A quick FAQ about NFTs
I thought I'd write up 4 technical questions about NFTs. They may not be the ones you ask, but they are the ones you should be asking. The questions:
- What does the token look like?
- How does it contain the artwork? (or, where is the artwork contained?)
- How are tokens traded? (How do they get paid? How do they get from one account to another?)
- What does the link from token to artwork mean? Does it give copyrights?
#1 What does the token look like?
An NFT token has a unique number, analogous to:
- your social security number (SSN#)
- your credit card number
- the VIN# on your car
- the serial number on a dollar bill
- etc.
This unique number is composed of two things:
- the contract number, identifying the contract that manages the token
- the unique token identifier within that contract
Announcing API Abuse Detection


APIs are incredibly important. Throughout the 2000s, they formed the backbone of popular web services, helping the Internet become more useful and accessible. In the 2010s, APIs played a larger role in our lives, allowing personal devices to communicate with the digital world. Many of our daily activities, like using rideshare services and paying for lattes, are dependent on this form of modern communication. Now we are approaching a post-pandemic world in which APIs will be more important than ever.
Unfortunately, as any technology grows, so does its surface area for abuse. APIs are no exception. Competing rideshare services might monitor each other’s prices via API, spawning a price war and a waste of digital resources. Or a coffee drinker might manipulate an API for a latte discount. Some companies have thousands of APIs — including ones that they don’t even know about. Cloudflare can help solve these problems.
Today, we are announcing early access to API Discovery and API Abuse Detection.
Background
Before going further, it’s important to explain why we need a solution for APIs. Traditional security tools, including Rate Limiting and DDoS Protection, can be wonderfully useful. But these approaches were not built to act Continue reading
Protecting Cloudflare Customers from BGP Insecurity with Route Leak Detection
Border Gateway Protocol (BGP) route leaks and hijacks can ruin your day — BGP is insecure by design, and incorrect routing information spreading across the Internet can be incredibly disruptive and dangerous to the normal functioning of customer networks, and the Internet at large. Today, we're excited to announce Route Leak Detection, a new network alerting feature that tells customers when a prefix they own that is onboarded to Cloudflare is being leaked, i.e., advertised by an unauthorized party. Route Leak Detection helps protect your routes on the Internet: it tells you when your traffic is going places it’s not supposed to go, which is an indicator of a possible attack, and reduces time to mitigate leaks by arming you with timely information.
In this blog, we will explain what route leaks are, how Cloudflare Route Leak Detection works, and what we are doing to help protect the Internet from route leaks.
What are route leaks and why should I care?
A route leak occurs when a network on the Internet tells the rest of the world to route traffic through their network, when the traffic isn’t supposed to go there normally. A great example of this Continue reading
Cloudflare’s New Magic WAN Is A Familiar Trick
Cloudflare is building out its network and security services offerings to compete with SASE and CASB providers. The new Magic WAN and Magic Firewall offerings let customers direct traffic from branch offices, remote workers, and data centers to Cloudlfare's infrastructure for WAN transport and security inspection.
The post Cloudflare’s New Magic WAN Is A Familiar Trick appeared first on Packet Pushers.
Witness VMware Disrupt Enterprise Data Center Security at XFD5
The security industry needs to wake up. Today’s attackers are too numerous and too determined to get caught by simple perimeter defenses. It’s no longer a matter of if an attack will be successful, it’s a matter of when. Security pros need to recognize this reality, stop using archaic detect and respond approaches to secure the enterprise, and start focusing on blocking the spread of attacks once they make that initial breach.
Changing the industry won’t be easy. It will require a bold step — one that we believe we’ve taken at VMware with our distributed, software-defined approach to enterprise security. This approach gives us the ability to operationalize east-west security at scale, simplify the implementation of segmentation in just a few steps, and insert advanced threat prevention inside the data center.
We’ll showcase these latest security advances on Thursday, March 25, starting at at 2:00 pm PST. Broadcasting live around the world during Security Field Day 5, NSX security experts will run through simple, practical steps that security teams can take to meet Continue reading
Browser Isolation for teams of all sizes

Every Internet-connected organization relies on web browsers to operate: accepting transactions, engaging with customers, or working with sensitive data. The very act of clicking a link triggers your web browser to download and execute a large bundle of unknown code on your local device.

IT organizations have always been on the back foot while defending themselves from security threats. It is not a question of ‘if’, but ‘when’ the next zero-day vulnerability will compromise a web browser. How can IT organizations protect their users and data from unknown threats without over-blocking every potential risk? The solution is to shift the burden of executing untrusted code from the user’s device to a remote isolated browser.
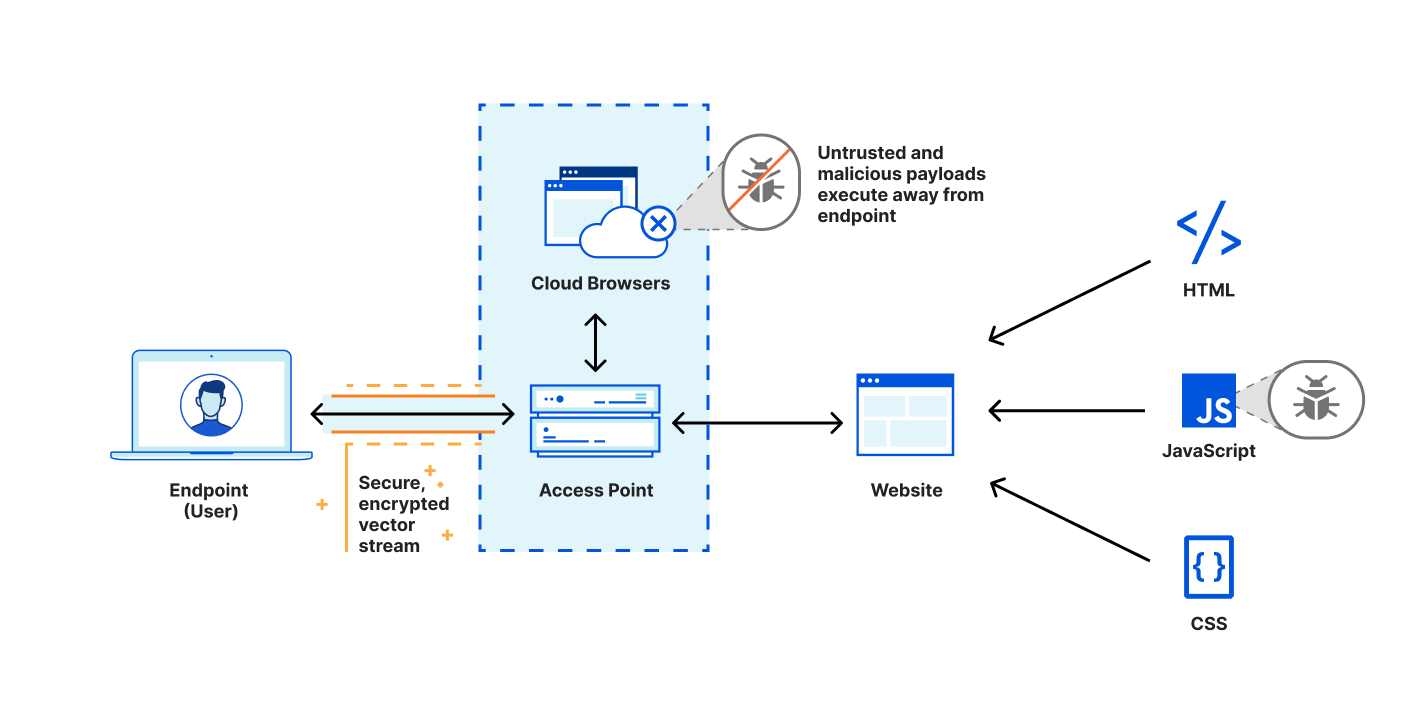
Bringing Remote Browser Isolation to teams of any size
Today we are excited to announce that Cloudflare Browser Isolation is now available within Cloudflare for Teams suite of zero trust security and secure web browsing services as an add-on. Teams of any size from startups to large enterprises can benefit from reliable and safe browsing without changing their preferred web browser or setting up complex network topologies.
Remote Browsers must be reliable
Running sensitive workloads in secure environments is nothing new, and Remote Browser Isolation (RBI) Continue reading
Announcing antivirus in Cloudflare Gateway

Today we’re announcing support for malware detection and prevention directly from the Cloudflare edge, giving Gateway users an additional line of defense against security threats.
Cloudflare Gateway protects employees and data from threats on the Internet, and it does so without sacrificing performance for security. Instead of backhauling traffic to a central location, Gateway customers connect to one of Cloudflare’s data centers in 200 cities around the world where our network can apply content and security policies to protect their Internet-bound traffic.
Last year, Gateway expanded from a secure DNS filtering solution to a full Secure Web Gateway capable of protecting every user’s HTTP traffic as well. This enables admins to detect and block not only threats at the DNS layer, but malicious URLs and undesired file types as well. Moreover, admins now have the ability to create high-impact, company-wide policies that protect all users with one click, or they can create more granular rules based on user identity.
Earlier this month, we launched application policies in Cloudflare Gateway to make it easier for administrators to block specific web applications. With this feature, administrators can block those applications commonly used to distribute malware, such as public cloud file storage.
These Continue reading
Announcing Network On-ramp Partners for Cloudflare One
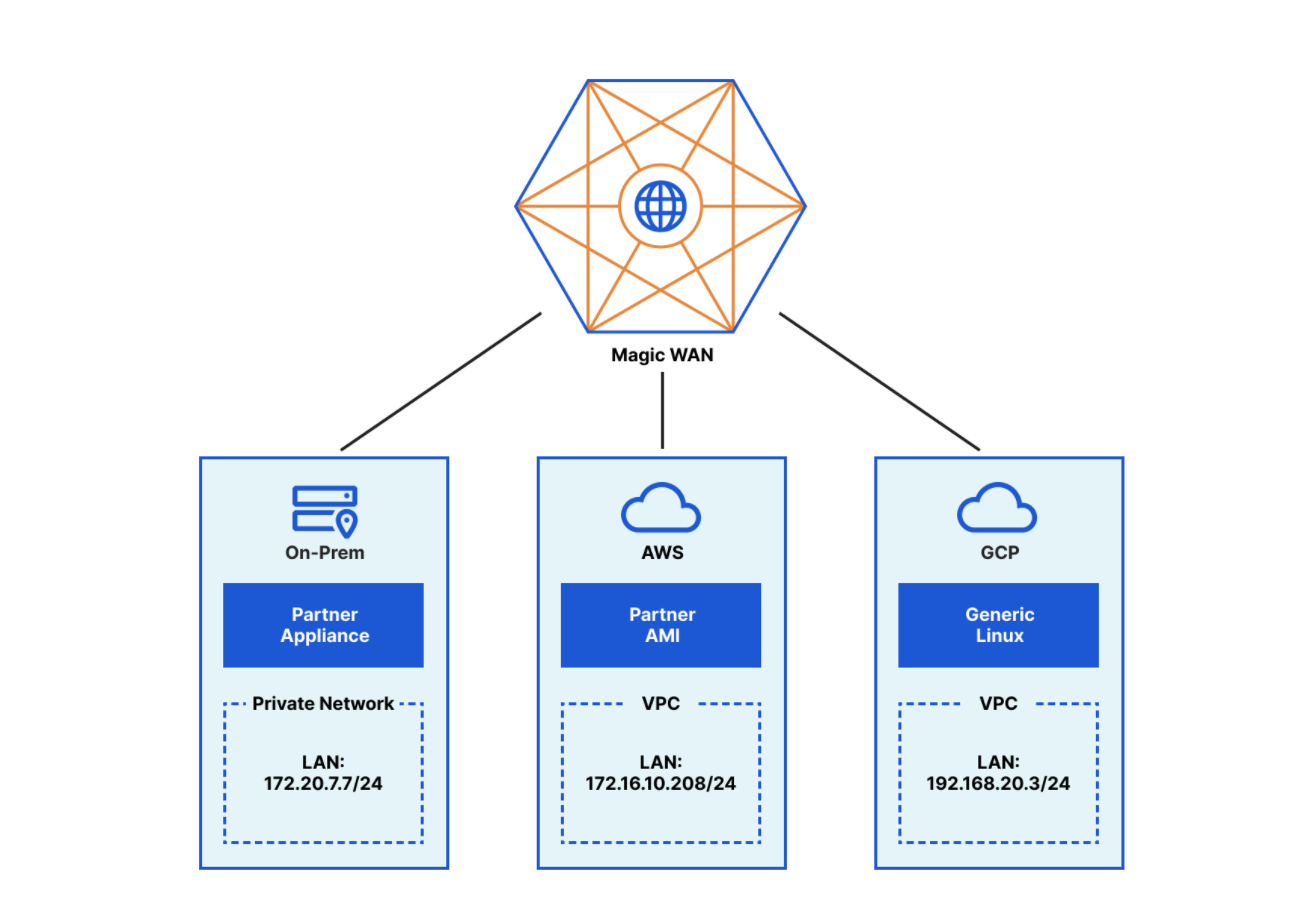
Today, we’re excited to announce our newest Network On-ramp Partnerships for Cloudflare One. Cloudflare One is designed to help customers achieve a secure and optimized global network. We know the promise of replacing MPLS links with a global, secure, performant and observable network is going to transform the corporate network. To realize this vision, we’re launching partnerships so customers can connect to Cloudflare’s global network from their existing trusted WAN & SD-WAN appliances and privately interconnect via the data centers they are co-located in.
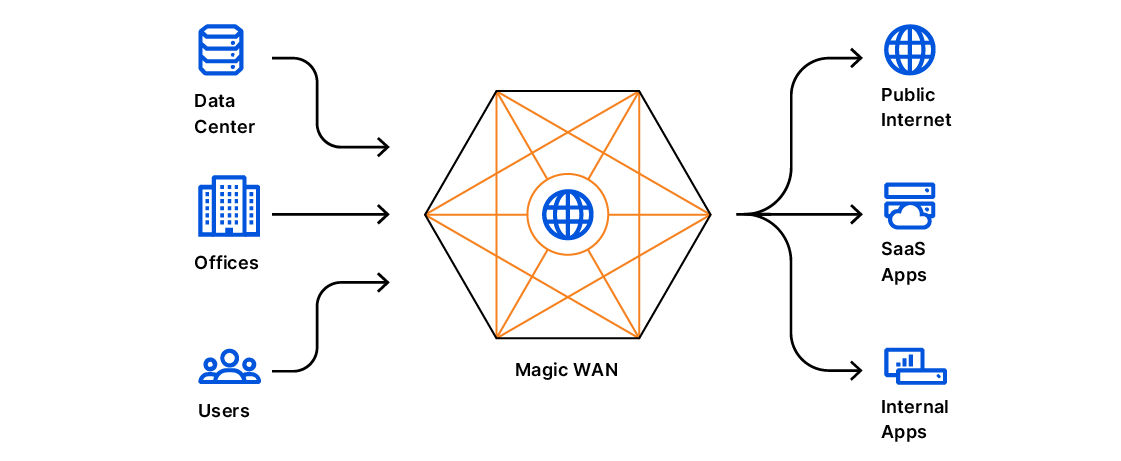
Today, we are launching our WAN and SD-WAN partnerships with VMware, Aruba and Infovista. We are also adding Digital Realty, CoreSite, EdgeConneX, 365 Data Centers, BBIX, Teraco and Netrality Data Centers to our existing Network Interconnect partners Equinix ECX, Megaport, PacketFabric, PCCW ConsoleConnect and Zayo. Cloudflare’s Network On-ramp partnerships now span 15 leading connectivity providers in 70 unique locations, making it easy for our customers to get their traffic onto Cloudflare in a secure and performant way, wherever they are.

Connect to Cloudflare using your existing WAN or SD-WAN Provider
With Magic WAN, customers can securely connect data centers, offices, devices and cloud properties to Cloudflare’s network and configure routing policies Continue reading
pygnmi 9. The safest way to store credentials for network devices.
Hello my friend,
Recently we were asked, what is the safest way to store the credentials for network devices to your automation tools (e.g., the one based on Python and gNMI). Building the network automation solutions for a while, we have a good answer to you.
2
3
4
5
retrieval system, or transmitted in any form or by any
means, electronic, mechanical or photocopying, recording,
or otherwise, for commercial purposes without the
prior permission of the author.
What is the most promising network automation protocol ?
gNMI was created by Google to manage their data centres and backbone network and is widely used by other biggest companies worldwide. However, it doesn’t mean that only the big guys can benefit from that. Every company and network can get the advantage of a single protocol for the configuration, operation, and streaming telemetry in their network provided your network devices support that.
At our trainings, advanced network automation and automation with Nornir (2nd step after advanced network automation), we give you detailed knowledge of all the technologies relevant:
- Data encoding (free-text, XML, JSON, YAML, Protobuf)
- Model-driven network automation Continue reading
Welcome to Cloudflare Security Week 2021!
Today kicks off Cloudflare's 2021 Security Week. Like all innovation weeks at Cloudflare, we'll be announcing a dizzying number of new products, opening products that have been in beta to general availability, and talking to customers and through use cases on how to use our network to fulfill our mission of helping build a better Internet.
In Cloudflare's early days, I resisted the label of being a "security company." It seemed overly limiting. Instead, we were setting out to fix the underlying "bugs" of the Internet. The Internet was never built for what it's become. We started Cloudflare to fix that. Being more secure was table stakes, but we also wanted to make the Internet faster, more reliable, and more efficient.
But a lot of what we do is about security. Approximately half our products are security related. And that makes sense because some of the Internet's deepest flaws are that it specifically did not engineer in security from the beginning.
Security: The Internet’s Afterthought
John Graham-Cumming, Cloudflare's CTO, gives a terrific talk about how the Internet we all have come to rely on wasn’t designed to have the security we all need. In Tim Berners-Lee's original proposal for Continue reading
Deconstructing that $69million NFT
"NFTs" have hit the mainstream news with the sale of an NFT based digital artwork for $69 million. I thought I'd write up an explainer. Specifically, I deconstruct that huge purchase and show what actually was exchanged, down to the raw code. (The answer: almost nothing).
The reason for this post is that every other description of NFTs describe what they pretend to be. In this blogpost, I drill down on what they actually are.
Note that this example is about "NFT artwork", the thing that's been in the news. There are other uses of NFTs, which work very differently than what's shown here.
tl;dr
I have long bit of text explaining things. Here is the short form that allows you to drill down to the individual pieces.
- Beeple created a piece of art in a file
- He created a hash that uniquely, and unhackably, identified that file
- He created a metadata file that included the hash to the artwork
- He created a hash to the metadata file
- He uploaded both files (metadata and artwork) to the IPFS darknet decentralized file sharing service
- He created, or minted a token governed by the MakersTokenV2 smart contract on the Ethereum blockchain
- Christies Continue reading
The History of Identity with Pamela Dingle

While identity is not directly a networking technology, it is closely adjacent to networking, and a critical part of the Internet’s architecture. In this episode of the History of Networking, Pamela Dingle joins Donald Sharpe and Russ White to discuss the humble beginnings of modern identity systems, including NDS and Streettalk.
pygnmi 8. Securing the gNMI connectivity with self-signed certificates.
Hello my friend,
Continuing our explanation of the pyGNMI, we’ll take a loon into the security aspect of the tool. Namely, we will take a look how quickly and easily you can implement the encryption between your host running pyGNMI and the gNMI speaking network function.
2
3
4
5
retrieval system, or transmitted in any form or by any
means, electronic, mechanical or photocopying, recording,
or otherwise, for commercial purposes without the
prior permission of the author.
Where is the GNMI in the Network Automation?
The automation world (network and not only) can at a high level be split into text-based automation and model-driven automation. The text based automation is all about Linux systems, where we typically template the whole configuration files, put them in the corresponding folders and then restart daemons. The model driven approach is where we communicate with the network devices using the NETCONF, RESTCONF or gNMI based on the YANG modules. At the current moment, gNMI is most dynamically developing protocol. We not only teaches you how it works and when to use it, but we also created a Python library, Continue reading
About the March 8 & 9, 2021 Verkada camera hack

Cloudflare uses a vendor called Verkada for cameras in our offices in San Francisco, Austin, New York, London and Singapore. These cameras are used at the entrances, exits and main thoroughfares of our offices and have been part of maintaining the security of offices that have been closed for almost a year.
Yesterday, we were notified of a breach of Verkada that allowed a hacker to access Verkada’s internal support tools to manage those cameras remotely, as well as access them through a remote root shell. As soon as we were notified of the breach, we proceeded to shut down the cameras in all our office locations to prevent further access.
To be clear: this hack affected the cameras and nothing else. No customer data was accessed, no production systems, no databases, no encryption keys, nothing. Some press reports indicate that we use a facial recognition feature available in Verkada. This is not true. We do not.
Our internal systems follow the same Zero Trust model that we provide to our customers, and as such our corporate office networks are not implicitly trusted by our other locations or data centers. From a security point of view connecting from one of Continue reading
Curiefense, A New Open Source Web App Firewall, Tackles Cloud-Native Security
Curiefense is a new, open source Web application firewall designed for cloud-native environments. Currently a "sandbox" project in the Cloud Native Computing Foundation, Curiefense is now generally available.
The post Curiefense, A New Open Source Web App Firewall, Tackles Cloud-Native Security appeared first on Packet Pushers.
SEC 4. Complete guide for integrating Nokia, Arista, Cumulus, as well as CentOS and Raspberry PI Linux in your own PKI
Hello my friend,
In one of the previous blogposts we have share the details how you can build the containerised PKI relying Docker, Alpine Linux and OpenSSL. Today we’ll show how you can use it.
2
3
4
5
retrieval system, or transmitted in any form or by any
means, electronic, mechanical or photocopying, recording,
or otherwise, for commercial purposes without the
prior permission of the author.
How automation can increase the security?
In one of the recent articles dedicated to threats to the national security with respect to 5G caused by the current operation models in the big service providers, one the network automation were named as one of the key mitigation approaches. The reason is very simple: network automation allows you to keep (or even increase) the pace of the network changes with increasing the stability without increasing the size of your network operation teams.
We absolutely agree with this statement. We have observed ourselves that in many cases the key technical competence for service providers is being outsourced and in certain cases the service providers have to rely on the external parties to perform Continue reading
Cracking WPA/WPA2 Pre-shared Key
This tutorial illustrates cracking of pre-shared key which is needed to gain an access to a WPA/WPA2 network. Instead of explaining the theory behind the attack, I focus on providing commands that you can easily copy and paste and penetrate the network. However, I strongly recommend getting a background to this topic by studying online […]Continue reading...
We are living in 1984 (ETERNALBLUE)
In the book 1984, the protagonist questions his sanity, because his memory differs from what appears to be everybody else's memory.
The Party said that Oceania had never been in alliance with Eurasia. He, Winston Smith, knew that Oceania had been in alliance with Eurasia as short a time as four years ago. But where did that knowledge exist? Only in his own consciousness, which in any case must soon be annihilated. And if all others accepted the lie which the Party imposed—if all records told the same tale—then the lie passed into history and became truth. ‘Who controls the past,’ ran the Party slogan, ‘controls the future: who controls the present controls the past.’ And yet the past, though of its nature alterable, never had been altered. Whatever was true now was true from everlasting to everlasting. It was quite simple. All that was needed was an unending series of victories over your own memory. ‘Reality control’, they called it: in Newspeak, ‘doublethink’.
I know that EternalBlue didn't cause the Baltimore ransomware attack. When the attack happened, the entire cybersecurity community agreed that EternalBlue wasn't responsible.
But this New York Times article said otherwise, blaming the Continue reading
Review: Perlroth’s book on the cyberarms market
New York Times reporter Nicole Perlroth has written a book on zero-days and nation-state hacking entitled “This Is How They Tell Me The World Ends”. Here is my review.
I’m not sure what the book intends to be. The blurbs from the publisher implies a work of investigative journalism, in which case it’s full of unforgivable factual errors. However, it reads more like a memoir, in which case errors are to be expected/forgivable, with content often from memory rather than rigorously fact checked notes.
But even with this more lenient interpretation, there are important flaws that should be pointed out. For example, the book claims the Saudi’s hacked Bezos with a zero-day. I claim that’s bunk. The book claims zero-days are “God mode” compared to other hacking techniques, I claim they are no better than the alternatives, usually worse, and rarely used.
But I can’t really list all the things I disagree with. It’s no use. She’s a New York Times reporter, impervious to disagreement.
If this were written by a tech journalist, then criticism would be the expected norm. Tech is full of factual truths, such as whether 2+2=5, where it’s possible for a thing to be Continue reading
Flow-based monitoring for Magic Transit
Network-layer DDoS attacks are on the rise, prompting security teams to rethink their L3 DDoS mitigation strategies to prevent business impact. Magic Transit protects customers’ entire networks from DDoS attacks by placing our network in front of theirs, either always on or on demand. Today, we’re announcing new functionality to improve the experience for on-demand Magic Transit customers: flow-based monitoring. Flow-based monitoring allows us to detect threats and notify customers when they’re under attack so they can activate Magic Transit for protection.
Magic Transit is Cloudflare’s solution to secure and accelerate your network at the IP layer. With Magic Transit, you get DDoS protection, traffic acceleration, and other network functions delivered as a service from every Cloudflare data center. With Cloudflare’s global network (59 Tbps capacity across 200+ cities) and <3sec time to mitigate at the edge, you’re covered from even the largest and most sophisticated attacks without compromising performance. Learn more about Magic Transit here.
Using Magic Transit on demand
With Magic Transit, Cloudflare advertises customers’ IP prefixes to the Internet with BGP in order to attract traffic to our network for DDoS protection. Customers can choose to use Magic Transit always on or on demand. With always Continue reading