NB455: Extreme Announces ZTNA Offering; Palo Alto Networks Spends Big On A Browser Startup
Extreme Networks is jumping into Zero Trust Network Access, Palo Alto Networks is reportedly spending more than half a billion dollars to acquire a corporate browser startup, and Forrester predicts as much as 20% of VMware's customers may jump ship after the Broadcom acquisition completes. We cover these stories and more in today's Network Break podcast.
The post NB455: Extreme Announces ZTNA Offering; Palo Alto Networks Spends Big On A Browser Startup appeared first on Packet Pushers.
Top500 Supercomputers: Who Gets The Most Out Of Peak Performance?
The most exciting thing about the Top500 rankings of supercomputers that come out each June and November is not who is on the top of the list. …
The post Top500 Supercomputers: Who Gets The Most Out Of Peak Performance? first appeared on The Next Platform.
Top500 Supercomputers: Who Gets The Most Out Of Peak Performance? was written by Timothy Prickett Morgan at The Next Platform.
Tech Bytes: Why AI Workloads Require Optimized Ethernet Fabrics (Sponsored)
Network engineers have a good grasp on how to build data center networks to support all kinds of apps, from traditional three-tier designs to applications built around containers and microservices. But what about building a network fabric to support AI? Today on the Tech Bytes podcast, sponsored by Nokia, we talk about the special requirements... Read more »Tech Bytes: Why AI Workloads Require Optimized Ethernet Fabrics (Sponsored)
Network engineers have a good grasp on how to build data center networks to support all kinds of apps, from traditional three-tier designs to applications built around containers and microservices. But what about building a network fabric to support AI? Today on the Tech Bytes podcast, sponsored by Nokia, we talk about the special requirements to build a data center fabric for AI use cases such as training and inference.
The post Tech Bytes: Why AI Workloads Require Optimized Ethernet Fabrics (Sponsored) appeared first on Packet Pushers.
Nvidia Pushes Hopper HBM Memory, And That Lifts GPU Performance
For very sound technical and economic reasons, processors of all kinds have been overprovisioned on compute and underprovisioned on memory bandwidth – and sometimes memory capacity depending on the device and depending on the workload – for decades. …
The post Nvidia Pushes Hopper HBM Memory, And That Lifts GPU Performance first appeared on The Next Platform.
Nvidia Pushes Hopper HBM Memory, And That Lifts GPU Performance was written by Timothy Prickett Morgan at The Next Platform.
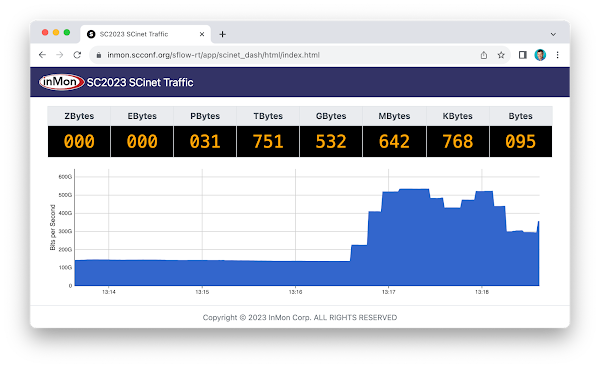
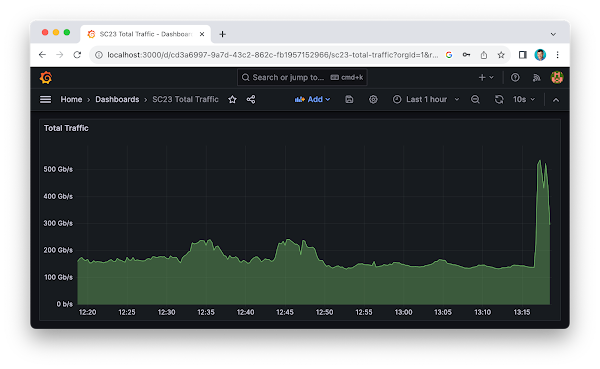
SC23 SCinet traffic
The real-time dashboard shows total network traffic at The International Conference for High Performance Computing, Networking, Storage, and Analysis (SC23) conference being held this week in Denver. The dashboard shows that 31 Petabytes of data have been transferred already and the conference hasn't even started. The conference network used in the demonstration, SCinet, is described as the most powerful and advanced network on Earth, connecting the SC community to the world. In this example, the sFlow-RT real-time analytics engine receives sFlow telemetry from switches, routers, and servers in the SCinet network and creates metrics to drive the real-time charts in the dashboard. Getting Started provides a quick introduction to deploying and using sFlow-RT for real-time network-wide flow analytics. The dashboard above trends SC23 Total Traffic. The dashboard was constructed using the Prometheus time series database to store metrics retrieved from sFlow-RT and Grafana to build the dashboard. Deploy real-time network dashboards using Docker compose demonstrates how to deploy and configure these tools to create custom dashboards like the one shown here.Finally, check out the SC23 Dropped packet visibility demonstration to learn about one of newest developments in sFlow monitoring and see a live demonstration.
How Certified SASE Solutions Build Trust and Resilience
Implementing a certified SASE solution improves interoperability and enables an enterprise to take advantage of the latest SASE features and functionality.LAN Data Link Layer Addressing
Last week, we discussed Fibre Channel addressing. This time, we’ll focus on data link layer technologies used in multi-access networks: Ethernet, Token Ring, FDDI, and other local area- or Wi-Fi technologies.
The first local area networks (LANs) ran on a physical multi-access medium. The first one (original Ethernet) started as a thick coaxial cable1 that you had to drill into to connect a transceiver to the cable core.
Later versions of Ethernet used thinner cables with connectors that you put together to build whole network segments out of pieces of cable. However, even in that case, we were dealing with a single multi-access physical network – disconnecting a cable would bring down the whole network.
LAN Data Link Layer Addressing
Last week, we discussed Fibre Channel addressing. This time, we’ll focus on data link layer technologies used in multi-access networks: Ethernet, Token Ring, FDDI, and other local area- or Wi-Fi technologies.
The first local area networks (LANs) ran on a physical multi-access medium. The first one (original Ethernet) started as a thick coaxial cable1 that you had to drill into to connect a transceiver to the cable core.
Later versions of Ethernet used thinner cables with connectors that you put together to build whole network segments out of pieces of cable. However, even in that case, we were dealing with a single multi-access physical network – disconnecting a cable would bring down the whole network.
Putting TACC’s “Stampede3” Through The HBM Paces
When you host the workhorse supercomputers of the National Science Foundation, you strive to provide the best possible solutions for your scientists. …
The post Putting TACC’s “Stampede3” Through The HBM Paces first appeared on The Next Platform.
Putting TACC’s “Stampede3” Through The HBM Paces was written by Ken Strandberg at The Next Platform.
Cisco Intent-Based Networking: Part I – Introduction
Introduction
This chapter introduces Cisco's approach to Intent-based Networking (IBN) through their Centralized SDN Controller, Cisco DNA Center, rebranded as Cisco Catalyst Center (from now on, I am using the abbreviation C3 for Cisco Catalyst Center). We focus on the network green field installation, showing workflows, configuration parameters, and relationships and dependencies between building blocks. The C3 workflow is divided into four main entities: 1) Design, 2) Policy, 3) Provision, and 4) Assurance, each having its own sub-processes. This chapter introduces the Design phase focusing on Network Hierarchy, Network Settings, and Network Profile with Configuration Templates.
This post deprecates the previous post, "Cisco Intent-Based Networking: Part I, Overview."
Network Hierarchy
Network Hierarchy is a logical structure for organizing network devices. At the root of this hierarchy is the Global Area, where you establish your desired network structure. In our example, the hierarchy consists of four layers: Area (country - Finland), Sub-area (city - Joensuu), Building (JNS01), and Floor (JNS01-FLR01). Areas and Buildings indicate the location, while Floors provide environmental information relevant to wireless networks, such as floor type, measurements, and wall properties.
Network Settings
Network settings define device credentials (CLI, HTTP(S), SNMP, and NETCONF) required for accessing devices Continue reading
Debian on Mellanox SN2700 (32x100G)
Introduction
I’m still hunting for a set of machines with which I can generate 1Tbps and 1Gpps of VPP traffic, and considering a 100G network interface can do at most 148.8Mpps, I will need 7 or 8 of these network cards. Doing a loadtest like this with DACs back-to-back is definitely possible, but it’s a bit more convenient to connect them all to a switch. However, for this to work I would need (at least) fourteen or more HundredGigabitEthernet ports, and these switches tend to get expensive, real quick.
Or do they?
Hardware
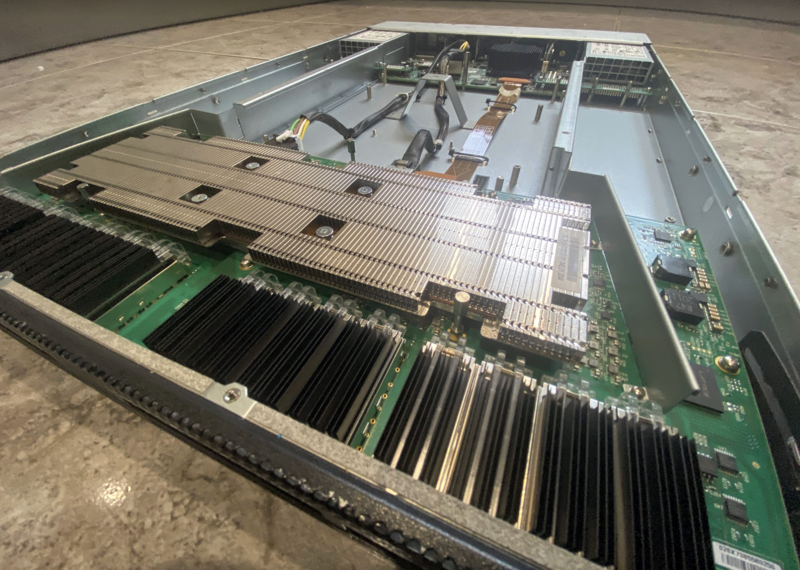
I thought I’d ask the #nlnog IRC channel for advice, and of course the usual suspects came past, such as Juniper, Arista, and Cisco. But somebody mentioned “How about Mellanox, like SN2700?” and I remembered my buddy Eric was a fan of those switches. I looked them up on the refurbished market and I found one for EUR 1’400,- for 32x100G which felt suspiciously low priced… but I thought YOLO and I ordered it. It arrived a few days later via UPS from Denmark to Switzerland.
The switch specs are pretty impressive, with 32x100G QSFP28 ports, which can be broken out to a set of Continue reading
My First Web Page
<h2>My First Web Page</h2>
<p>My first paragraph.</p>
<p>Never call dudud document.write after the document has finished loading.
<div id="om-utia0gbpx93d4wvo9abp-holder"></div>.
It will overwrite the whole document.</p>
<script>
document.write(5 + 6);
</script>The post My First Web Page appeared first on Tigera.