0
History of computers, part 2 — TCP/IP owes a lot to Xerox PUP
To understand where we are going, we first must understand where we have been. This applies equally well to the history of nations across the globe as it does to computers and computer networking.With that in mind, we’re taking a slow (somewhat meandering) stroll through the history of how computers talk to each other. Last time, we talked a bit about dial-up Bulletin Board Systems (BBSs) – popular through the 1980s and the bulk of the 1990s.Also on Network World: The hidden cause of slow Internet and how to fix it Today, I’d like to talk about one of the most influential, but rarely discussed, networking protocol suites: PARC Universal Packet (PUP).To read this article in full or to leave a comment, please click here


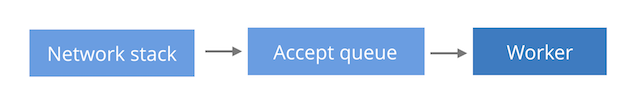
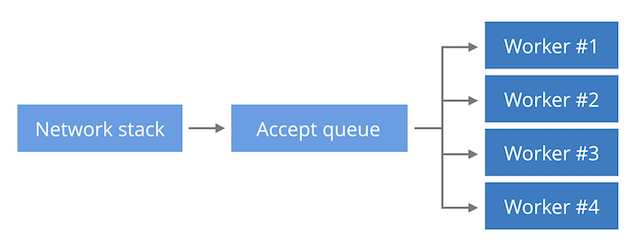
 At the outset, a 1200 word article about saving configuration sounds strange. It would perhaps be perfectly normal if the topic was Vi and not
At the outset, a 1200 word article about saving configuration sounds strange. It would perhaps be perfectly normal if the topic was Vi and not