DDoS attack trends for 2021 Q2


Recent weeks have witnessed massive ransomware and ransom DDoS (Distributed Denial of Service) attack campaigns that interrupted aspects of critical infrastructure around the world, including one of the largest petroleum pipeline system operators, and one of the world’s biggest meat processing companies. Earlier this quarter, more than 200 organizations across Belgium, including the government and parliament websites and other services, were also DDoS’d.
And when most of the United States were celebrating Independence Day on July 4, hundreds of US companies were hit by a ransomware attack demanding 70 million USD in Bitcoin. Attackers known to be affiliated with REvil, a Russian ransomware group, exploited multiple previously unknown vulnerabilities in IT management software. The targets included schools, small public-sector bodies, travel and leisure organizations, and credit unions, to name a few. While the threat of ransomware and ransom DDoS is not new (read our posts on ransomware and ransom DDoS from 2021 Q1), the latest attacks on Internet properties ranging from wineries, professional sports teams, ferry services and hospitals has brought them from just being background noise to front page headlines affecting our day-to-day lives. In fact, recent attacks have propelled ransomware and DDoS to the top of US Continue reading
Microsoft Misplaced Security Priorites
 Pays bug bounty pittance, spends big on speculative product
Pays bug bounty pittance, spends big on speculative product
Ransomware: Quis custodiet ipsos custodes
Many claim that "ransomware" is due to cybersecurity failures. It's not really true. We are adequately protecting users and computers. The failure is in the inability of cybersecurity guardians to protect themselves. Ransomware doesn't make the news when it only accesses the files normal users have access to. The big ransomware news events happened because ransomware elevated itself to that of an "administrator" over the network, giving it access to all files, including online backups.
Generic improvements in cybersecurity will help only a little, because they don't specifically address this problem. Likewise, blaming ransomware on how it breached perimeter defenses (phishing, patches, password reuse) will only produce marginal improvements. Ransomware solutions need to instead focus on looking at the typical human-operated ransomware killchain, identify how they typically achieve "administrator" credentials, and fix those problems. In particular, large organizations need to redesign how they handle Windows "domains" and "segment" networks.
I read a lot of lazy op-eds on ransomware. Most of them claim that the problem is due to some sort of moral weakness (laziness, stupidity, greed, slovenliness, lust). They suggest things like "taking cybersecurity more seriously" or "do better at basic cyber hygiene". These are "unfalsifiable" -- things that nobody Continue reading
NATs, PATs, and Network Hygiene
While reading a research paper on address spoofing from 2019, I ran into this on NAT (really PAT) failures—
The authors state 49% of the NATs they discovered in their investigation of spoofed addresses fail in one of these two ways. From what I remember way back when the first NAT/PAT device (the PIX) was deployed in the real world (I worked in TAC at the time), there was a lot of discussion about what a firewall should do with packets sourced from addresses not indicated anywhere.
If I have an access list including 192.168.1.0/24, and I get a packet sourced from 192.168.2.24, Continue reading
Password Managers Aren’t Good But I Use One
 Not the app but the integration
Not the app but the integration
Some quick notes on SDR
I'm trying to create perfect screen captures of SDR to explain the world of radio around us. In this blogpost, I'm going to discuss some of the imperfect captures I'm getting, specifically, some notes about WiFi and Bluetooth.
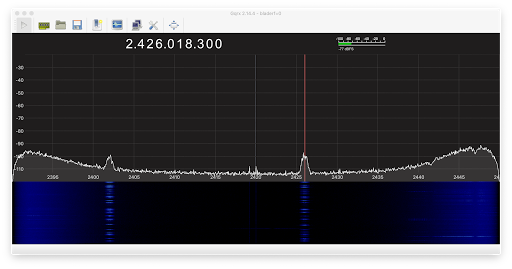
An SDR is a "software defined radio" which digitally samples radio waves and uses number crunching to decode the signal into data. Among the simplest thing an SDR can do is look at a chunk of spectrum and see signal strength. This is shown below, where I'm monitoring part of the famous 2.4 GHz pectrum used by WiFi/Bluetooth/microwave-ovens:
There are two panes. The top shows the current signal strength as graph. The bottom pane is the "waterfall" graph showing signal strength over time, display strength as colors: black means almost no signal, blue means some, and yellow means a strong signal.
The signal strength graph is a bowl shape, because we are actually sampling at a specific frequency of 2.42 GHz, and the further away from this "center", the less accurate the analysis. Thus, the algorithms think there is more signal the further away from the center we are.
What we do see here is two peaks, at 2.402 Continue reading
Cracking WPA/WPA2 Pre-shared Key Using GPU
The WPA/WPA2 4-way authentication handshake between AP (authenticator) and client (supplicant) is used to generate encryption keys. These keys are then used to encrypt data sent over wireless medium. In the previous tutorial, we installed the aircrack-ng suite to capture and crack the 4-way authentication handshake to obtain passphrase needed to access a wireless network. […]Continue reading...
More products, more partners, and a new look for Cloudflare Logs

We are excited to announce a new look and new capabilities for Cloudflare Logs! Customers on our Enterprise plan can now configure Logpush for Firewall Events and Network Error Logs Reports directly from the dashboard. Additionally, it’s easier to send Logs directly to our analytics partners Microsoft Azure Sentinel, Splunk, Sumo Logic, and Datadog. This blog post discusses how customers use Cloudflare Logs, how we’ve made it easier to consume logs, and tours the new user interface.
New data sets for insight into more products
Cloudflare Logs are almost as old as Cloudflare itself, but we have a few big improvements: new datasets and new destinations.
Cloudflare has a large number of products, and nearly all of them can generate Logs in different data sets. We have “HTTP Request” Logs, or one log line for every L7 HTTP request that we handle (whether cached or not). We also provide connection Logs for Spectrum, our proxy for any TCP or UDP based application. Gateway, part of our Cloudflare for Teams suite, can provide Logs for HTTP and DNS traffic.
Today, we are introducing two new data sets:
Firewall Events gives insight into malicious traffic handled by Cloudflare. It provides detailed information Continue reading
When we’ll get a 128-bit CPU
On Hacker News, this article claiming "You won't live to see a 128-bit CPU" is trending". Sadly, it was non-technical, so didn't really contain anything useful. I thought I'd write up some technical notes.
The issue isn't the CPU, but memory. It's not about the size of computations, but when CPUs will need more than 64-bits to address all the memory future computers will have. It's a simple question of math and Moore's Law.
Today, Intel's server CPUs support 48-bit addresses, which is enough to address 256-terabytes of memory -- in theory. In practice, Amazon's AWS cloud servers are offered up to 24-terabytes, or 45-bit addresses, in the year 2020.
Doing the math, it means we have 19-bits or 38-years left before we exceed the 64-bit registers in modern processors. This means that by the year 2058, we'll exceed the current address size and need to move 128-bits. Most people reading this blogpost will be alive to see that, though probably retired.
There are lots of reasons to suspect that this event will come both sooner and later.
It could come sooner if storage merges with memory. We are moving away from rotating platters of rust toward solid-state Continue reading
Bringing “docker scan” to Linux
At the end of last year we launched vulnerability scanning options as part of the Docker platform. We worked together with our partner Snyk to include security testing options along multiple points of your inner loop. We incorporated scanning options into the Hub, so that you can configure your repositories to automatically scan all the pushed images. We also added a scanning command to the Docker CLI on Docker Desktop for Mac and Windows, so that you can run vulnerability scans for images on your local machine. The earlier in your development that you find these vulnerabilities, the easier and cheaper it is to fix them. Vulnerability scan results also provide remediation guidance on things that you can do to remove the reported vulnerabilities. Some of the examples of remediation include recommendations for alternative base images with lower vulnerability counts, or package upgrades that have already resolved the specified vulnerabilities.
We are now making another update in our security journey, by bringing “docker scan” to the Docker CLI on Linux. The experience of scanning on Linux is identical to what we have already launched for Desktop CLI, with scanning support for linux/amd64 (x86-64) Docker images. The Continue reading
Network-based policies in Cloudflare Gateway
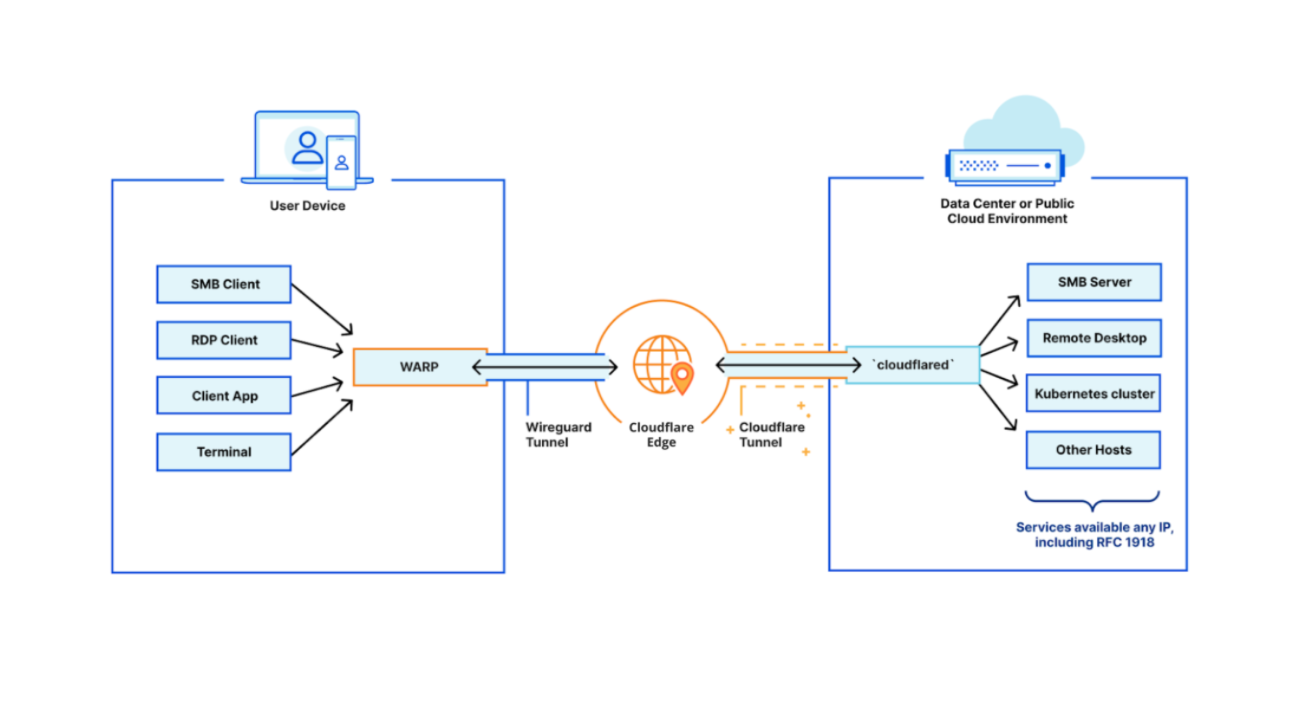
Over the past year, Cloudflare Gateway has grown from a DNS filtering solution to a Secure Web Gateway. That growth has allowed customers to protect their organizations with fine-grained identity-based HTTP policies and malware protection wherever their users are. But what about other Internet-bound, non-HTTP traffic that users generate every day — like SSH?
Today we’re excited to announce the ability for administrators to configure network-based policies in Cloudflare Gateway. Like DNS and HTTP policy enforcement, organizations can use network selectors like IP address and port to control access to any network origin.
Because Cloudflare for Teams integrates with your identity provider, it also gives you the ability to create identity-based network policies. This means you can now control access to non-HTTP resources on a per-user basis regardless of where they are or what device they’re accessing that resource from.
A major goal for Cloudflare One is to expand the number of on-ramps to Cloudflare — just send your traffic to our edge however you wish and we’ll make sure it gets to the destination as quickly and securely as possible. We released Magic WAN and Magic Firewall to let administrators replace MPLS connections, define routing decisions, and apply packet-based Continue reading
Illusory Correlation and Security
Fear sells. Fear of missing out, fear of being an imposter, fear of crime, fear of injury, fear of sickness … we can all think of times when people we know (or worse, a people in the throes of madness of crowds) have made really bad decisions because they were afraid of something. Bruce Schneier has documented this a number of times. For instance: “it’s smart politics to exaggerate terrorist threats” and “fear makes people deferential, docile, and distrustful, and both politicians and marketers have learned to take advantage of this.” Here is a paper comparing the risk of death in a bathtub to death because of a terrorist attack—bathtubs win.
But while fear sells, the desire to appear unafraid also sells—and it conditions people’s behavior much more than we might think. For instance, we often say of surveillance “if you have done nothing wrong, you have nothing to hide”—a bit of meaningless bravado. What does this latter attitude—“I don’t have anything to worry about”—cause in terms of security?
Several attempts at researching this phenomenon have come to the same conclusion: average users will often intentionally not use things they see someone they perceive as paranoid using. Continue reading
QUIC Version 1 is live on Cloudflare


On May 27 2021, the Internet Engineering Task Force published RFC 9000 - the standardarized version of the QUIC transport protocol. The QUIC Working Group declared themselves done by issuing a Last Call 7 months ago. The i's have been dotted and the t's crossed, RFC 8999 - RFC 9002 are a suite of documents that capture years of engineering design and testing of QUIC. This marks a big occasion.
And today, one day later, we’ve made the standardized version of QUIC available to Cloudflare customers.
Transport protocols have a history of being hard to deploy on the Internet. QUIC overcomes this challenge by basing itself on top of UDP. Compared to TCP, QUIC has security by default, protecting almost all bytes from prying eyes or "helpful" middleboxes that can end up making things worse. It has designed-in features that speed up connection handshakes and mitigate the performance perils that can strike on networks that suffer loss or delays. It is pluggable, providing clear standardised extensions point that will allow smooth, iterative development and deployment of new features or performance enhancements for years to come.
The killer feature of QUIC, however, is that it is deployable in reality. We are Continue reading
How to Protect Azure VMware Solution Resources with Azure Application Gateway
Azure VMware Solution (AVS) is a VMware validated private cloud solution managed and maintained by Azure. It runs on dedicated bare-metal Azure infrastructure. AVS allows customers to manage and secure applications across VMware environments and Microsoft Azure with a consistent operating framework. It supports workload migration, VM deployment, and Azure service consumption.
As AVS private cloud runs on an isolated Azure environment, it is not accessible from Azure or the Internet by default. Users can use either ExpressRoute Global Reach (i.e., from on-prem) or a jump box (i.e., on an Azure VNet) to access AVS private cloud. This means AVS workload VMs are confined within AVS private cloud and not accessible from the Internet.
But what if customers want to make AVS Private Cloud resources, such as web servers, accessible from the Internet? In that case, Public IP needs to be deployed. There are couple of ways to do this: (1) Azure Application Gateway, and (2) Destination NAT or DNAT using Azure WAN Hub and Firewall. Azure Application Gateway is Continue reading
Learn from industry experts at the Kubernetes Security and Observability Summit—next week!
The Kubernetes Security and Observability Summit is only 1 week away! The industry’s first and only conference solely focused on Kubernetes security and observability will be taking place online June 3, 2021.
During the Summit, DevOps, SREs, platform architects, and security teams will enjoy the chance to network with industry experts and explore trends, strategies, and technologies for securing, observing and troubleshooting cloud-native applications.
What does security and observability mean in a cloud-native context? What challenges should Kubernetes practitioners anticipate and what opportunities should they investigate? Join us to explore these types of questions and gain valuable insight you’ll be able to take back to your teams.
Speakers & sessions
Tigera’s President & CEO, Ratan Tipirneni, will kick off the Summit with an opening keynote address. Two additional keynotes from Graeme Hay of Morgan Stanley and Keith Neilson of Discover Financial Services will follow. Attendees will then have the opportunity to attend breakout sessions organized into three tracks:
- Stories from the real world
- Best practices
- Under the hood
During these sessions, experts from industry-leading companies like Amazon, Box, Citi, EY, Mirantis, Morgan Stanley, PayPal, Salesforce, and of course, Tigera, will share real-world stories, best practices, and technical concepts related to Continue reading
Cloudflare’s SOC as a Service
When Cloudflare started, sophisticated online security was beyond the reach of all but the largest organizations. If your pockets were deep enough, you could buy the necessary services — and the support that was required to operate them — to keep your online operations secure, fast, and reliable. For everyone else? You were out of luck.
We wanted to change that: to help build a better Internet. To build a set of services that weren’t just technically sophisticated, but easy to use. Accessible. Affordable. Part of this meant that we were always looking to build and equip our customers with all the tools they needed in order to do this for themselves.
Of course, a lot has changed since we started. The Internet has only increased in importance, fast becoming the most important channel for many businesses. Cybersecurity threats have only become more prevalent — and more sophisticated. And the products that Cloudflare offers to keep you safe on the Internet have attracted some of the largest and most recognizable organizations in the world.
Ask some of these larger organizations about cybersecurity, and they’ll tell you a few things: first, they love our products. But, second, that when something happens Continue reading
Data Center Threats: Turning Remote Access into Money
Data centers are an appealing target for cybercriminals. Even though they may be more difficult to compromise than the home computer of a kid playing Fortnite or the laptop of a sales representative connecting to a random wireless network, they can bring very large rewards: databases with millions of records containing financial and personal information, substantial computational resources that can be used to mine cryptocurrencies, and access to key assets that can be held for ransom.
In this blog post, we analyze the main pathways that cybercriminals leverage to gain access to data centers, how they take advantage of that access, and what security administrators can do to reduce and manage the associated risks.
Getting into the Data Center
The obvious first goal of an attacker is to gain access to the targeted data center. This can be achieved in several ways — including social engineering [1], physical access [2], and occasionally by deer [3]— but anecdotal evidence suggests that the two main avenues are remote exploitation (also known as remote-to-local attacks [4]), and stolen credentials [5].
Remote-to-local Attacks
In a remote-to-local attack, an attacker targets a remotely accessible service provided by one of the workloads running in the data Continue reading
Why you don’t want to miss the upcoming Kubernetes Security and Observability Summit
The inaugural Kubernetes Security and Observability Summit will be a free, live, online experience full of Kubernetes-related security and observability content. On June 3, 2021, industry experts will gather under one virtual roof to discuss trends, strategies, and technologies for Kubernetes security and observability, to help you understand and navigate today’s pressing issues in the world of cloud-native applications.
Why attend?
The Summit is a great opportunity to:
- Network with the industry’s best security, DevOps, and site reliability engineer (SRE) teams for cloud-native platforms
- Learn how to secure, observe, and troubleshoot Kubernetes environments
- Explore real-world Kubernetes security and observability use cases presented by experts from industry-leading companies like Amazon, Box, Citi, EY, Mirantis, Morgan Stanley, PayPal, Salesforce, and of course, Tigera
Who should attend?
SREs, platform architects, and DevOps and security teams will all find value in attending the Summit.
- DevOps teams and SREs – Learn how to include security and observability in your CI/CD to enable security, observability, and troubleshooting
- Platform architects – Learn architecture patterns and best practices to secure and troubleshoot cloud-native applications
- Security teams – Learn how to holistically secure your cloud-native applications following today’s best practices
Speakers & sessions
An opening keynote address from Continue reading