Episode 22 – Securing BGP
In part 3 of our deep dive into BGP operations, Nick Russo and Russ White join us again on Network Collective to talk about securing BGP. In this episode we cover topics like authentication, advertisement filtering, best practices, origin security, path security, and remotely triggered black holes.
 We would like to thank Cumulus Networks for sponsoring this episode of Network Collective. Cumulus is offering you, our listeners, a completely free O’Reilly ebook on the topic of BGP in the data center. You can get your copy of this excellent technical resource here: http://cumulusnetworks.com/networkcollectivebgp
We would like to thank Cumulus Networks for sponsoring this episode of Network Collective. Cumulus is offering you, our listeners, a completely free O’Reilly ebook on the topic of BGP in the data center. You can get your copy of this excellent technical resource here: http://cumulusnetworks.com/networkcollectivebgp
Show Notes:
- Authentication
- Classic MD5
- Enhanced Authentication extensions (EA). Supported by IOS XR and allows for SHA1 as well, along with key-chain rotations. Doesn’t appear commonly used
- GTSM, and how it can be better than the previous option in some cases
- Basic prefix filtering:
- From your customers: allow any number of their own AS prepended
- From the Internet: block bogons (RFC1918, class D/E, etc)
- To your peers: only your local space (ie, your customers)
- From your peers: only routes originating from their AS (any # of prepends)
- BCP38
- Techniques for spoofing prevention
- Describe with a simple snail mail analogy
- Usually uRPF strict Continue reading
Ready for Take-Off with Kubernetes, Cloud Foundry, and vSphere
A complex and diverse world
Singapore. Etihad. Wow. I always found it impressive when airlines were able to build a business and a brand without a significant domestic customer base to start off from. They instead focus on the global market, which is much more challenging. There is a competitive landscape of many players. There is the complexity of interconnecting a world of disparate lands and diverse customer cultures and preferences. An impressive feat.
The world of networking is becoming quite similar. From private, hybrid, and public cloud models, to increased use of SaaS, to the way SaaS and other apps are built using microservices architectures and containers, the landscape of islands to connect in an inherently secure and automated fashion is increasingly diverse and complex.
An app built to demonstrate this diversity
If the airline to networking analogy is lost on you, or you think it’s too much of a stretch, let me pull up the second reason I used planes in my symbolism. My brilliant colleague Yves Fauser built an app to demonstrate how NSX is connecting and securing this variety of new app frameworks, and it happens to be a “plane spotter” app. You may have already Continue reading
FIRST/TF-CSIRT: The Changing Face of Cybersecurity
The Internet Society was recently approved as a Liaison Member of TF-CSIRT, the European Forum for Computer Security Incident Response Teams, and therefore took the opportunity to participate in the FIRST/TF-CSIRT Symposium that was held 5-7 February 2018 in Hamburg, Germany.
The Internet Society continues to support organisations and activities concerned with maintaining the safety, stability and security of the Internet, and our colleague Kevin Meynell is already known within the TF-CSIRT community having run the forum between 2008 and 2012 and overseen its transition from a grouping of primarily academic CSIRTs to a wider industry body encompassing more than 160 National, Government, Military and Commercial CSIRTs, as well as those in academia.
TF-CSIRT meets three times per year, but starting in 2008 the first meeting of the year has always been held jointly with FIRST, the global Forum of Incident Response and Security Teams. This provides an opportunity for the European CSIRTs to meet with their counterparts around the world to exchange information, and develop the networks of trust that are critical to effective cooperation in handling cyber incidents when they occur, but also in development of early warning and prevention techniques.
And a number of the presentations had particular Continue reading
The Anatomy of a Cisco Spark Bot
I spent a long time creating my first Spark bot, Zpark. The first commit was in August and the first release was posted in January. So, six months elapsed time. It’s also over-engineered. I mean, all it does is post messages back and forth between a back-end system and some Spark spaces and I ended up with something so complex that I had to draw a damn block diagram in the user guide to give people a fighting chance at comprehending how it works.
Its internals could’ve been much simpler. But that was part of the point of creating the bot: examining the proper architecture for a scalable application, learning about new technologies for building my own API, learning about message brokers, pulling my hair out over git’s eccentricities and ultimately, having enough material to write this blog post.
In this post I’m going to break down the different functional components of Zpark, discuss what each does, and why–or not–that component is necessary. If I can achieve one goal, it will be to retire to a tropical island ASAP. If I can achieve a second goal, it will be to give aspiring bot creaters (like yourself, presumably) a strong Continue reading
Cisco Cybersecurity Report: Bad Guys Winning at Weaponizing Encryption
 More than half of all attacks resulted in financial damages of more than $500,000.
More than half of all attacks resulted in financial damages of more than $500,000.
Taking IT Automation to the Next Level
Process and tool simplification will help IT teams become more integrated into everyday business.
How Useful Is Microsegmentation?
Got an interesting microsegmentation-focused email from one of my readers. He started with:
Since every SDDC vendor is bragging about need for microsegmentation in order to protect East West traffic and how their specific products are better compared to competition, I’d like to ask your opinion on a few quick questions.
First one: does it even make sense?
Read more ...ជំរាបសួរ! – Phnom Penh: Cloudflare’s 122nd Data Center
Cloudflare is excited to turn up our newest data center in Phnom Penh, Cambodia, making over 7 million Internet properties even faster. This is our 122nd data center globally, and our 41st data center in Asia. By the end of 2018, we expect that 95% of the world's population will live in a country with a Cloudflare data center, as we grow our global network to span 200 cities.
Cambodian Internet
Home to over 16 million people, Cambodia has a relatively low base of Internet penetration (~25%) today, but is seeing an increasing number of Internet users coming online. For perspective, Cambodia has approximately the same number of Internet users as Lebanon (where we just turned up our 121st data center!) or Singapore (from where we used to serve a portion of Cambodian visitors).
In the coming weeks, we’ll further optimize our routing for Cloudflare customers and expect to see a growing number of ISPs pick up our customers’ traffic on a low latency path.
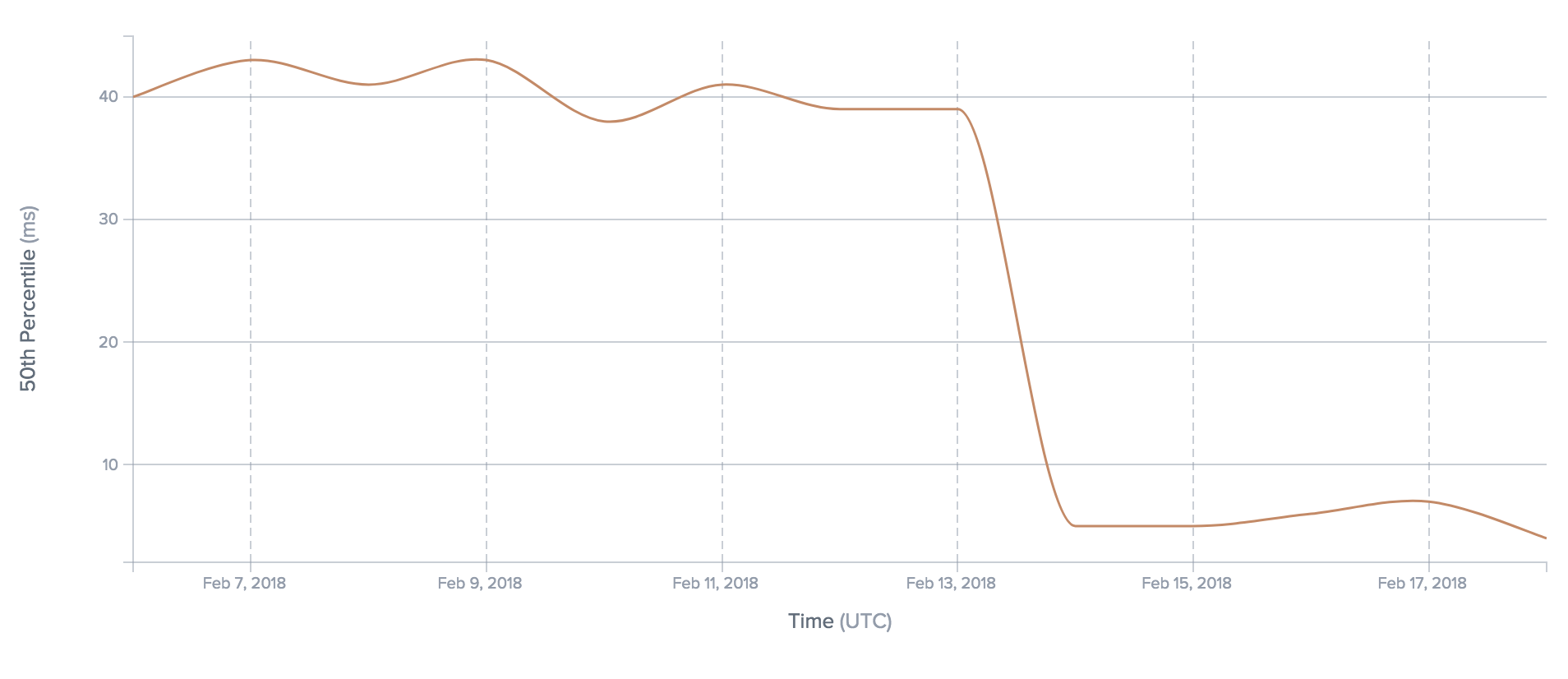
Latency from a Cambodian ISP (SINET) to Cloudflare customers decreases 10x
Coming up next
Next up, in fact, thousands of feet further up, we head to the mountains for Cloudflare’s 123rd data center. Following Continue reading
AT&T Fights Back: 5G Footprint Will be Nationwide, Not Just Hot Spots
 Atlanta, Dallas, and Waco, Texas, will be among the operator’s first 5G markets.
Atlanta, Dallas, and Waco, Texas, will be among the operator’s first 5G markets.
The Anatomy of a Cisco Spark Bot
I spent a long time creating my first Spark bot, Zpark. The first commit was in August and the first release was posted in January. So, six months elapsed time. It's also over-engineered. I mean, all it does is post messages back and forth between a back-end system and some Spark spaces and I ended up with something so complex that I had to draw a damn block diagram in the user guide to give people a fighting chance at comprehending how it works.
Its internals could've been much simpler. But that was part of the point of creating the bot: examining the proper architecture for a scalable application, learning about new technologies for building my own API, learning about message brokers, pulling my hair out over git's eccentricities and ultimately, having enough material to write this blog post.
In this post I'm going to break down the different functional components of Zpark, discuss what each does, and why-or not-that component is necessary. If I can achieve one goal, it will be to retire to a tropical island ASAP. If I can achieve a second goal, it will be to give aspiring bot creaters (like yourself, presumably) a strong Continue reading
NSX-T: Multi-Tiered Routing Architecture
Multi-tenancy exists in some shape or form in almost every network. For an Enterprise network, it can be the separation of tenants based on different business units, departments, different security/network policies or compliance requirements. For a service provider, multi-tenancy can simply be separation of different customers (tenants).
Multi-tenancy doesn’t just allow separation of tenants, but also provides control boundaries as to who controls what. For instance, tenant administrators can control/configure the network and security policies for their specific tenants and a service provider administrator can either provide a shared service or provide inter-tenant or WAN connectivity.
In the logical routing world of NSX-T, this provider function can provide connectivity between the tenant logical networks and physical infrastructure. It can also provide inter-tenant communication or some shared services (like NAT, Load Balancer etc.) to the tenants.
In my previous post, NSX-T: Routing where you need it (Part 1), I discussed how NSX-T provides optimized E-W distributed routing and N-S centralized routing. In addition to that, NSX-T supports a multi-tiered routing model with logical separation between provider router functions and tenant routing functions. The concept of multi-tenancy is built into the routing model. The top-tier logical router is referred to Continue reading
The Linux Foundation Opens to the Edge with Akraino Project
 AT&T contributed seed code to the open source project.
AT&T contributed seed code to the open source project.
VxLan – Short Story Lab
Hi,
Note: Its perfectly possible to do VXLAN/EVPN on VQFX and VMX, all you have to do is to setup a good lab over ESXI or if you want you can do it over Eve-ng emulator. I personally did it via ESXI.
Am not covering the petty BGP configuration of Full-Mesh and Evpn-BGP configuration, its very simple, this post mainly Aims at show-casing the quick and short way of setting up EVPN/VXLAN in Vqfx and over vMX
On the way to some DC Lab Practise, I wanted to quickly show you guys how to lab up Vxlan on Vqfx and Vmx.
Intention – I was reading on VxLan and as most of my learning comes around seeing things first and understanding the later, I felt uncomfortable too soon reading at the Documentation, I wanted to learn it by doing.
Here is the topology
Goal – Build Vxlan / Evpn with a very small set-up to under the workings.
First things first
-> In order to build any VxLan, you need to have some underlay and some overlay. Our underlay is BGP (It can be anything you see, as long as it can exchange Loopback Space and establish IP Continue reading
NDSS 2018: Automating the Process of Vulnerability Discovery
NDSS 2018 is in full swing in San Diego this week and a couple of papers that really grabbed my attention were both in the same session on Network Security and Cellular Networks yesterday.
Samuel Jero, a PhD student at Purdue University and past IRTF Applied Networking Research Prize Winner, presented a fascinating paper on “Automated Attack Discovery in TCP Congestion Control Using a Model-guided Approach”. Of the many protocols and algorithms that are in daily use on the Internet, some are more fundamental and important than others and it doesn’t get much more fundamental and important than TCP congestion control.
TCP congestion control is what makes it possible for millions of autonomous devices and networks to seamlessly, and more-or-less fairly, share available bandwidth. Without it the network would literally collapse.
Attacks against congestion control to manipulate senders’ or receivers’ understanding of the state of the network have been known for some time. Jero and his co-authors Endadul Hoque, David Choffnes, Alan Mislove and Cristina Nita-Rotaru developed an approach using model-based testing to address the scalability challenges of previous work to automate the discovery of manipulation attacks against congestion control algorithms.
By building abstract models of several congestion Continue reading
IBM Storage Rides Up Flash And NVM-Express
IBM’s systems hardware business finished 2017 in a stronger position than it has seen in years, due in large part to the continued growth of the company’s stalwart System z mainframes and Power platform. As we at The Next Platform noted, the last three months of last year were also the first full quarter of shipments of IBM’s new System z14 mainframes, while the first nodes of the “Summit” supercomputer at Oak Ridge National Laboratory and the “Sierra” system at Lawrence Livermore National Laboratory began to ship.
Not to be overlooked was the strong performance of the IBM’s storage …
IBM Storage Rides Up Flash And NVM-Express was written by Jeffrey Burt at The Next Platform.
