No Scripting Required to Start Your Automation Journey
The “everyone should be a programmer” crowd did a really good job of scaring network engineers (congratulations, just what we need!). Here’s a typical question I’m getting:
Do I need to be good in scripting to attend your automation course.
TL&DR: Absolutely not.
Read more ...Setting Up Addressing and Routing: FTDv Fun
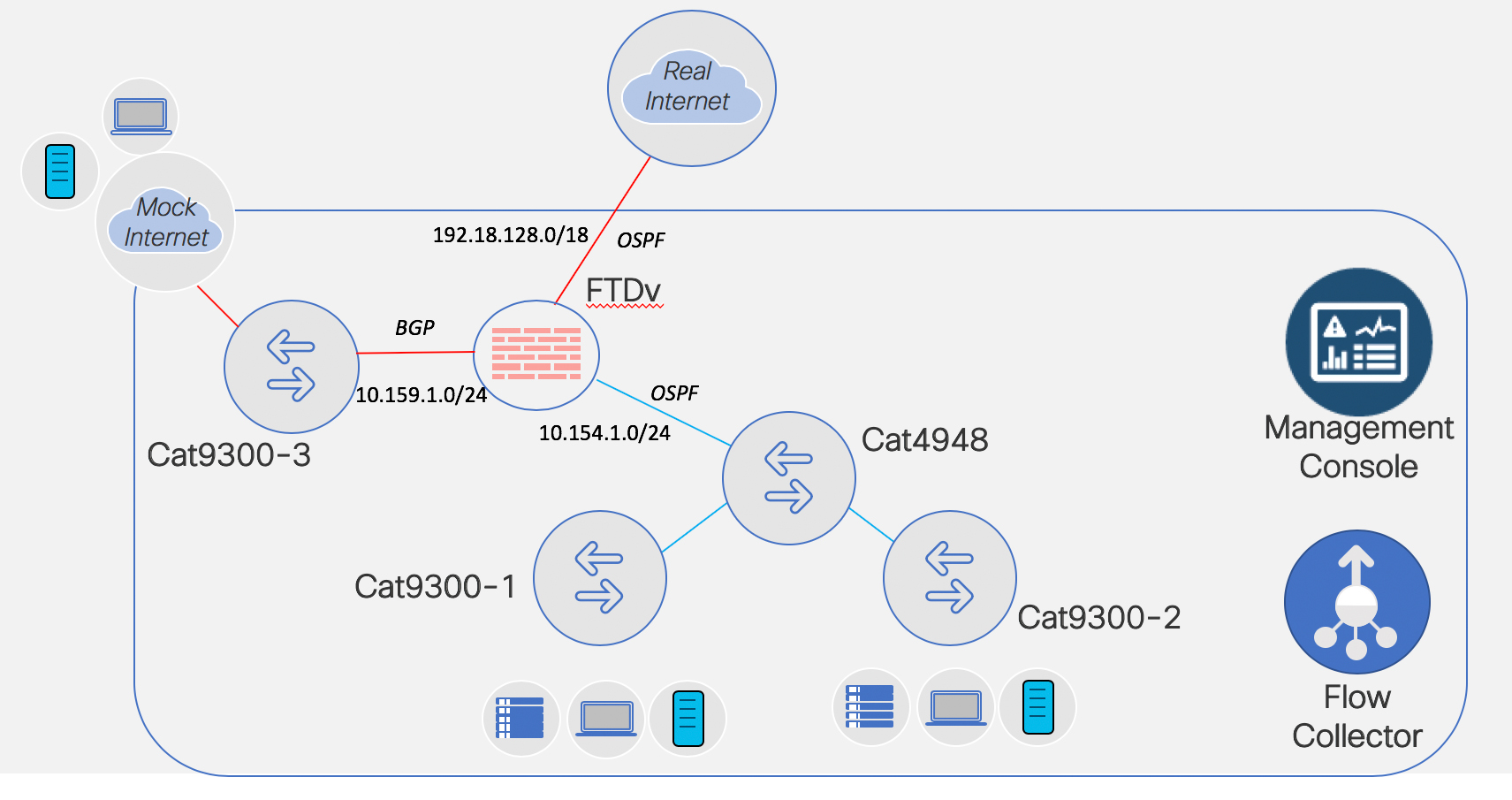
In my previous blog (Fun in the Lab: FTDv & FMC – Install and Deploy) we deployed a FMC VM and a FTDv VM and ended the blog with the FTDv successfully added to the FMC.
Now? Now let’s add IP addressing for the FTDv and also set up routing protocol neighbor relationships. I learned what I am about to show you from my co-worker and friend, Keith Brister. So don’t thank me, thank Keith. 
I tossed together a ~29 minute YouTube. Obviously you can watch the entire thing. Or… here you go for the big sections.
- Overview – Start to 2:17 minutes
- Physical/Logical Mapping Overview – 2:18 to 9:25
- vSwitches, vmNICs and More in VMware – 9:26 to 16:20
- FTDv Configuring IP Adresses via FMC – 16:21 to 23:18
- FTDv Configuring IP Routing via FMC – 23:19 to 29:29
Done and Done. Easy Peasy!
IETF 103, Day 4: Trusted Systems, IoT & IPv6

This week is IETF 103 in Bangkok, Thailand, and we’re bringing you daily blog posts highlighting the topics of interest to us in the ISOC Internet Technology Team. Thursday actually represents the last day of the meeting this time, although there’s still several sessions to draw attention to.
SUIT is meeting first thing at 09.00 UTC+9. This is considering how the firmware of IoT devices can securely updated, and the architecture and information models for this will be discussed. There are three other drafts relating to manifest formats that are the meta-data describing the firmware images.
NOTE: If you are unable to attend IETF 103 in person, there are multiple ways to participate remotely.
DMM is the first of the afternoon sessions at 13.50 UTC+7, and there are several IPv6-related drafts under consideration. Proxy Mobile IPv6 extensions for Distributed Mobility Management proposes a solution whereby mobility sessions are anchored at the last IP hop router, whilst Segment Routing IPv6 for Mobile User Plane defines segment routing behaviour and applicability to the mobile user plane behaviour and defines the functions for that. There’s also three updated drafts on 5G implementations which may interest some.
To round off the week, there’s a choice Continue reading
Competition Finally Comes To Datacenter GPU Compute
AMD’s “Rome” processors, the second generation of Epyc processors that the company will be putting into the field, are a key step for the company on its path back to the datacenter. …
Competition Finally Comes To Datacenter GPU Compute was written by Timothy Prickett Morgan at .
STFC Data Centre Tour 2018 – 45PB of Distributed IP Storage, 3 Tier CLOS network at 100G/200G/400G

Video tour of data centre with 45PB of distributed IP storage and its network
The post STFC Data Centre Tour 2018 – 45PB of Distributed IP Storage, 3 Tier CLOS network at 100G/200G/400G appeared first on EtherealMind.
Citrix, Teridion Combine SD-WAN With a Routing Optimization Network
 Teridion says its technology optimizes the middle mile of connectivity between public cloud providers and ISPs, but where enterprises have no control. And Citrix brings SD-WAN to the first and last mile of enterprises.
Teridion says its technology optimizes the middle mile of connectivity between public cloud providers and ISPs, but where enterprises have no control. And Citrix brings SD-WAN to the first and last mile of enterprises.
ARM is the NNSA’s New Secret Weapon
It might have been difficult to see this happening a mere few years ago, but the National Nuclear Security Administration and one of its key supercomputing sites are looking past Intel to Arm-based supercomputers in hopes of reaching efficiency and memory bandwidth targets needed for nuclear stockpile simulations. …
ARM is the NNSA’s New Secret Weapon was written by Nicole Hemsoth at .
Research Brief: Evolution of Security in Mobile Networks – Impact of 5G
 This new Research Brief from AvidThink delves into the evolution of the mobile network and explores new threats.
This new Research Brief from AvidThink delves into the evolution of the mobile network and explores new threats.
Related Stories
Headcount: The Latest in Firings, Hirings, and Retirings — November 7, 2018
 CenturyLink adds another Level 3 employee to C-Suite; Intel reorganizes its chip manufacturing business; and Docker expands its leadership team.
CenturyLink adds another Level 3 employee to C-Suite; Intel reorganizes its chip manufacturing business; and Docker expands its leadership team.
Nokia Strikes Infosys Deal That Targets Enterprise Digitization
 The vendor recently announced plans to slash thousands of jobs as part of a major corporate restructuring.
The vendor recently announced plans to slash thousands of jobs as part of a major corporate restructuring.
Cisco Axes Hundreds of Jobs
 This round of layoffs follows several recent departures from Cisco’s senior executive team.
This round of layoffs follows several recent departures from Cisco’s senior executive team.
Fighting the Ecosystem Wars in the Proactive Cloud
This article is a chapter from my book Explain the Cloud Like I'm 10. It has 30 reviews on Amazon! If you like this chapter then you'll love the book.

The cloud is always busy proactively working for you in the background. That’s how cloud services compete with each other to keep you in their ecosystem.
Most of the cloud services we’ve talked about so far have been request driven. You initiate a request and the cloud does something for you. You read a book. You search for the nearest coffee shop. You navigate to a destination. You send a message. You play a movie.
Handling direct requests is not all a cloud is good for. In fact, the biggest potential of the cloud is how it can proactively perform jobs for you in the background, without you asking or even knowing that it can be done.
Let’s set this up:
Packet Pockets Edge Data Center Deal With SBA
 Packet is working with other tower owners besides SBA on similar projects. The company plans to install around 50 new sites.
Packet is working with other tower owners besides SBA on similar projects. The company plans to install around 50 new sites.
History Of Networking – Bob Hinden – IPv6
Outro Music:
Danger Storm Kevin MacLeod (incompetech.com)
Licensed under Creative Commons: By Attribution 3.0 License
http://creativecommons.org/licenses/by/3.0/
The post History Of Networking – Bob Hinden – IPv6 appeared first on Network Collective.