TNO002: How Simplification Helps MSPs Scale
Simplification is the theme of today’s episode. Host Scott Robohn and guest Jack Maxfield explore the operational impacts of simplification for a Managed Service Provider (MSP). They discuss the challenges of managing multi-vendor environments and how to use templating and tools to simplify the management process. Proactive client communication and the integration of network and... Read more »Technology Short Take 182
Welcome to Technology Short Take #182! I have a slightly bulkier list of links for you today, bolstered by some recent additions to my RSS feeds and supplemented by some articles I found through social media. There should be enough here to keep folks entertained this weekend—enjoy!
Networking
- New to network automation? Ivan Pepelnjak has made publicly available the materials from his Network Automation 101 course.
- This is an older article from 2020, but still useful: Nathan Taber “demystifies” cluster networking for Amazon EKS worker nodes.
- Ales Brelih provides a reasonably comprehensive introduction to container networking, covering all the significant concepts involved (network namespaces, veth pairs, bridges, and our good friend
iptables). - And here’s another breakdown of network namespaces and container networking.
- Running your own FreeRADIUS implementation to control Wi-Fi access is overkill for me, but for Neil it’s just another day.
- Alexis Ducastel provides some CNI benchmark results.
Servers/Hardware
- I thought this write-up of Andy Bechtolsheim’s keynote at Hot Interconnects 2024 was an interesting summary of where we could see hardware development go in the next 4 years.
- It turns out that Yubikeys—hardware security keys—are subject to a potential cloning vulnerability, although it does require physical access Continue reading
Repost: BGP, EVPN, VXLAN, or SRv6?
Did you know that some vendors use the ancient MPLS/VPN (RFC 4364) control plane when implementing L3VPN with SRv6?
That’s just one of the unexpected tidbits I discovered when explaining why you can’t compare BGP, EVPN, and SRv6.
NOAA Gets $100 Million Windfall For “Rhea” Research Supercomputer
All of the weather and climate simulation centers on Earth are trying to figure out how to use a mixture of traditional HPC simulation and modeling with various kinds of AI prediction to create forecasts for both near-term weather and long-term climate that have higher fidelity and go out further into the future. …
NOAA Gets $100 Million Windfall For “Rhea” Research Supercomputer was written by Timothy Prickett Morgan at The Next Platform.
Network CI/CD Pipeline – GitLab Variables

Hi all, welcome back to our Network CI/CD blog series. In the previous posts, we covered what CI/CD is and why you need it for Network Automation. We also covered GitLab basics and how to set up your first pipeline. In this post, we’ll look into how to keep your credentials secure by hiding them from the repository and using GitLab variables. Let’s get to it!
GitLab Variables
In GitLab CI/CD, variables play an important role in managing dynamic values throughout your pipeline. These variables can store anything from environment-specific settings to sensitive information like credentials. By using variables, you can easily manage and change values without hardcoding them in your scripts or playbooks.
GitLab provides a secure way to store sensitive data such as passwords or API tokens. You can define these variables in your project’s Settings > CI/CD > Variables section, and they will be securely injected into your pipeline during runtime.
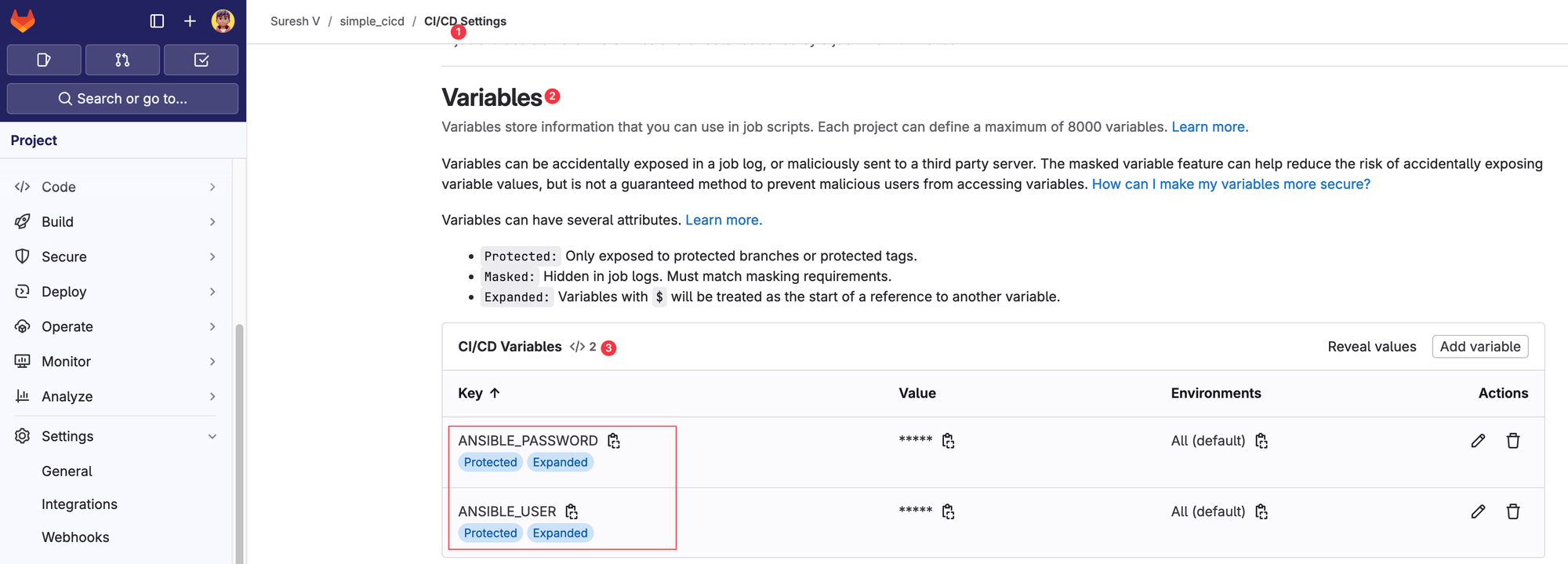
If you recall, in our previous examples, we had the username and password hardcoded in the Ansible variables file. This is not secure at all, and you should never expose sensitive information like credentials directly in your repository. By using GitLab variables, you can securely Continue reading
Hedge 242: The Myth of the Coder
In the early days of computer programming, some thought there was a difference between a coder and a programmer. Did this division ever really exist, and are there similar divisions in network engineering?
Profiting From The GenAI Boom Is Tough Even If It Democratizes
Wall Street might have unreasonable expectations about how OEMs and ODMs can profit from the GenAI boom through selling GPU laden systems. …
Profiting From The GenAI Boom Is Tough Even If It Democratizes was written by Timothy Prickett Morgan at The Next Platform.
Free Network Configuration Backup with Netpicker

Netpicker is a tool that brings together config backups, security/compliance checks, and automation in one place. Netpicker supports 130+ network vendors, including Cisco, Juniper, Arista, Palo Alto, and Fortinet. It also integrates well with tools like Netbox, Nautobot, and Infrahub for inventory, and Slurp’it for network discovery. You can also reuse your existing Python scripts to run checks or automate tasks across your network.
In this post, we'll go through how to set up Netpicker and configure device backups for free. We'll also look at how Netpicker stores these backups and how you can compare or view the diff to see what has changed over time.
Please note that this is a paid article. Netpicker has asked me to write and publish this blog post on their behalf, and I’ve charged a fee for it. As of writing this, Netpicker also sponsors my blog.
Netpicker Initial Setup
To get started, head over to the Netpicker website and fill out the form with your name and email. You’ll receive an email shortly with the download instructions. Netpicker comes with a free-for-life license that gives you unlimited device backups and basic automation. You’ll also get a ‘Professional’ license Continue reading
IPB159: IPv6 Basics – Router Advertisements
Our series on IPv6 basics continues with Router Advertisements (RAs) within the Neighbor Discovery Protocol. We look at how hosts bootstrap onto a network using ICMPv6, discuss the timing of sending out an RA, and then cover the configuration of RAs, including key flags and options. We also talk about the importance of understanding the... Read more »Wireshark tid-bit: Looking for the smoking gun
It’s not always the network which is at fault but it is usually the network that is the assumed culprit. Wireshark can be a vital tool when troubleshooting difficult scenarios or prove that the network is not root cause. The purpose of this post is to ask questions and promote out of the box thinking […]Cloud HPC Is The ‘SilverLining’ in Global Warming Mitigation
PARTNER CONTENT Scientists say the global climate crisis is continuing to intensify, and managing the situation requires increasingly innovative solutions. …
Cloud HPC Is The ‘SilverLining’ in Global Warming Mitigation was written by Timothy Prickett Morgan at The Next Platform.
EVPN Designs: Scaling IBGP with Route Reflectors
In the previous blog posts, we explored the simplest possible IBGP-based EVPN design and tried to figure out whether BGP route reflectors do more harm than good. Ignoring that tiny detail for the moment, let’s see how we could add route reflectors to our leaf-and-spine fabric.
As before, this is the fabric we’re working with:
A global assessment of third-party connection tampering
Have you ever made a phone call, only to have the call cut as soon as it is answered, with no obvious reason or explanation? This analogy is the starting point for understanding connection tampering on the Internet and its impact.
We have found that 20 percent of all Internet connections are abruptly closed before any useful data can be exchanged. Essentially, every fifth call is cut before being used. As with a phone call, it can be challenging for one or both parties to know what happened. Was it a faulty connection? Did the person on the other end of the line hang up? Did a third party intervene to stop the call?
On the Internet, Cloudflare is in a unique position to help figure out when a third party may have played a role. Our global network allows us to identify patterns that suggest that an external party may have intentionally tampered with a connection to prevent content from being accessed. Although they are often hard to decipher, the ways connections are abruptly closed give clues to what might have happened. Sources of tampering generally do not try to hide their actions, which leaves hints of Continue reading
Bringing insights into TCP resets and timeouts to Cloudflare Radar
Cloudflare handles over 60 million HTTP requests per second globally, with approximately 70% received over TCP connections (the remaining are QUIC/UDP). Ideally, every new TCP connection to Cloudflare would carry at least one request that results in a successful data exchange, but that is far from the truth. In reality, we find that, globally, approximately 20% of new TCP connections to Cloudflare’s servers time out or are closed with a TCP “abort” message either before any request can be completed or immediately after an initial request.
This post explores those connections that, for various reasons, appear to our servers to have been halted unexpectedly before any useful data exchange occurs. Our work reveals that while connections are normally ended by clients, they can also be closed due to third-party interference. Today we’re excited to launch a new dashboard and API endpoint on Cloudflare Radar that shows a near real-time view of TCP connections to Cloudflare’s network that terminate within the first 10 ingress packets due to resets or timeouts, which we’ll refer to as anomalous TCP connections in this post. Analyzing this anomalous behavior provides insights into scanning, connection tampering, DoS attacks, connectivity issues, and other behaviors.
MSS, MSS Clamping, PMTUD, and MTU
Maximum Segment Size (MSS) and MSS clamping are concepts that can be confusing. How do they relate to the MTU (Maximum Transmission Unit)? Before we setup a lab to demonstrate these concepts, let’s give some background. Note that this entire post assumes a maximum frame size of 1518 bytes, the original Ethernet definition, and does not cover jumbo frames.
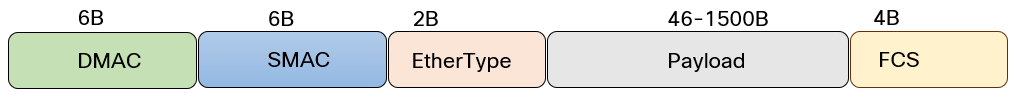
Ethernet frame
Almost all interfaces today are Ethernet. The original 802.3 standard from 1985 defined the minimum size- and maximum size frame as the following:
- minFrameSize – 64 octets.
- maxFrameSize – 1518 octets.
With a maximum frame size of 1518 octets (bytes), that leaves 1500 bytes of payload as the Ethernet frame adds 18 bytes, 14 bytes of header and 4 bytes of trailer. The Ethernet frame is shown below:
IP header
An IPv4 IP header adds at least 20 bytes to the frame. The IPv4 header is shown below:
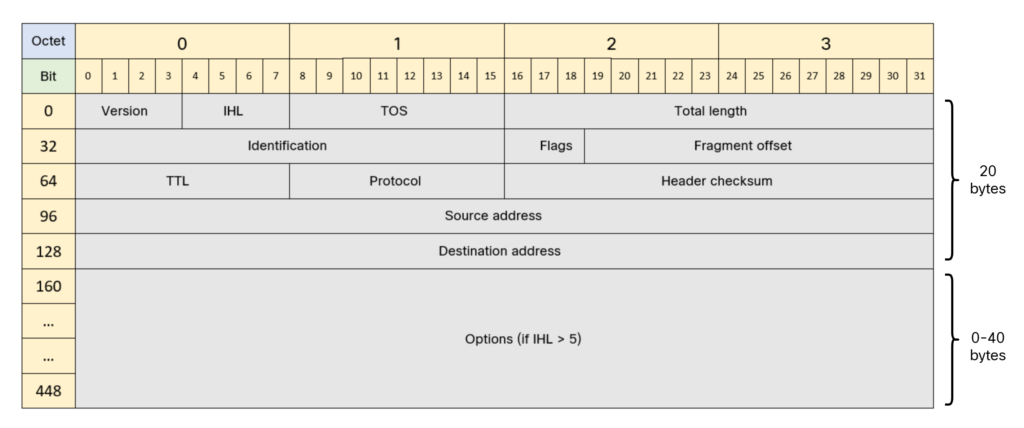
Note that more than 20 bytes can be used if the header has IP options. With no options in the IP header, there’s 1480 bytes remaining for the L4 protocol such as UDP or TCP.
TCP header
TCP also adds a minimum of 20 bytes, meaning that the maximum payload Continue reading
TACC Fires Up “Vista” Bridge To Future “Horizon” Supercomputer
The Texas Advanced Computing Center at the University of Austin is the flagship datacenter for supercomputing for the US National Science Foundation, and so what TACC does – and doesn’t do – is a kind of bellwether for academic supercomputing. …
TACC Fires Up “Vista” Bridge To Future “Horizon” Supercomputer was written by Timothy Prickett Morgan at The Next Platform.
D2DO250: The Realities of Responsible Disclosure in the Cloud
Cloud security and responsible disclosure are the focus of today’s conversation with guest Kat Traxler. Kat shares her insights on identifying vulnerabilities in cloud services, particularly Google Cloud, and the importance of curiosity in her research. The episode explores the role of bug bounty programs and the shift towards issuing CVEs for cloud vulnerabilities. Lastly,... Read more »Routing Table and BGP RIB on SR Linux
Ages ago, I described how “traditional” network operating systems used the BGP Routing Information Base (BGP RIB), the system routing table (RIB), and the forwarding table (FIB). Here’s the TL&DR:
- Routes received from BGP neighbors are stored in BGP RIB.
- Routes redistributed into BGP from other protocols are (re)created in the BGP RIB.
- BGP selects the best routes in BGP RIB using its convoluted set of rules.
- Best routes from the BGP RIB are advertised to BGP neighbors
- Best routes from the BGP RIB compete (based on their administrative distance) against routes from other routing protocols to enter the IP routing table (system RIB)
- Routes from the system RIB are copied into FIB after their next hops are fully evaluated (a process that might involve multiple recursive lookups).