CMC Networks Bolsters SD-WAN with Enea NFV Access
Enea's NFV Access platform will power CMC Network's Rapid Adaptive Network SD-WAN in Africa and the...
Ericsson Bribery Scandal Cuts Deep, Surpassing $1B Penalty
Ericsson expects to pay $1.23 billion to cover a potential settlement and related costs to resolve...
Cisco Warns of ‘Continued Attempts’ to Exploit Critical Bug
Cisco disclosed more than two dozen vulnerabilities in its network automation software and one...
Designing Your First Application in Kubernetes, Part 4: Configuration
I reviewed the basic setup for building applications in Kubernetes in part 1 of this blog series, and discussed processes as pods and controllers in part 2. In part 3, I explained how to configure networking services in Kubernetes to allow pods to communicate reliably with each other. In this installment, I’ll explain how to identify and manage the environment-specific configurations expected by your application to ensure its portability between environments.

Factoring out Configuration
One of the core design principles of any containerized app must be portability. We absolutely do not want to reengineer our containers or even the controllers that manage them for every environment. One very common reason why an application may work in one place but not another is problems with the environment-specific configuration expected by that app.
A well-designed application should treat configuration like an independent object, separate from the containers themselves, that’s provisioned to them at runtime. That way, when you move your app from one environment to another, you don’t need to rewrite any of your containers or controllers; you simply provide a configuration object appropriate to this new environment, leaving everything else untouched.
When we design applications, we need to identify what Continue reading
Deep Dive: How Do Banks Score on Privacy and Security?

In April 2019 the Internet Society’s Online Trust Alliance published its 10th annual Online Trust Audit & Honor Roll assessing the security and privacy of 1,200 top organizations. The Banking sector includes the top 100 banks in the U.S., based on assets according to the Federal Deposit Insurance Corporation (FDIC). Banks had a standout year, with a dramatic increase in scores across the board. Let’s take a closer look.
Overall, 73% of banks made the Honor Roll, putting the banking sector 4th behind the News and Media (78%), Consumer Services (85%), and the U.S. Federal Government (91%) sectors. In the previous Audit, only 27% made the grade. This large jump is due to improvements in all three scoring categories: email authentication, site security, and privacy.
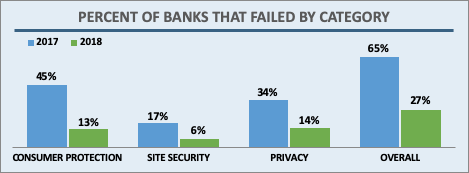
Banks, like most sectors, came close to 100% adoption in the two main email security technologies studied in the Audit: SPF (93%) and DKIM (87%). In addition, banks saw a marked improvement in how many sites implemented both both technologies at 87% in 2018, up from 60% in 2017. This puts banks among the most improved sectors in this area.
DMARC builds on SPF and DKIM results, provides a means for Continue reading
HTTP/3: the past, the present, and the future

During last year’s Birthday Week we announced preliminary support for QUIC and HTTP/3 (or “HTTP over QUIC” as it was known back then), the new standard for the web, enabling faster, more reliable, and more secure connections to web endpoints like websites and APIs. We also let our customers join a waiting list to try QUIC and HTTP/3 as soon as they became available.

Since then, we’ve been working with industry peers through the Internet Engineering Task Force, including Google Chrome and Mozilla Firefox, to iterate on the HTTP/3 and QUIC standards documents. In parallel with the standards maturing, we’ve also worked on improving support on our network.
We are now happy to announce that QUIC and HTTP/3 support is available on the Cloudflare edge network. We’re excited to be joined in this announcement by Google Chrome and Mozilla Firefox, two of the leading browser vendors and partners in our effort to make the web faster and more reliable for all.
In the words of Ryan Hamilton, Staff Software Engineer at Google, “HTTP/3 should make the web better for everyone. The Chrome and Cloudflare teams have worked together closely to bring HTTP/3 and QUIC from nascent standards to widely Continue reading
Volta Networks Virtualizes Routing on Edgecore White Boxes
Volta Networks aims to squeeze legacy vendors’ service provider business by bringing its virtual...
Exploring Cluster API v1alpha2 Manifests
The Kubernetes community recently released v1alpha2 of Cluster API (a monumental effort, congrats to everyone involved!), and with it comes a number of fairly significant changes. Aside from the new Quick Start, there isn’t (yet) a great deal of documentation on Cluster API (hereafter just called CAPI) v1alpha2, so in this post I’d like to explore the structure of the CAPI v1alpha2 YAML manifests, along with links back to the files that define the fields for the manifests. I’ll focus on the CAPI provider for AWS (affectionately known as CAPA).
As a general note, any links back to the source code on GitHub will reference the v0.2.1 release for CAPI and the v0.4.0 release for CAPA, which are the first v1apha2 releases for these projects.
Let’s start with looking at a YAML manifest to define a Cluster in CAPA (this is taken directly from the Quick Start):
apiVersion: cluster.x-k8s.io/v1alpha2
kind: Cluster
metadata:
name: capi-quickstart
spec:
clusterNetwork:
pods:
cidrBlocks: ["192.168.0.0/16"]
infrastructureRef:
apiVersion: infrastructure.cluster.x-k8s.io/v1alpha2
kind: AWSCluster
name: capi-quickstart
---
apiVersion: infrastructure.cluster.x-k8s.io/v1alpha2
kind: AWSCluster
metadata:
name: capi-quickstart
spec:
region: us-east-1
sshKeyName: default
Right off the bat, Continue reading
Hey Dropbox, I Don’t Want The Bloat. Or the Constant Ads.

TL-DR: Dropbox is harassing me about new products. Combined with poor performance of their bloated app and enormous waisting of my disk space, I’m getting close to quitting. I want to use Dropbox to synchronise files between my various devices aka desktop, laptop, tablet and smartphone for quite some time. I like it enough to […]
The post Hey Dropbox, I Don’t Want The Bloat. Or the Constant Ads. appeared first on EtherealMind.
Upcoming Events and Webinars (October 2019)
The autumn 2019 webinar season is in full swing ;) We’re almost done with Azure Networking webinar (the last session will take place on October 10th) and the network automation course is nicely chugging along – a few weeks ago Matthias Luft talked about supply-chain security in open-source software and today we’ll enjoy the start with a single source of truth presentation by Damien Garros.
Dinesh Dutt is coming back on October 8th with another installment of EVPN saga, this time focused on running EVPN on Linux hosts, and on October 22nd Donald Sharp will tell us all about the underlying magic box – the Free Range Routing software.
But there are even more open-source goodies waiting for you: on October 15th we’ll have Pete Lumbis describing the new features Cumulus Linux got in the last year, including AutoBGP and AutoMLAG.
Most everything I mentioned above apart is accessible with Standard ipSpace.net Subscription, and you’ll need Expert Subscription to enjoy the automation course contents.
The Bookshelf
I am a big fan of Audible for books. Every once in a while I have time and patience to read a physical book, but often times I find myself needing to do things like washing dishes, going on a long walk or drive, and Audible has made it so much easier for me to get back into “reading”. Since I started doing this, I’d like to share the books that I’ve been able to get through this way.Matt Oswalt – Portfolio
Short Bio Matt Oswalt hails from Portland, OR, and focuses on the intersection of network infrastructure, automation, systems, and software engineering. He’s passionate about enabling engineers to evolve their careers to the next level, and sharing the bright spots that exist within the technology industry with the masses. You can often find him speaking at conferences or meetups about these topics, as well as writing about them on his blog (https://keepingitclassless.LF Edge Sharpens Its Focus With Baetyl, Fledge
China's Baidu donated the Baetyl seed code, while Dianomic contributed Fledge.
EVPN-PIM: Anycast VTEPs
This is the second of the two part EVPN-PIM blog series exploring the feature and network deployment choices. If you missed part one, learn about BUM optimization using PIM-SM here.
Anycast VTEPs
Servers in a data-center Clos are typically dual connected to a pair of Top-of-Rack switches for redundancy purposes. These TOR switches are setup as a MLAG (Multichassis Link Aggregation) pair i.e. the server sees them as a single switch with two or more bonded links. Really there are two distinct switches with an ISL/peerlink between them syncing databases and pretending to be one.

The MLAG switches (L11, L12 in the sample setup) use a single VTEP IP address i.e. appear as an anycast-VTEP or virtual-VTEP.
Additional procedures involved in EVPN-PIM with anycast VTEPs are discussed in this blog.
EVPN-PIM in a MLAG setup vs. PIM-MLAG
Friend: “So you are working on PIM-MLAG?”
Me: “No, I am implementing EVPN-PIM in a MLAG setup”
Friend: “Yup, same difference”
Me: “No, it is not!”
Friend: “OK, OK, so you are implementing PIM-EVPN with MLAG?”
Me: “Yes!”
Friend: “i.e. PIM-MLAG?”
Me: “Well, now that you put it like that….……..NO, I AM NOT!! Continue reading