Engagement Farming
One of my readers asked for my opinion about the following masterpiece posted on (where else) LinkedIn1:

One of my readers asked for my opinion about the following masterpiece posted on (where else) LinkedIn1:

One of my readers asked for my opinion about the following masterpiece posted on (where else) LinkedIn1:

Data changes behavior and behavior changes data. It is a phenomenon that is akin to the Observer Effect in physics in that you can’t observe something without changing its behavior. …
The post The Interplay Of GDP, Inflation, And IT Spending first appeared on The Next Platform.
The Interplay Of GDP, Inflation, And IT Spending was written by Timothy Prickett Morgan at The Next Platform.


Cloudflare has a unique vantage point on the Internet. From this position, we are able to see, explore, and identify trends that would otherwise go unnoticed. In this report we are doing just that and sharing our insights into Internet-wide application security trends.
This report is the third edition of our Application Security Report. The first one was published in March 2022, with the second published earlier this year in March, and this is the first to be published on a quarterly basis.
Since the last report, our network is bigger and faster: we are now processing an average of 46 million HTTP requests/second and 63 million at peak. We consistently handle approximately 25 million DNS queries per second. That's around 2.1 trillion DNS queries per day, and 65 trillion queries a month. This is the sum of authoritative and resolver requests served by our infrastructure. Summing up both HTTP and DNS requests, we get to see a lot of malicious traffic. Focusing on HTTP requests only, in Q2 2023 Cloudflare blocked an average of 112 billion cyber threats each day, and this is the data that powers this report.
But as usual, before we dive in, Continue reading


In 2023, cybersecurity continues to be in most cases a need-to-have for those who don’t want to take chances on getting caught in a cyberattack and its consequences. Attacks have gotten more sophisticated, while conflicts (online and offline, and at the same time) continue, including in Ukraine. Governments have heightened their cyber warnings and put together strategies, including around critical infrastructure (including health and education). All of this, at a time when there were never so many online risks, but also people online — over five billion in July 2023, 64.5% of the now eight billion that are the world’s total population.
Here we take a look at what we’ve been discussing in 2023, so far, in our Cloudflare blog related to attacks and online security in general, with several August reading list suggestions. From new trends, products, initiatives or partnerships, including AI service safety, to record-breaking blocked cyberattacks. On that note, our AI hub (ai.cloudflare.com) was just launched.
Throughout the year, Cloudflare has continued to onboard customers while they were being attacked, and we have provided protection to many others, including once.net, responsible for the 2023 Eurovision Song Contest online voting system Continue reading
In the quickly evolving networking environment, efficient management of routing protocols is essential for reliable and optimized network performance.
Red Hat Ansible Automation Platform is a powerful tool for streamlining repetitive tasks and orchestrating complex network configurations. One crucial aspect of platform-agnostic network management is the management of routing protocols, and in this blog post, we'll explore how Ansible Automation Platform can be utilized to manage OSPF (Open Shortest Path First), a widely used dynamic routing protocol.
At AnsibleFest 2022 we announced a new form of content included in the platform, called Ansible validated content. We also have detailed blogs on Network Automation with Ansible Validated Content using the network.base collection, and BGP Management with Ansible Validated Content using the network.bgp collection. Now, we are adding a network validated content Collection called network.ospf to manage your OSPF protocols.
OSPF is a widely used dynamic routing protocol, and Ansible Automation Platform can significantly streamline the management of OSPF configurations. In this blog post, we will explore the benefits of managing OSPF with Ansible Automation Platform, including some practical examples of how to automate common OSPF tasks that are part of network management.
We’ve got more durm and strang in open source license debate, cars that don't work wihtout a network, something mumble something Fibrechannel, a security acquisition by Check Point, cheesy microchips and more.
The post Network Break 443: Nuclear DCs, Mobile Cars, Fibrechannel, Open Source And Cheese appeared first on Packet Pushers.
We added just a few small features in netlab release 1.6.11:
We added just a few small features in netlab release 1.6.11:
As I dive into the world of VXLAN, I will need a lab as that is the best way to deepen the learning process and to get hands-on experience with a protocol. I will be building a Cisco Nexus9000v lab in VMware ESX but the same images can be used in CML, EveNG, GNS3, etc. The lab is based on the following topology:
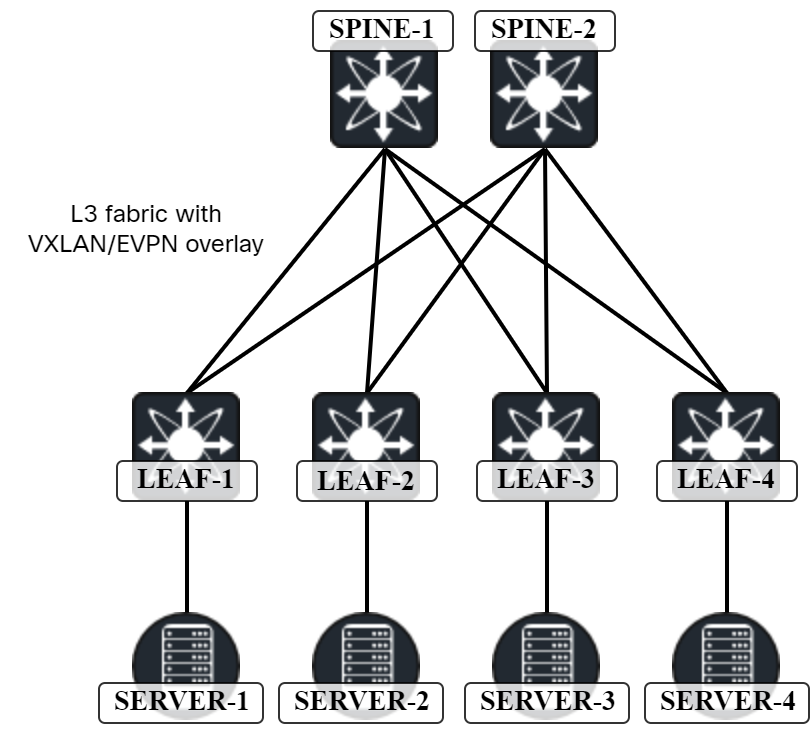
The specific platform I’ll use is the Nexus9300v which has the following requirements:
Note that there is also a Nexus9500v image which is a 16-slot modular chassis. As I have no need for multiple slots, and it requires more CPUs, I will not be using this image.
The specific image I am using is nexus9300v64.10.2.5.M.ova, which is NX-OS version 10.2.5.
Deploying the OVA can take some time but is otherwise straightforward. Refer to my post on caveats for more details.
I have mapped the different NICs to different port groups:
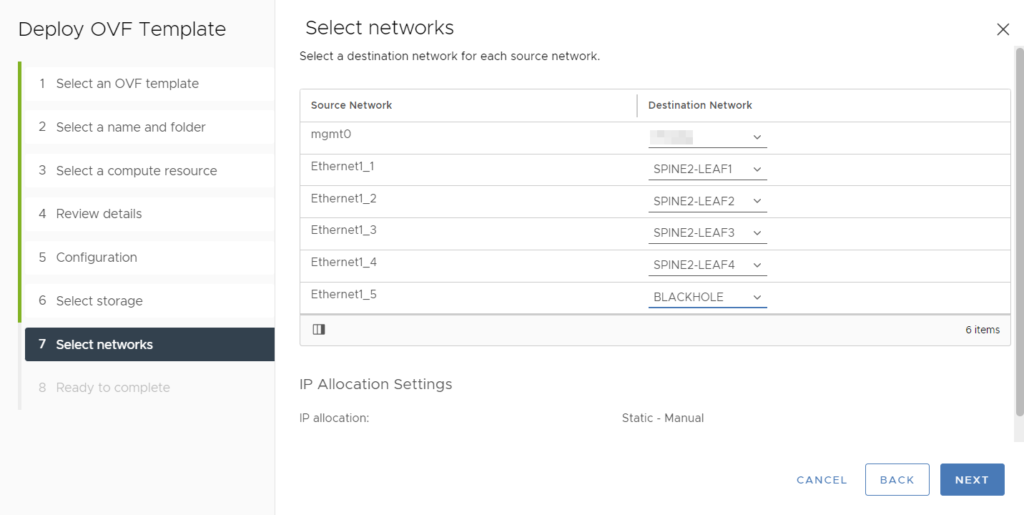
The mgmt0 interface is mapped to my management network so that I can SSH to the devices. I have also created specific port groups for the interconnections between leaf Continue reading