WISP Design – Building Highly Available VPLS for Public Subnets
What is VPLS?
Virtual Private LAN Service or VPLS is a Layer 2 overlay or tunnel that allows for the encapsulation of ethernet frames (with or without VLAN tags) over an MPLS network.
https://tools.ietf.org/html/rfc4762
VPLS is often found in Telco networks that rely on PPPoE to create centralized BRAS deployments by bringing all of the end users to a common point via L2.
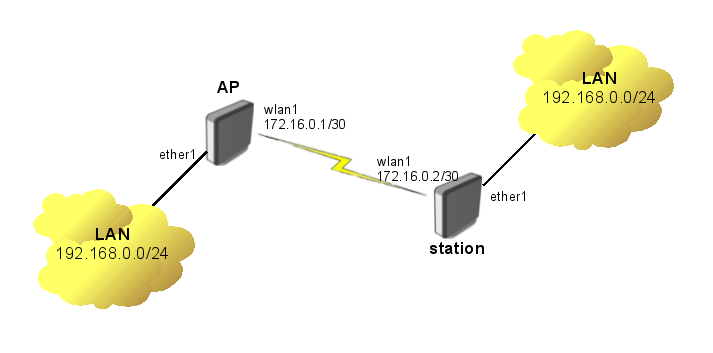
MikroTik VPLS example (https://wiki.mikrotik.com/wiki/Transparently_Bridge_two_Networks_using_MPLS)
Background
The idea for this post came out of a working session (at the bar of course) at WISPAmerica 2018 in Birmingham, Alabama.
There was a discussion about how to create redundancy for VPLS tunnels on multiple routers. I started working on this in EVE-NG as we were talking about it.
The goal is creating highly available endpoints for VPLS when using them to deploy a public subnet that can be delivered to any tower in the WISP. The same idea works for wireline networks as well.
Use Case
As IPv4 becomes harder to get, ISPs like WISPs, without large blocks of public space find it difficult to deploy them in smaller subnets. The idea behind breaking up a /23 or /24 for example, is that every Continue reading


 CEO Borje Ekholm’s cost-cutting measures seem to be working. In the first quarter, the company reined in its losses and improved its gross margin.
CEO Borje Ekholm’s cost-cutting measures seem to be working. In the first quarter, the company reined in its losses and improved its gross margin. Micro-segmentation Starter Kit Traditional security solutions are designed to protect the perimeter. As applications and data are becoming increasingly distributed, they are often spanning not only multiple sites, but also multiple clouds. This is making it harder to identify where the perimeter actually is in order to secure it. But even if the perimeter can...
Micro-segmentation Starter Kit Traditional security solutions are designed to protect the perimeter. As applications and data are becoming increasingly distributed, they are often spanning not only multiple sites, but also multiple clouds. This is making it harder to identify where the perimeter actually is in order to secure it. But even if the perimeter can... 