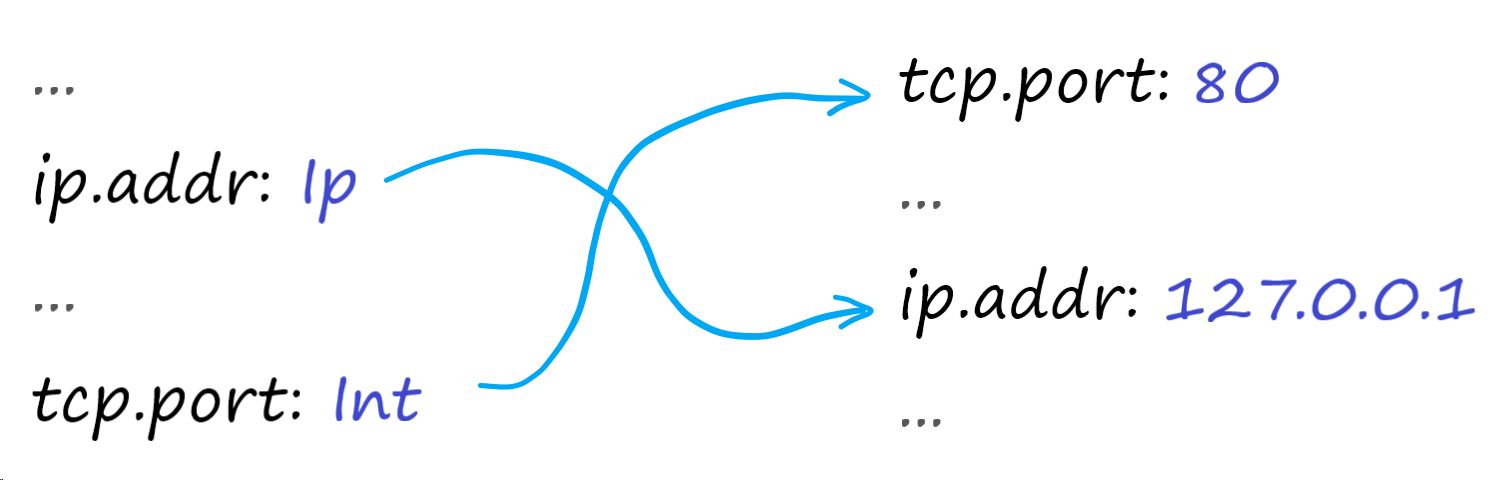
Meet the VMware Service-defined Firewall: A new approach to firewalling
VMware has had front row seats to the digital transformation that has touched virtually every organization. We’ve been there (and helped drive!) the journey from monolithic applications hosted on a single server, to distributed apps running in VMs, to further decentralization in the form of cloud-native apps composed of microservices. Now, we’re watching the proliferation of public clouds, the up and coming space of serverless and the adoption of functions as a service as ways to build and deploy applications faster than ever.
It’s this vantage point that also gives us clear line of sight to one of the biggest cyber security challenges that modern enterprises face: as their applications become more distributed, an organization’s attack surface significantly increases. Despite all of the advancements and innovation in the way applications are built, we have not seen the same rate of progress with respect to the way applications are secured. Adopting a zero-trust network security model in an enterprise environment remains incredibly hard to achieve. How do you know what security policies to create? How do you enforce those policies consistently across on-premises physical and virtual environments, let alone the public cloud? How do you enforce them across different Continue reading
 It uses VMware’s ability to inspect the guest OS and application without being resident in the...
It uses VMware’s ability to inspect the guest OS and application without being resident in the... 5G was by far the biggest talking point at this year's MWC Barcelona event but Huawei did give it a...
5G was by far the biggest talking point at this year's MWC Barcelona event but Huawei did give it a... Edge, the new overhyped term for MWC 2020.
Edge, the new overhyped term for MWC 2020. It’s a cloud service built on Google infrastructure that lets companies upload, store, and...
It’s a cloud service built on Google infrastructure that lets companies upload, store, and... AT&T ties its 5G and Airship plans to the Mirantis core; the Linux community uncovers a runC...
AT&T ties its 5G and Airship plans to the Mirantis core; the Linux community uncovers a runC... The plan calls for the government to take wireless spectrum from the Defense Department and use a...
The plan calls for the government to take wireless spectrum from the Defense Department and use a... Juniper CEO called the purchase an "offensive move" against its networking competitors, namely...
Juniper CEO called the purchase an "offensive move" against its networking competitors, namely... Falcon for Mobile identifies threats on mobile devices and provides visibility into situations...
Falcon for Mobile identifies threats on mobile devices and provides visibility into situations... The demonstration is using open APIs to connect the entire system to a programmable optical network...
The demonstration is using open APIs to connect the entire system to a programmable optical network... Alliance members will demonstrate how their products and services work together to secure...
Alliance members will demonstrate how their products and services work together to secure...