0
Microsoft, Daimler to use fuel cells to power data centers
In separate announcements, Microsoft Corp. and Daimler indicated that hydrogen fuel cells could provide significantly better energy solutions for data centers than existing electrical grid and backup power technology.Daimler, best known for its Mercedes-Benz automobile brand, presented this week its latest-generation fuel cell technology, which is 30 percent smaller, has 40 percent more power and is small enough to fit into the engine compartment of Mercedes-Benz passenger vehicles. The company plans to expand the use of that technology in a hydrogen-powered data center power plant, collaborating with HPE, Power Innovations (PI) and the National Renewable Energy Laboratory (NREL).To read this article in full, please click here
 Revenue from the company's core business of routers and switches declined 4 percent.
Revenue from the company's core business of routers and switches declined 4 percent. But for the past couple months I’ve been able to really start digging in.
But for the past couple months I’ve been able to really start digging in.
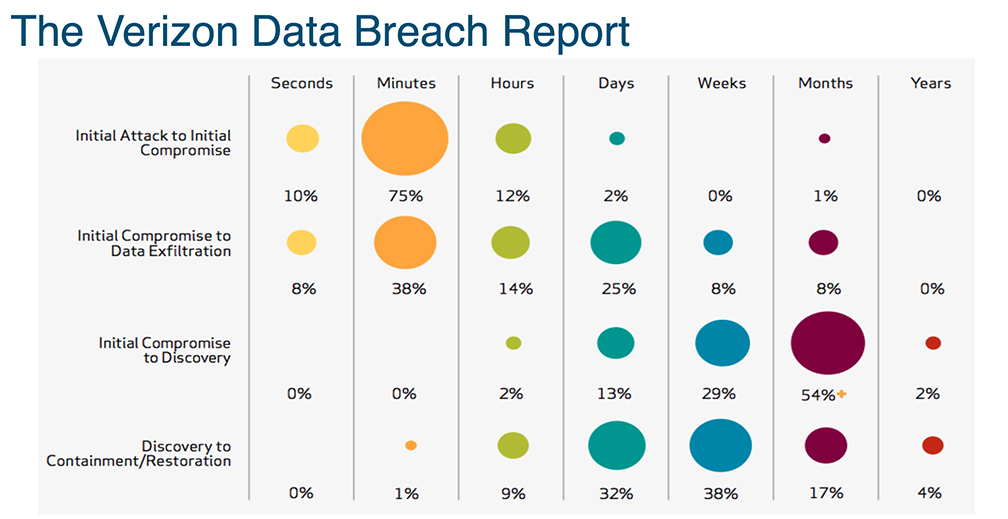
 But for the past couple months I’ve been able to really start digging in.
But for the past couple months I’ve been able to really start digging in. The company has spent at least $6.6B on software-centric companies.
The company has spent at least $6.6B on software-centric companies. Both operators and the LSO APIs rely on ONAP.
Both operators and the LSO APIs rely on ONAP. The SD-WAN market is forecast to reach $3.3 billion in revenue by 2021.
The SD-WAN market is forecast to reach $3.3 billion in revenue by 2021.
 Download now to learn the latest on open source in networking.
Download now to learn the latest on open source in networking.