Segment Routing and MPLS VPN
MPLS VPN and Segment Routing. Many people have been asking what are the differences between MPLS VPN and Segment Routing. In fact, this is a wrong question, because Segment Routing provides transport, MPLS VPN provides Service. They are not mutually exclusive but they are complementary. In order to create end to …
Continue reading "Segment Routing and MPLS VPN"
The post Segment Routing and MPLS VPN appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.
 Despite saying VMware should be worth $300 per share, and filing a lawsuit against Dell to stop the deal, Icahn late today issued a statement that essentially says he’s done fighting.
Despite saying VMware should be worth $300 per share, and filing a lawsuit against Dell to stop the deal, Icahn late today issued a statement that essentially says he’s done fighting. It was the company's second quarter of 50 percent-plus growth in India.
It was the company's second quarter of 50 percent-plus growth in India. The Data Lakes Analytics service helps customers that need cloud-native analytics and need to turn raw data into real-time insights.
The Data Lakes Analytics service helps customers that need cloud-native analytics and need to turn raw data into real-time insights. The collaboration will initially use IBM’s Blockchain Platform to improve reliability and transparency of information collected by different networks when routing international calls.
The collaboration will initially use IBM’s Blockchain Platform to improve reliability and transparency of information collected by different networks when routing international calls. At a recent investor conference both AT&T and Verizon said that 5G won’t have an impact on their revenues until at least 2020.
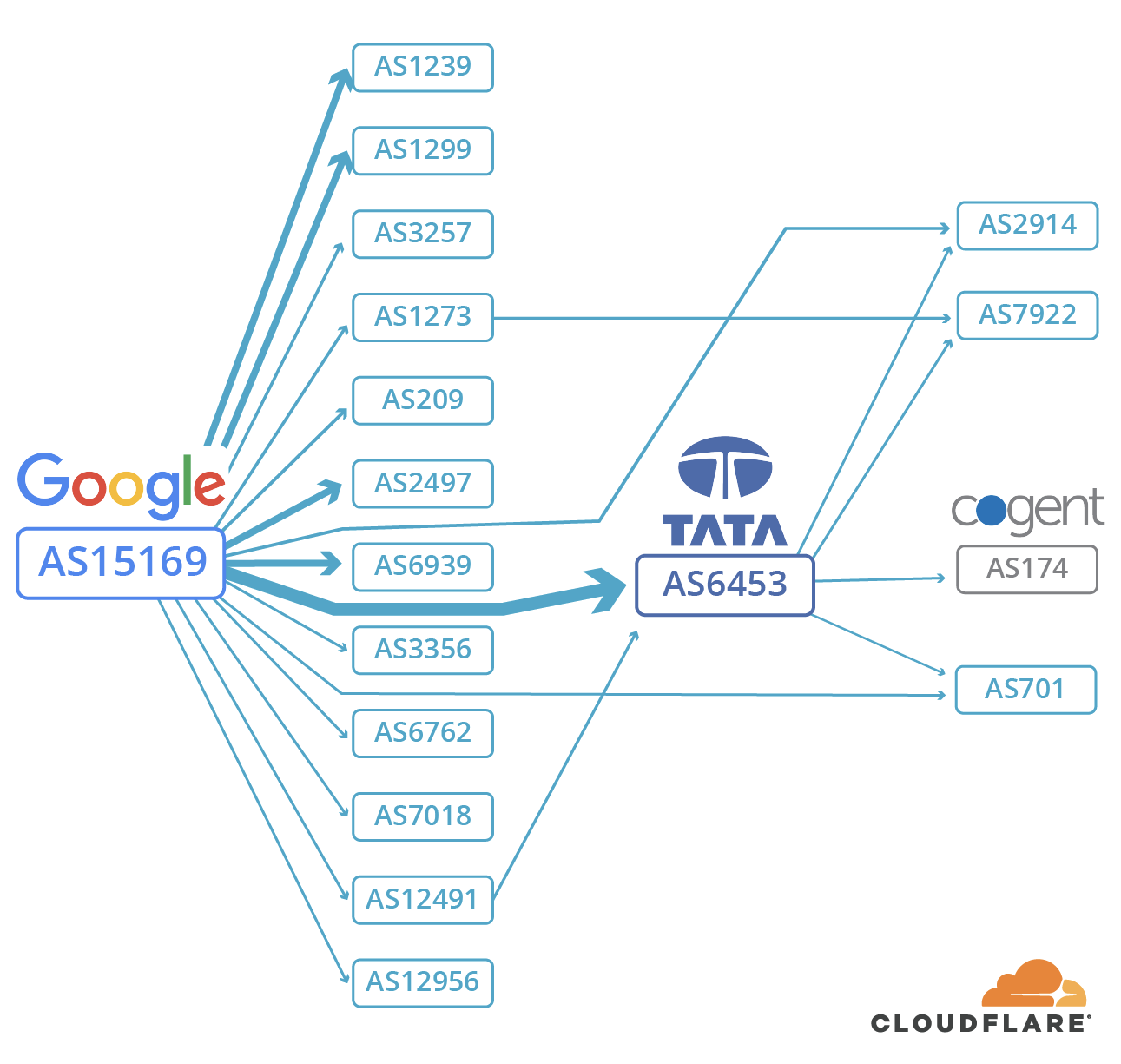
At a recent investor conference both AT&T and Verizon said that 5G won’t have an impact on their revenues until at least 2020.




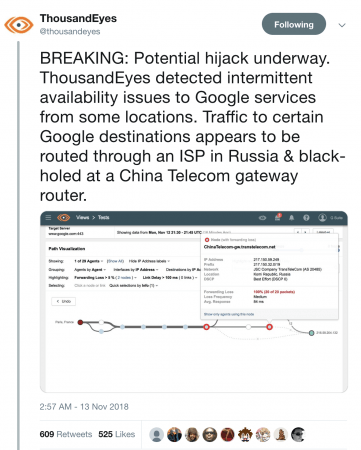
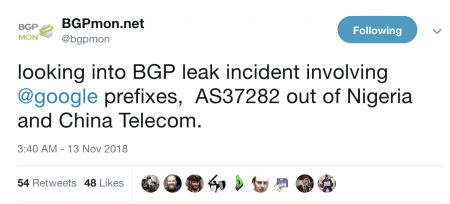
 The latest update uses an in-house developed open source version of OpenStack that provides for more agility and a smaller footprint to support edge computing environments.
The latest update uses an in-house developed open source version of OpenStack that provides for more agility and a smaller footprint to support edge computing environments.