links in Newark to a link with more capacity. Doing a “hot-cut” means that both parties will change cabling and configuration at the same time, usually while being on a conference call, to reduce downtime and impact on the network. Continue reading
Gigamon Introduces Playbooks, Plus A Full Year Of Data Retention, To Its NDR Service
Gigamon has added new features to its SaaS-based Network Detection and Response (NDR) service, including playbooks that provide context for investigations, and a full year of data retention. In addition, Gigamon hopes to compete with more established NDR vendors by bringing more of a human touch to its service.
The post Gigamon Introduces Playbooks, Plus A Full Year Of Data Retention, To Its NDR Service appeared first on Packet Pushers.
2022 Top 10 Cyber Security Certifications
Before Starting Cyber Security
Cyber Security, sometimes you might find it as Cyber Operations, CyberOps, is the branch of Network Security that focuses on attacks, from the internet or from the inside of the network, gaps, bugs, look for them before they get used, fix them, and look again.
so the engineers continue to keep looking and fixing, as the internet is always evolving and generating more threats.
How to Study Cyber Security
generally, the domain of security (Information Security, Cyber Security) has nowadays hundreds of certifications and exams from many different vendors.
some are involved in the industry of making security devices/components, others are there just to teach us and make us the best engineers in the domain.
and mostly, cyber stuff comes from companies that focuses on creating the content/references more.
rather than information security exams and books that comes from vendors that produces platforms (Firewalls, IPS, IDS, NGFW, NGIPS, ESA, WSA, and many others).
so as a beginner, up to higher than an expert, many exams should be studied.
of course alongside with some other general/networking exams that you might already hold before studying the cyber security, and these exams will be mentioned below.
Top 10 Cyber Continue reading
OMG: VTP Is Insecure
One of my readers sent me an interesting pointer:
I just watched a YouTube video by a security researcher showing how a five line python script can be used to unilaterally configure a Cisco switch port connected to a host computer into a trunk port. It does this by forging a single virtual trunk protocol (VTP) packet. The host can then eavesdrop on broadcast traffic on all VLANs on the network, as well as prosecute man-in-the-middle of attacks.
I’d say that’s a “startling revelation” along the lines of “OMG, VXLAN is insecure” – a wonderful way for a security researcher to gain instant visibility. From a more pragmatic perspective, if you enable an insecure protocol on a user-facing port, you get the results you deserve1.
While I could end this blog post with the above flippant remark, it’s more fun considering two fundamental questions.
OMG: VTP Is Insecure
One of my readers sent me an interesting pointer:
I just watched a YouTube video by a security researcher showing how a five line python script can be used to unilaterally configure a Cisco switch port connected to a host computer into a trunk port. It does this by forging a single virtual trunk protocol (VTP) packet. The host can then eavesdrop on broadcast traffic on all VLANs on the network, as well as prosecute man-in-the-middle of attacks.
I’d say that’s a “startling revelation” along the lines of “OMG, VXLAN is insecure” – a wonderful way for a security researcher to gain instant visibility. From a more pragmatic perspective, if you enable an insecure protocol on a user-facing port, you get the results you deserve1.
While I could end this blog post with the above flippant remark, it’s more fun considering two fundamental questions.
Why Privacy?
I’ve kicked off a series over at Packet Pushers on the ; the first installment is up now.
There’s a chapter in my new book on the topic, as well.
Announcing the public launch of Cloudflare’s bug bounty program
Today we are launching Cloudflare’s paid public bug bounty program. We believe bug bounties are a vital part of every security team’s toolbox and have been working hard on improving and expanding our private bug bounty program over the last few years. The first iteration of our bug bounty was a pure vulnerability disclosure program without cash bounties. In 2018, we added a private bounty program and are now taking the next step to a public program.
Starting today, anyone can report vulnerabilities related to any Cloudflare product to our public bug bounty program, hosted on HackerOne’s platform.
Let's walk through our journey so far.

Step 1: starting a vulnerability disclosure program
In 2014, when the company had fewer than 100 employees, we created a responsible disclosure policy to provide a safe place for security researchers to submit potential vulnerabilities to our security team, with some established rules of engagement. A vulnerability disclosure policy is an important first step for a company to take because it is an invitation to researchers to look at company assets without fear of repercussions, provided the researchers follow certain guidelines intended to protect everyone involved. We still stand by that policy and welcome Continue reading
Privacy And Networking: Part 1 – Why Privacy?
In the first post on a series on privacy and networking, Russ White makes the case that privacy matters not just for infosec, risk management, or compliance, but as a human right.
The post Privacy And Networking: Part 1 – Why Privacy? appeared first on Packet Pushers.
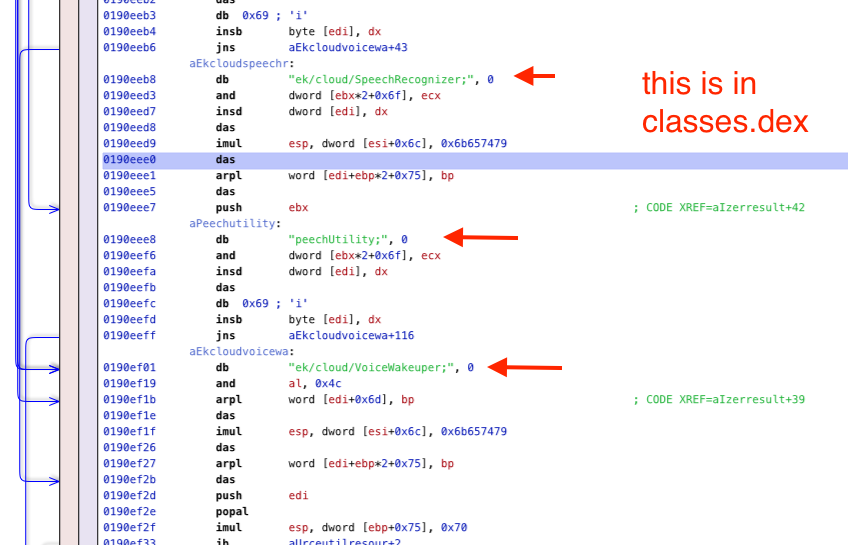
No, a researcher didn’t find Olympics app spying on you
For the Beijing 2022 Winter Olympics, the Chinese government requires everyone to download an app onto their phone. It has many security/privacy concerns, as CitizenLab documents. However, another researcher goes further, claiming his analysis proves the app is recording all audio all the time. His analysis is fraudulent. He shows a lot of technical content that looks plausible, but nowhere does he show anything that substantiates his claims.
Average techies may not be able to see this. It all looks technical. Therefore, I thought I'd describe one example of the problems with this data -- something the average techie can recognize.
His "evidence" consists screenshots from reverse-engineering tools, with red arrows pointing to the suspicious bits. An example of one of these screenshots is this on:
Landscape of API Traffic
In recent years we have witnessed an explosion of Internet-connected applications. Whether it is a new mobile app to find your soulmate, the latest wearable to monitor your vitals, or an industrial solution to detect corrosion, our life is becoming packed with connected systems.
How is the Internet changing because of this shift? This blog provides an overview of how Internet traffic is evolving as Application Programming Interfaces (APIs) have taken the centre stage among the communication technologies. With help from the Cloudflare Radar team, we have harnessed the data from our global network to provide this snapshot of global APIs in 2021.
The huge growth in API traffic comes at a time when Cloudflare has been introducing new technologies that protect applications from nascent threats and vulnerabilities. The release of API Shield with API Discovery, Schema Validation, mTLS and API Abuse Detection has provided customers with a set of tools designed to protect their applications and data based on how APIs work and their challenges.
We are also witnessing increased adoption of new protocols. Among encryption protocols, for example, TLS v1.3 has become the most used protocol for APIs on Cloudflare while, for transport protocols, we Continue reading
6 East-West Security Myths Busted
With the world at our fingertips via a simple Google search, it can sometimes be tough to figure out what’s fact and what’s fiction. Whether you’re an expert, novice, or beginner in the tech world, time should be spent putting capabilities and terms into action – rather than trying to piece them together and understand them like a Sudoku puzzle. That’s why we’re going to debunk six major East-West security myths for you – so you can get back to the good stuff.
1. East-West security is the monitoring and inspection of traffic moving medially within the network perimeter, working to identify and block threats and enable access rights.
Busted. East-West security does all of the fancy stuff mentioned, with one very important difference: it moves laterally through the network perimeter. This is a key understanding, since East-West security operates on the premise that threat factors will eventually find a way through next-generation firewalls – which means all internal network traffic is vulnerable.
2. A traditional firewall that manages North-South traffic can handle a modern network breach by itself.
Busted. While it’s important to have North-South security in place (filtering the traffic that is exiting and entering the network), it cannot protect the network on its own Continue reading
CyberFlood: The Security Mix Tab
For those of you that use CyberFlood I want to talk about something very specific today. The “Traffic Mix” tab and the “Security Mix” tab when running a CyberFlood test. When I was playing with CyberFlood in my little “Stealthwatch... Read More ›
The post CyberFlood: The Security Mix Tab appeared first on Networking with FISH.
Microsegmentation Terminology
While I liked reading the Where to Stick the Firewall blog post by Peter Welcher, it bothered me a bit that he used microsegmentation to mean security groups.
I know that microsegmentation became approximately as well-defined as cloud or SDN1, but let’s aim our shiny lance 2 at the nearest windmill and gallop away…
Microsegmentation Terminology
While I liked reading the Where to Stick the Firewall blog post by Peter Welcher, it bothered me a bit that he used microsegmentation to mean security groups.
I know that microsegmentation became approximately as well-defined as cloud or SDN1, but let’s aim our shiny lance 2 at the nearest windmill and gallop away…