Extending the Power of NSX to Bare-metal Workloads
Authors – Sridhar Subramanian and Geoff Wilmington
VMware NSX Data Center was built with the goal of consistent networking and security services independent of changing application frameworks or physical infrastructure. In the last couple of years, NSX Data Center has focused on delivering network and security abstractions for applications on any compute platform. In our journey, we have handled VM’s, containers, cloud, and now we are also looking to help our customers with scenarios where they need a unified experience for bare-metal workloads. The goal being to maintain a consistent security experience regardless of location or platform the workload is running on.
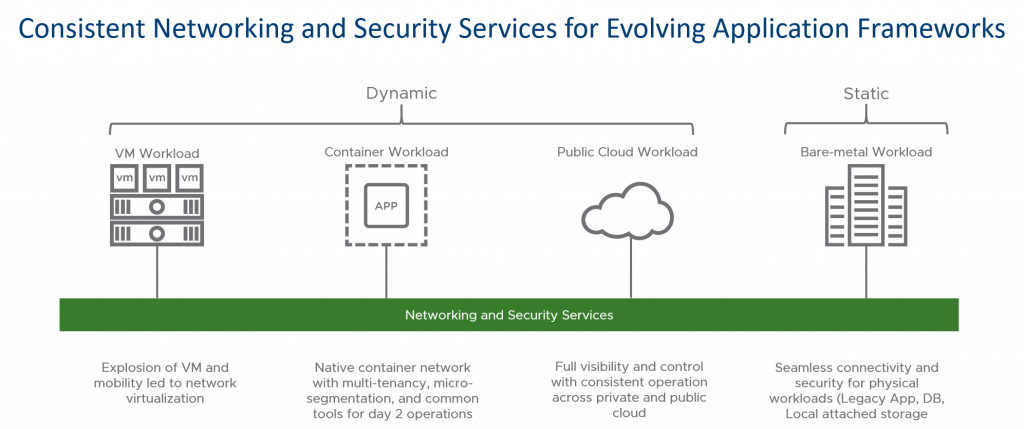
This experience means being able to take any workload, add it to an NSX Data Center Security Group and through the NSX Data Center Distributed Firewall have a consistent policy applied regardless of location and workload type. This consistent approach leverages the NSX DFW capabilities with stateful firewalling for the workloads. This is accomplished outside of using native OS capabilities like IP Tables or Windows Firewall so security admins only need to understand how to apply security through NSX DFW, and not have to understand the myriad of native OS approaches and complexity. By centralizing Continue reading
 We would like to thank Core BTS for sponsoring this episode of Network Collective. Core BTS focuses on partnering with your company to deliver technical solutions that enhance and drive your business. If you’re looking for a partner to help your technology teams take the next step, you can reach out to Core BTS by
We would like to thank Core BTS for sponsoring this episode of Network Collective. Core BTS focuses on partnering with your company to deliver technical solutions that enhance and drive your business. If you’re looking for a partner to help your technology teams take the next step, you can reach out to Core BTS by 



 The 25G Ethernet network infrastructure integrates with cloud and hyperconverged infrastructure software stacks from vendors including VMware, Nutanix, Red Hat, and Microsoft.
The 25G Ethernet network infrastructure integrates with cloud and hyperconverged infrastructure software stacks from vendors including VMware, Nutanix, Red Hat, and Microsoft.
 Unless the TM Forum spends more time on the cultural challenges, most operators will continue to struggle to make meaningful strides toward the holy grail of becoming bona fide Digital Service Providers.
Unless the TM Forum spends more time on the cultural challenges, most operators will continue to struggle to make meaningful strides toward the holy grail of becoming bona fide Digital Service Providers.