Data Center Physical Realities in a Software-Defined World
A company's ability to leverage software depends on efficient infrastructure.
Docker Networking Basics: A Quick Guide
Learn about default Docker network settings and options for expanded networking capabilities.
DMVPN Configurations on Juniper Router
Below are some of the links where i started with the DMVPN explanations
DMVPN Basics
DMVPN Vs IPSEC Basics
Quick Comparison: IPSEC vs DMVPN vs EasyVPN vs GETVPN
The configurations used here are for the demo purposes and has no relevance with any of the live and the enterprise networks. What kind of Topology it looks like, So i am pasting here the sample DMVPN topology and has no relevance with the configuration defining below. The configuration is just for your reference to take it further.
 |
| Fig 1.1- Sample DMVPN Topology |
ISIS Authentication types (packet captures)
In this post i would like to highlight a couple of “features” of ISIS.
More specifically the authentication mechanism used and how it looks in the data plane.
I will do this by configuring a couple of routers and configure the 2 authentication types available. I will then look at packet captures taken from the link between them and illustrate how its used by the ISIS process.
The 2 types of Authentication are link-level authentication of the Hello messages used to establish an adjacency and the second type is the authentication used to authenticate the LSP’s (Link State Packet) themselves.
First off, here is the extremely simple topology, but its all thats required for this purpose:
Simple, right? 2 routers with 1 link between them on Gig1. They are both running ISIS level-2-only mode, which means they will only try and establish a L2 adjacency with their neighbors. Each router has a loopback interface, which is also advertised into ISIS.
First off, lets look at the relevant configuration of CSR-02 for the Link-level authentication:
key chain MY-CHAIN key 1 key-string WIPPIE ! interface GigabitEthernet1 ip address 10.1.2.2 255.255.255.0 ip router isis 1 negotiation auto no Continue reading
Notes from IETF 99 – The IEPG Meeting
Interest in the DNS appears to come in pronounced surges. Its quiet for a few years, then there is a furious burst of activity. If the activity at the recent IETF meeting is any indication, we appear to be in the middle of a burst of activity.Defending anti-netneutrality arguments
Last week, activists proclaimed a "NetNeutrality Day", trying to convince the FCC to regulate NetNeutrality. As a libertarian, I tweeted many reasons why NetNeutrality is stupid. NetNeutrality is exactly the sort of government regulation Libertarians hate most. Somebody tweeted the following challenge, which I thought I'd address here.@ErrataRob I'd like to see you defend your NN stance in this context.https://t.co/2yvwMLo1m1https://t.co/a7CYxd9vcW— Tanner Bennett (@NSExceptional) July 21, 2017
The links point to two separate cases.
- the Comcast BitTorrent throttling case
- a lawsuit against Time Warning for poor service
- the Comcast BitTorrent throttling benefits customers
- poor service has nothing to do with NetNeutrality
The long answers are below.
EVPN-VXLAN INTER-TENANT ROUTING ON JUNIPER QFX / MX
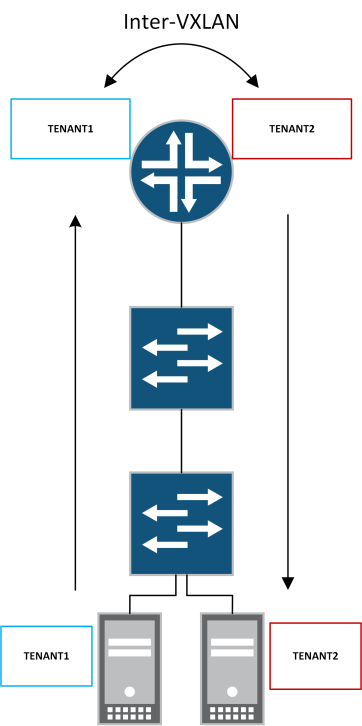
I’ve recently started working on a project focused on EVPN-VXLAN based on Juniper technology. I figured I’d take the opportunity to share some experiences specifically around inter-VXLAN routing. Inter-VXLAN routing can be useful when passing traffic between different tenants. For example, you may have a shared-services tenant that needs to be accessed by a number of different customer tenants whilst not allowing reachability between customer tenants. By enabling inter-VXLAN routing on the MX we can use various route-leaking techniques and policy to provide a technical point of control.
To read the article then please head over to the iNET ZERO blog
IP over AX.25 over 802.11 with ESP8266
IP over AX.25 over 802.11 with ESP8266
I love obscure protocols, and while most of the world’s legacy X.25 equipment is slowly being shut down. It’s amateur radio derivative AX.25 is getting along pretty wel
Notes from IETF 99 – The IEPG Meeting
Many years ago the IEPG had a role in allowing network operators to talk to other operators about what they were seeing and what they were thinking about. Those days are long since over, and today the IEPG meetings present an opportunity for an eclectic set of diehards to listen to an equally eclectic collection of presentations that wander over much of the topics of today's Internet, without any particular common theme or filter.2017 Edge Computing and MEC Report Survey is Here!
 Take survey and enter to win one of two $300 Amazon Gift Cards.
Take survey and enter to win one of two $300 Amazon Gift Cards.
JUNIPER NORTHSTAR UPGRADE 2.1 TO 3.0
In this post, I’m quickly going to describe how to upgrade NorthStar 2.1 to 3.0. For a detailed installation and user guide refer to the 3.0 release notes here.
Firstly, let’s start off by verifying the current host OS and NorthStar versions. Note. NorthStar 3.0 requires a minimum of Centos 6.7 or above.
[root@northstar ~]# cat /etc/redhat-release
CentOS release 6.9 (Final)
To check the current version of NorthStar, navigate to the about section via the drop down menu located at the top right of the GUI
Download NorthStar, Extract & Copy:
Download the NorthStar 3.0 application from Juniper.net NorthStar download page. Once downloaded, extract the RPM and copy to your host machine. Below I have copied the NorthStar-Bundle-3.0.0-20170630_141113_70366_586.x86_64.rpm to the /root/rpms/ directory.
[root@northstar ~]# ls /root/rpms/ -l
total 3843976
-rw-r–r–. 1 root root 881371892 Mar 11 2016 NorthStar-Bundle-2.0.0-20160311_005355.x86_64.rpm
-rw-r–r– 1 root root 856402720 Jul 11 2016 NorthStar-Bundle-2.1.0-20160710_201437_67989_360.x86_64.rpm
-rw-r–r– 1 root root 2148942508 Jun 30 19:24 NorthStar-Bundle-3.0.0-20170630_141113_70366_586.x86_64.rpm
-rw-r–r– 1 root root 21878016 Dec 28 2016 NorthStar-Patch-2.1.0-sp1.x86_64.rpm
-rw-r–r–. 1 root root 27610536 Mar 11 Continue reading
Top Players in the Container Ecosystem You Should Know
 Vendors chasing a multibillion dollar market.
Vendors chasing a multibillion dollar market.
Worth Reading: AMD and the Infinity Fabric
The post Worth Reading: AMD and the Infinity Fabric appeared first on rule 11 reader.
What Does Cisco’s Intent-Based Networking Actually Do?
 Cisco stole some marketing thunder from MEF, which is taking over ONF's work on the technology.
Cisco stole some marketing thunder from MEF, which is taking over ONF's work on the technology.