Software-Defined Data Center: How to Get Started
Interop ITX speaker says the key to a smooth transition is to start small with fresh hardware.
Interop ITX speaker says the key to a smooth transition is to start small with fresh hardware.
If you can’t beat the largest cloud players at economies of scale, the only option is to try to outrun them in performance, capabilities, or price.
While go head to head with Amazon, Google, Microsoft, or IBM on cloud infrastructure prices is a challenge, one way to gain an edge is by being the first to deliver bleeding-edge hardware to those users with emerging, high-value workloads. The trick is to be at the front of the wave, often with some of the most expensive iron, which is risky with AWS and others nipping at heels and quick to follow. It …
Risk or Reward: First Nvidia DGX-1 Boxes Hit the Cloud was written by Nicole Hemsoth at The Next Platform.
See what users say about popular firewalls from Palo Alto Networks, Cisco, and more.
Cloudflare is now well into its 6th year and providing authoritative DNS has been a core part of infrastructure from the start. We’ve since grown to be the largest and one of the fastest managed DNS services on the Internet, hosting DNS for nearly 100,000 of the Alexa top 1M sites and over 6 million other web properties – or DNS zones.
 CC-BY 2.0 image by Steve Jurvetson
CC-BY 2.0 image by Steve Jurvetson
Today Cloudflare’s DNS service answers around 1 million queries per second – not including attack traffic – via a global anycast network. Naturally as a growing startup, the technology we used to handle tens or hundreds of thousands of zones a few years ago became outdated over time, and couldn't keep up with the millions we have today. Last year we decided to replace two core elements of our DNS infrastructure: the part of our DNS server that answers authoritative queries and the data pipeline which takes changes made by our customers to DNS records and distributes them to our edge machines across the globe.
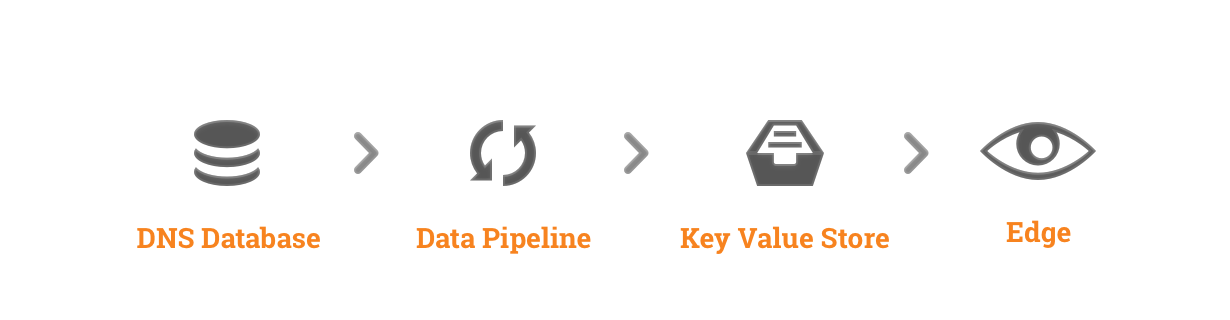
The rough architecture of the system can be seen above. We store customer DNS records and other origin server information in a central database, convert the Continue reading
Evgeny made an interesting observation while testing the NETCONF client on IOS XE 16.x (see also this comment on my blog):
The most interesting part: for unknown reason IOS-XE gives different answers about capabilities on ports 830 and 22.
Einar quickly explained the mysterious behavior:
Read more ...Hell has nine layers .... so does the OSI model. I know, I know, you have been taught that the OSI model has seven layers. See the illustration below for the proof. continue reading
Networking pros are spending more of their time troubleshooting security-related issues, survey finds.
 The Deis platform combines features and technologies from Google, Docker, and CoreOS.
The Deis platform combines features and technologies from Google, Docker, and CoreOS.