Worth Reading: Is cloud moving too fast for security?
The post Worth Reading: Is cloud moving too fast for security? appeared first on rule 11 reader.
The post Worth Reading: Is cloud moving too fast for security? appeared first on rule 11 reader.
Change in the work place can be hard, unsettling, uncomfortable and… oh screw it… let’s just say it…. Change in the work place can just be down right scary when we are in the midst of it.
I’m 52 so I’ve been through a lot of changes in my work environment over the years. Since I’m a control freak it likely isn’t much of a shock that work changes like taking on a new job in a new company or new department aren’t the ones that I have the hardest time with. I can see that this is because I feel like I’m the one who initiated the change in those situations. I made the decision to move to that new company, job, or department. I interviewed for it. I felt it “called to me”.
But change in the work place is change in the work place. Whether it is me initiating the change… or the change being “done to me”. So why does a large re-organization in the same company feel scarier to me than me going to a new job at a new company? They are both change. Continue reading
The 5th Africa Domain Names System (DNS) Forum was successfully closed on 28 July after three days of insightful reflections on the Africa DNS Industry and the business opportunities it can provide. This forum follows on the success of previous fora that have taken place in Africa over the past few years – namely South Africa in 2013, Nigeria in 2014, Kenya in 2015, and Morocco in 2016.
 The hybrid cloud sits at the core of compute and storage efforts.
The hybrid cloud sits at the core of compute and storage efforts.
 Founded by Kunihiro Ishiguro and Yoshinari Yoshikawa the founders of GNU Zebra, came together to form IP Infusion back in 1999 as a commercial-grade, hardware-independent networking software company. If you’re not familiar with Zebra, you probably know it’s little brother Quagga which powers everything from Cumulus Linux to Vyatta and even my old digs.. Imagestream routers. Ishiguro and Yoshikawa took Zebra, and built ZebOS, which has been working behind the scenes in products we all use every day for years. IP Infusion’s ZebOS powers everything from F5 LTM’s and Citrix Netscaler’s to Plexxi, SK Telecom, and Huawei networking products.
Founded by Kunihiro Ishiguro and Yoshinari Yoshikawa the founders of GNU Zebra, came together to form IP Infusion back in 1999 as a commercial-grade, hardware-independent networking software company. If you’re not familiar with Zebra, you probably know it’s little brother Quagga which powers everything from Cumulus Linux to Vyatta and even my old digs.. Imagestream routers. Ishiguro and Yoshikawa took Zebra, and built ZebOS, which has been working behind the scenes in products we all use every day for years. IP Infusion’s ZebOS powers everything from F5 LTM’s and Citrix Netscaler’s to Plexxi, SK Telecom, and Huawei networking products.
Today IP Infusion is selling two variants of ZebOS to OEMs, OcNOS and VirNOS. OcNOS is a full featured network OS built specifically for White Box OEMs looking for switching, routing, MPLS, and SDN support. It can support a hybrid, centralized, or distributed network framework which provides a scalable, modular, and robust framework that can be deployed on merchant silicon. VirNOS is their NFV solution that can be used for distributed or cloud based vCPE, vPE, or vRouters in your data center.
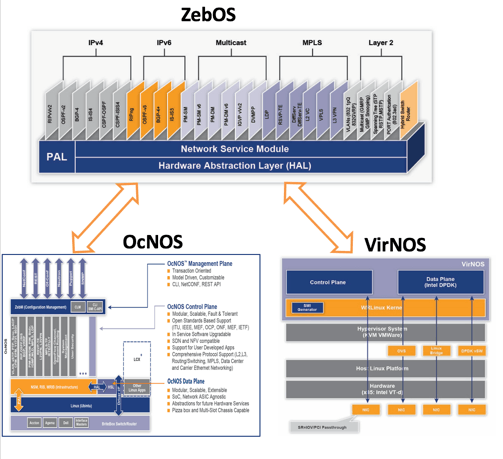
Whitebox networking is a really exciting market that I have been looking into since the SDN craze started. Continue reading
In this post, I’m going to explain how we can use an SDN controller to provision traffic-engineered MPLS LSPs between PE nodes situated in different traffic-engineering domains.
The SDN controller that we’re going to use is NorthStar from Juniper Networks running version 3.0. For more information regarding NorthStar check here. There is also a great Day One book available: NorthStar Controller Up and Running.
Typically, in order to provision traffic-engineered MPLS LSPs between PE nodes, it is necessary for the PEs to be situated in a common TE domain. There are some exceptions to this such as inter-domain LSP or LSP stitching. However, these options are limited and do not support end-to-end traffic-engineering as the ingress PE does not have a complete traffic-engineering view. I personally haven’t seen many deployments utilising these features.
So, what’s the use case? Many service providers and network operators are using RSVP to signal traffic-engineered LSPs in order to control how traffic flows through their environments. There are many reasons for doing this, such as steering certain types of traffic via optimal paths or achieving better utilisation of network bandwidth. With many RSVP deployments, you will see RSVP used in the core of Continue reading
What is Layer 0 in the OSI layers ? Isn’t OSI (Open Systems Interconnection) seven layers? Yes it is. In the standard, seven layers have been defined. Just let’s remember the seven layers of OSI. Layer 7: The application layer. Layer 6: The presentation layer. Layer 5: The session layer. Layer 4: The […]
The post What is Layer 0 in the OSI Layers ? appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.
5/5 - (1 vote)
The post The Number of the Beast or the Practical usage of the Blackhole Community appeared first on Noction.
Is it really hard to spell ‘ Orhan Ergun ‘ ? I see a lot of different variations of my name, its funny though ? Below are some search keywords which people used to find something related with me. I know my name is not very common. In fact, among English speaking people, one […]
The post Is it really hard to spell ‘ Orhan Ergun ‘ ? appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.
Nonprofit takes innovative, cost-effective approach to handle higher densities in older facilities.
People have always been quick to blame the network.
You wouldn’t believe it – after almost 22 years (yeah, it’s been that long since RFC 1883 was published), IPv6 became an Internet standard (RFC8200/STD86). No wonder some people claim IETF moves at glacial speed ;)
Speaking of IPv6, IETF and glacial speeds – there’s been a hilarious thread before Prague IETF meeting heatedly arguing whether the default WLAN SSID should be IPv6-only (+NAT64). Definitely worth reading (for the entertainment value) over a beer or two.