Nokia Expands Cloud to Private LTE Networks
 The company is aggressively going after the enterprise market.
The company is aggressively going after the enterprise market.
 The company is aggressively going after the enterprise market.
The company is aggressively going after the enterprise market.
 This report analyzes the impact of telco cloud transformation—specifically, NFV and SDN—will have on various elements of CSPs’ operations
This report analyzes the impact of telco cloud transformation—specifically, NFV and SDN—will have on various elements of CSPs’ operations
In the last two posts here and here, we have discussed how TCP stack initiates a TCP 3-way handshake and create the appropriate Transmission Control Block for the data to flow reliably. We knew that the main function of the 3-way handshaking is to exchange the sequence numbers, MSS, receive window and other parameters between …
The post TCP Protocol: Flow Control appeared first on Networkers-online.com.
Today, we're introducing two new Cloudflare Traffic products to give customers control over how Cloudflare’s edge network handles their traffic, allowing them to shape and direct it for their specific needs.
More than 10 trillion requests flow through Cloudflare every month. More than 4 million customers and 10% of internet requests benefit from our global network. Cloudflare's virtual backbone gives every packet improved performance, security, and reliability.
That's the macro picture.
What's more interesting is keeping each individual customer globally available. While every customer benefits from the network effect of Cloudflare, each customer is (appropriately) focused on their application uptime, security and performance.
Cloudflare’s new Traffic Control allows a customer to rate limit, shape or block traffic based on the number of requests per second per IP, cookie, or authentication token. Traffic can be controlled on a per-URI (with wildcards for greater flexibility) basis giving pinpoint control over a website, application, or API.
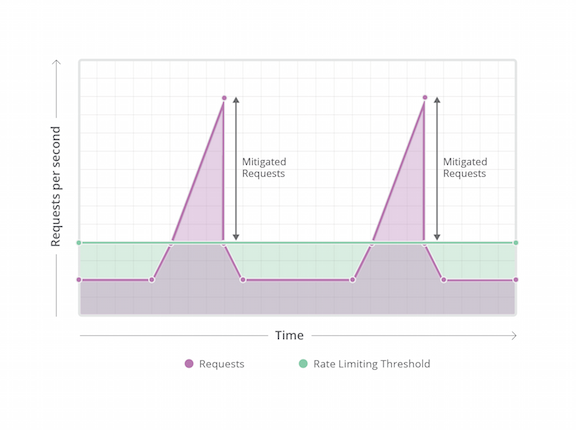
Customers seek reliability and availability in the face of popularity or unexpected traffic such as slow brute force attacks on a WordPress site, Denial of Service against dynamic pages, or the stampede of requests that comes with success. We are the leader at stopping significant Continue reading
This blog article was inspired by some infuriating reads and blogs doing the rounds doing significant damage to business thinking.
I’ve heard so many conversations that confuse Software Defined Networking with Software Driven Networking, automation mixed up with abstraction and MANO (Management and Orchestration) mixed up with configuration management tools that are used for building mutable infrastructure like Puppet, Chef, Ansible and Salt. Is it possible to cross pollinate all of these technologies? Sure, but do not expect people to happy about it. Nerds will love it, process people will hate it and failures will be dominant. Don’t even go there with failing fast. That statement is out of scope as an excuse.
Mutable Infrastructure
Mutable in this sense means to mutate and change. Configuration management tools can create virtual machines, populate them with the packages required to deliver services and place domain specific configuration in order to make them live and in production.
Mutable infrastructure as we know it today is "treat your VMs like cattle, not pets" and this is achieved with well known tools.
Immutable Infrastructure
Think about containers here and unikernels. The idea is we build applications with as few dependencies as possible. Ultimately building applications Continue reading
IPv6 registrations are steady, but demand for IPv4 remains sky high since ARIN's IPv4 supply ran out.