IPv6 Buzz 138: Making Sense Of DHCPv6 Prefix Delegation (DHCPv6-PD)
DHCPv6 Prefix Delegation (DHCPv6-PD) is an IETF RFC that lets a router delegate a long-lived prefix, using DHCP, to a requesting router. The hosts discuss how this is used today both by service providers and in the enterprise, and potential impacts on address allocation and planning.
The post IPv6 Buzz 138: Making Sense Of DHCPv6 Prefix Delegation (DHCPv6-PD) appeared first on Packet Pushers.
Fact-Gathering with Event-Driven Ansible for Microsoft Windows ITSM
The use of Event-Driven Ansible to enable fact gathering from events is considered a “Getting Started” type of use case, but it can be extremely powerful. This use case is simple and it is what we consider a “Read Only” type of action, meaning that we are not making any changes, but we are using the event to trigger a fact gathering process which we can later publish to the IT Service Management system.
The benefit with this is we are able to provide consistent automated troubleshooting and fact gathering which is used to enrich the ticketing systems, so when our engineers have a look at the incident, they have all the information they need to decide on the next steps to resolve the issue or situation. This can potentially save many hours of toil and ultimately save an organization money from reduced down time and faster resolutions. But, we are assuming that our technical teams will know what to do with this event data.
What if we could assist with filling the gap when an incident takes place, and we could receive information or even options on how to resolve the issues? This is where we could use Continue reading
BGP Labs: Build a Transit Network with IBGP
Last time we built a network with two adjacent BGP routers. Now let’s see what happens when we add a core router between them:
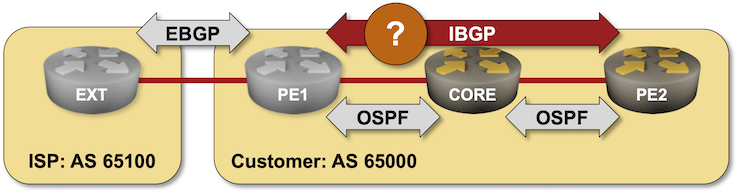
BGP Labs: Build a Transit Network with IBGP
Last time we built a network with two adjacent BGP routers. Now let’s see what happens when we add a core router between them:

Where Cloud And AI Titans Rule The Network
As 2023 has progressed, the revenue growth projections at Arista Networks have inched up as its supply chain issues are getting resolved. …
The post Where Cloud And AI Titans Rule The Network first appeared on The Next Platform.
Where Cloud And AI Titans Rule The Network was written by Timothy Prickett Morgan at The Next Platform.
Cloudflare incident on October 30, 2023

Multiple Cloudflare services were unavailable for 37 minutes on October 30, 2023. This was due to the misconfiguration of a deployment tool used by Workers KV. This was a frustrating incident, made more difficult by Cloudflare’s reliance on our own suite of products. We are deeply sorry for the impact it had on customers. What follows is a discussion of what went wrong, how the incident was resolved, and the work we are undertaking to ensure it does not happen again.
Workers KV is our globally distributed key-value store. It is used by both customers and Cloudflare teams alike to manage configuration data, routing lookups, static asset bundles, authentication tokens, and other data that needs low-latency access.
During this incident, KV returned what it believed was a valid HTTP 401 (Unauthorized) status code instead of the requested key-value pair(s) due to a bug in a new deployment tool used by KV.
These errors manifested differently for each product depending on how KV is used by each service, with their impact detailed below.
What was impacted
A number of Cloudflare services depend on Workers KV for distributing configuration, routing information, static asset serving, and authentication state globally. These services instead received Continue reading
AMD’s Instinct GPU Business Is Coiled To Spring
Timing is a funny thing. The summer of 2006 when AMD bought GPU maker ATI Technologies for $5.6 billion and took on both Intel in CPUs and Nvidia in GPUs was the same summer when researchers first started figuring out how to offload single-precision floating point math operations from CPUs to Nvidia GPUs to try to accelerate HPC simulation and modeling workloads. …
The post AMD’s Instinct GPU Business Is Coiled To Spring first appeared on The Next Platform.
AMD’s Instinct GPU Business Is Coiled To Spring was written by Timothy Prickett Morgan at The Next Platform.
D2C218: What’s Inside The AI Magic Box?
AI and machine learning are being more widely used in IT and elsewhere. Today's episode opens the AI magic box to better understand what's inside, including software and hardware. We discuss essentials such as training models and parameters, software components, GPUs, networking, and storage. We also discuss using cloud-based AI platforms vs. building your own in-house, and what to consider when assembling your own AI infrastructure.D2C218: What’s Inside The AI Magic Box?
AI and machine learning are being more widely used in IT and elsewhere. Today's episode opens the AI magic box to better understand what's inside, including software and hardware. We discuss essentials such as training models and parameters, software components, GPUs, networking, and storage. We also discuss using cloud-based AI platforms vs. building your own in-house, and what to consider when assembling your own AI infrastructure.
The post D2C218: What’s Inside The AI Magic Box? appeared first on Packet Pushers.
Addressing Visibility Blind Spots in Co-los and the Public Cloud
As businesses increasingly migrate mission-critical applications or services to colo facilities and the public cloud, the lack of visibility into their cloud infrastructure must be addressed to avoid blind spots.Worth Reading: Taming the BGP Reconfiguration Transients
Almost exactly a decade ago I wrote about a paper describing how IBGP migrations can cause forwarding loops and how one could reorder BGP reconfiguration steps to avoid them.
One of the paper’s authors was Laurent Vanbever who moved to ETH Zurich in the meantime where his group keeps producing great work, including the Chameleon tool (code on GitHub) that can tame transient loops while reconfiguring BGP. Definitely something worth looking at if you’re running a large BGP network.
Worth Reading: Taming the BGP Reconfiguration Transients
Almost exactly a decade ago I wrote about a paper describing how IBGP migrations can cause forwarding loops and how one could reorder BGP reconfiguration steps to avoid them.
One of the paper’s authors was Laurent Vanbever who moved to ETH Zurich in the meantime where his group keeps producing great work, including the Chameleon tool (code on GitHub) that can tame transient loops while reconfiguring BGP. Definitely something worth looking at if you’re running a large BGP network.
Restoring Hashcat Cracking
Hash cracking is often paused or stopped for various reasons. Hashcat has a Pause button […]
The post Restoring Hashcat Cracking first appeared on Brezular's Blog.
Amazon Gears Up To Profit Mightily From The Generative AI Boom
Because they are in the front of the line for acquiring Nvidia datacenter GPUs, the hyperscalers and cloud builders are going to be the ones who benefit mightily from shortages of matrix math engines that can train AI models and run inference against them. …
The post Amazon Gears Up To Profit Mightily From The Generative AI Boom first appeared on The Next Platform.
Amazon Gears Up To Profit Mightily From The Generative AI Boom was written by Timothy Prickett Morgan at The Next Platform.