Details Emerge On Post-K Exascale System With First Prototype
Japanese computer maker Fujitsu, which has four different processors under development at the same time aimed at different workloads in the datacenter – five if you count its digital annealer quantum chip – has unveiled some of the details about the future Arm processor, as yet unnamed, that is being created for the Post-K exascale supercomputer at RIKEN, the research and development arm of the Japanese Ministry of Education, Culture, Sports, Science and Technology (MEXT). …
Details Emerge On Post-K Exascale System With First Prototype was written by Timothy Prickett Morgan at .
 To win more cloud provider customers Cisco is focusing on helping hyperscalers solve big engineering problems, and it's embracing open networking.
To win more cloud provider customers Cisco is focusing on helping hyperscalers solve big engineering problems, and it's embracing open networking. The carrier had been rumored to be looking to offload the data center assets, which followed similar sales by telecom rivals Verizon and CenturyLink.
The carrier had been rumored to be looking to offload the data center assets, which followed similar sales by telecom rivals Verizon and CenturyLink. The lawmakers claim Google is “more willing to support the Chinese Communist Party than the U.S. military.”
The lawmakers claim Google is “more willing to support the Chinese Communist Party than the U.S. military.”
 Images courtesty of
Images courtesty of 
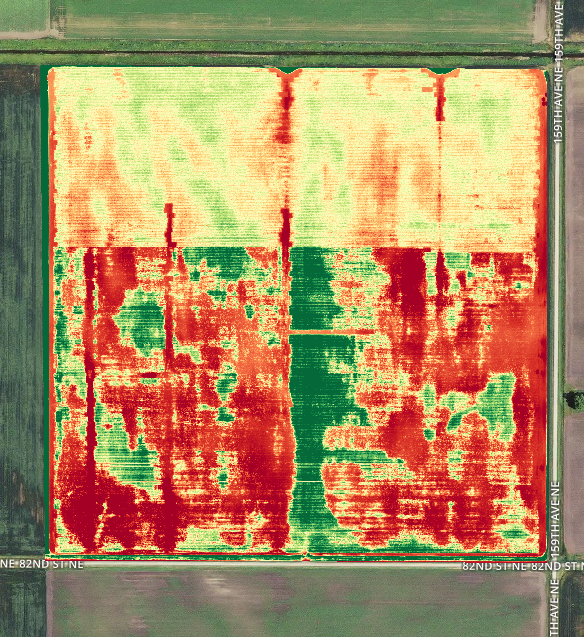
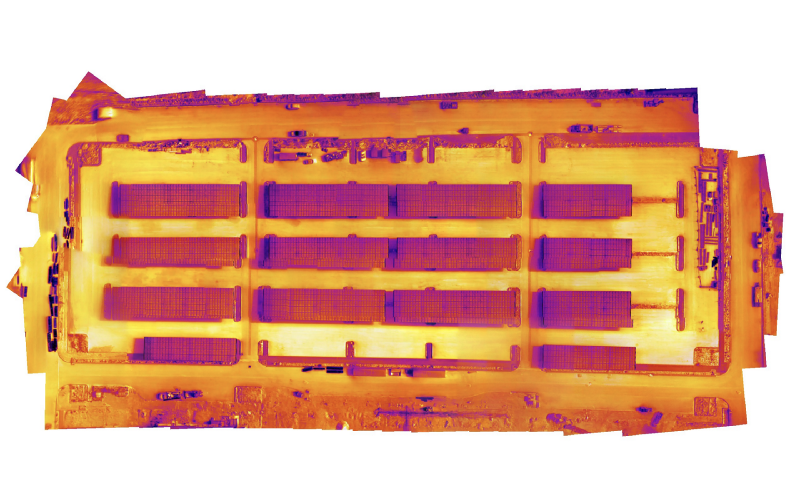 With Thermal Live Map, it’s possible
With Thermal Live Map, it’s possible  The Silver Peak security alliance ecosystem enables customer to choose from eight different security offerings.
The Silver Peak security alliance ecosystem enables customer to choose from eight different security offerings. The company's board of directors named CFO Robert Swan as interim CEO while it searches for a successor.
The company's board of directors named CFO Robert Swan as interim CEO while it searches for a successor.