Sedona Systems’ NetFusion Maps Networks, Then Automates Services
 Poor quality data is a "silent killer" of service automation.
Poor quality data is a "silent killer" of service automation.
 Poor quality data is a "silent killer" of service automation.
Poor quality data is a "silent killer" of service automation.
 Check out the new Palo Alto Networks channel on SDxCentral for the latest in next-gen security for IoT, 5G, Cloud, and NFV.
Check out the new Palo Alto Networks channel on SDxCentral for the latest in next-gen security for IoT, 5G, Cloud, and NFV.
 The research company also defined "IoT platform."
The research company also defined "IoT platform."
 Digital offers the service in 14 metro areas.
Digital offers the service in 14 metro areas.
Network pros need a wide range of skills to manage cloud, network security, and more.
I had a week off, and being a security domain researcher, I started working on automating security rules in network security components. The goal was to read the existing security rules of the IPv4 protocol and deploy parallel security rules for the IPv6 protocol in the same security component for the newly configured protocol in a network. For this purpose, I started to develop an automation service. The service was intended to use the IPv4 address in a DNS query to resolve the corresponding IPv6 address. The next intended step was to add these same rules in the network security component for the newly resolved IPv6 address. This was when I came to know that the existing DNS protocol does not provide IPv4 to IPv6 resolution and vice versa.
While trying to figure out a solution to this problem, the Internet Society Pakistan Islamabad Chapter announced to carry-out a local IETF-Outreach Program managed by Internet Society Asia-Pacific Bureau. As part of the program, a seminar was conducted that introduced the history of IETF and outlined the process of the Internet standards-making process, including how we could get involved in this process. The most appealing part of the programme was the Continue reading
It is not uncommon for countries around the world to interrupt Internet access for political reasons or because of social unrest. We've seen this many times in the past (e.g. Gabon, Syria, Togo).
Today, it appears that Internet access in the Democratic Republic of Congo has been greatly curtailed. The BBC reports that Internet access in the capital, Kinshasa was cut on Saturday and iAfrikan reports that the cut is because of anti-Kabila protests.
Our monitoring of traffic from the Democratic Republic of Congo shows a distinct drop off starting around midnight UTC on January 21, 2018. Traffic is down to about 1/3 of its usual level.
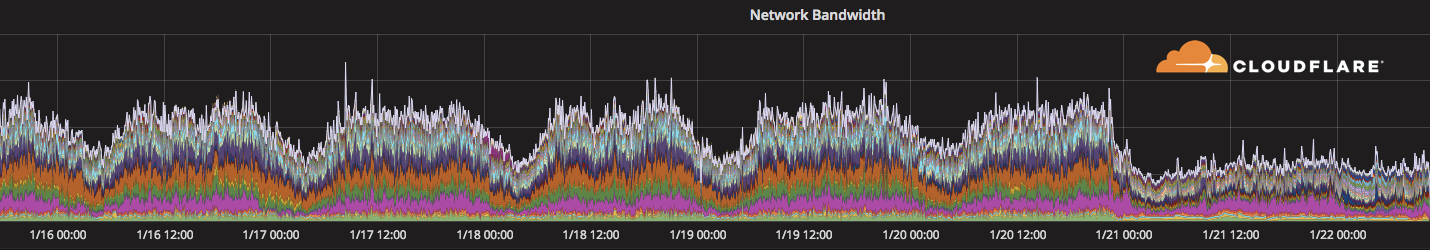
We'll update this blog once we have more information about traffic levels.
CCDE Training in Istanbul on November 2017. It was 5 days , almost 50 hours training. It was very intense and the attendees got tried but enjoyed too, as you will see their feedbacks in the below video. None of these guys attended CCDE Practical exam on November, some of them will attempt on February 2018 …
Continue reading "CCDE Training in Istanbul on November 2017 – Feedbacks"
The post CCDE Training in Istanbul on November 2017 – Feedbacks appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.
CCDE Training in Istanbul on November 2017. It was 5 days , almost 50 hours training. It was very intense and the attendees got tried but enjoyed too, as you will see their feedbacks in the below video. None of these guys attended CCDE Practical exam on November, some of them will attempt on February 2018 …
Continue reading "CCDE Training in Istanbul on November 2017 – Feedbacks"
The post CCDE Training in Istanbul on November 2017 – Feedbacks appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.
CCDE Training in Istanbul on November 2017. It was 5 days , almost 50 hours training. It was very intense and the attendees got tried but enjoyed too, as you will see their feedbacks in the below video. None of these guys attended CCDE Practical exam on November, some of them will attempt on February 2018 […]
The post CCDE Training in Istanbul on November 2017 – Feedbacks appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.
Is BGP RR used in EBGP ? You might think I mean IBGP , not EBGP or I mean BGP Route Server, not BGP Route Reflector but no I really mean BGP RR (Route Reflector). If you are reading this post, for sure you know what is BGP Route Reflector and it is used for …
Continue reading "BGP RR (Route Reflector) in EBGP"
The post BGP RR (Route Reflector) in EBGP appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.
Is BGP RR used in EBGP ? You might think I mean IBGP , not EBGP or I mean BGP Route Server, not BGP Route Reflector but no I really mean BGP RR (Route Reflector). If you are reading this post, for sure you know what is BGP Route Reflector and it is used for …
Continue reading "BGP RR (Route Reflector) in EBGP"
The post BGP RR (Route Reflector) in EBGP appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.
Is BGP RR used in EBGP ? You might think I mean IBGP , not EBGP or I mean BGP Route Server, not BGP Route Reflector but no I really mean BGP RR (Route Reflector). If you are reading this post, for sure you know what is BGP Route Reflector and it is used for […]
The post BGP RR (Route Reflector) in EBGP appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.
While I have stock homework assignments prepared for every module of the Building Network Automation Solutions online course I always encourage the students to pick a challenge from their production network and solve it during the course.
Pavel Rovnov decided to focus on consistency of network management parameters (NTP, SNMP, SSH and syslog configuration) across Extreme and Cumulus switches, Fortinet firewalls and several distributions of Linux.
Read more ...If Mellanox Technologies had not begun investing in the Ethernet switching as it came out of the Great Recession, it would be a much different company than it is today. It might have even been long since acquired by Oracle or some other company, for instance.
To be sure, Mellanox might have been able to capture some business at the cloud builders, hyperscalers, and clustered storage makers with InfiniBand. But it would not have been the one to capitalize on moving InfiniBand-style technologies such as remote direct memory access (RDMA) to Ethernet, and it would not have been able to …
Mellanox Trims Down To Reach For A Profitable $1 Billion was written by Timothy Prickett Morgan at The Next Platform.
Many of my students have been asking whether CCDE Practical/Lab Exam Result policy is still the same. As you might know after CCDE 2017 May exam cancellation , practical exam results can be learned after 8 to 12 weeks. This mean, if you attend CCDE Practical exam, you cannot learn the result (Pass or fail) …
Continue reading "CCDE Practical/Lab Exam Result Policy"
The post CCDE Practical/Lab Exam Result Policy appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.