36 – VXLAN EVPN Multi-Fabrics with Anycast L3 gateway (part 3)
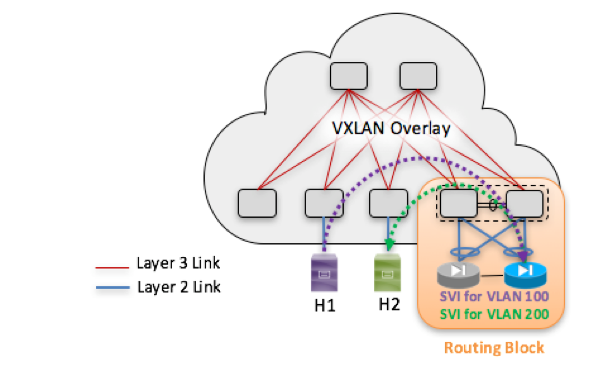
VXLAN EVPN Multi-Fabric with Distributed Anycast Layer 3 Gateway
Layer 2 and Layer 3 DCI interconnecting multiple VXLAN EVPN Fabrics
A distributed anycast Layer 3 gateway provides significant added value to VXLAN EVPN deployments for several reasons:
- It offers the same default gateway to all edge switches. Each endpoint can use its local VTEP as a default gateway to route traffic outside its IP subnet. The endpoints can do so, not only within a fabric but across independent VXLAN EVPN fabrics (even when fabrics are geographically dispersed), removing suboptimal interfabric traffic paths. Additionally, routed flows between endpoints connected to the same leaf node can be directly routed at the local leaf layer.
- In conjunction with ARP suppression, it reduces the flooding domain to its smallest diameter (the leaf or edge device), and consequently confines the failure domain to that switch.
- It allows transparent host mobility, with the virtual machines continuing to use their respective default gateways (on the local VTEP), within each VXLAN EVPN fabric and across multiple VXLAN EVPN fabrics.
- It does not require you to create any interfabric FHRP filtering, because no protocol exchange is required between Layer 3 anycast gateways.
- It allows better distribution of state (ARP, Continue reading

 DANZ addresses customer's concerns for more security.
DANZ addresses customer's concerns for more security.