Docker Momentum Mesmerizes and Threatens
 The Docker platform for Linux containers is growing fast -- but what does it mean for the ecosystem?
The Docker platform for Linux containers is growing fast -- but what does it mean for the ecosystem?
 The Docker platform for Linux containers is growing fast -- but what does it mean for the ecosystem?
The Docker platform for Linux containers is growing fast -- but what does it mean for the ecosystem?
 Company joins IBM, GE and others making big-dollar investments in IoT.
Company joins IBM, GE and others making big-dollar investments in IoT.
Over at IPSpace this last week, Ivan pointed to a paper by Dijkstra (and if you don’t know who that is, you need to learn a thing or two about the history of routing protocols—because history makes culture, and culture matters—or, as the tagline on this blog says, culture eats technology for breakfast). In this paper, Dijkstra points out some rather important things about computer science and programming that can be directly applied to the network engineering world. For instance, Ivan says—
I was fascinated with Ivan’s take on this paper—particularly in that complexity is an area I find interesting and very useful in my everyday life as a designer—that I went and read the original article. You should, too.
I think Ivan’s observations are spot on, but I think it’s worthwhile to actually broaden them. From where I sit, after 25 years building and breaking networks, I agree that complexity sells—but it sells for two particular reasons. The reason, as Dijkstra said all those years ago (in computer terms), is this:
Since the Continue reading
128 Technology says its session-aware virtual router provides simpler and more secure networking.
Pica8, early pioneer of disaggregated networking and SDN, today announced a new version of their switch operating system, PicOS v2.7.1. Normally I wouldn’t note a networking OS update, but probably the biggest single update for this release is the new support for 100GigabitEthernet switches, with support for both Broadcom and Cavium / XPliant ASICs.
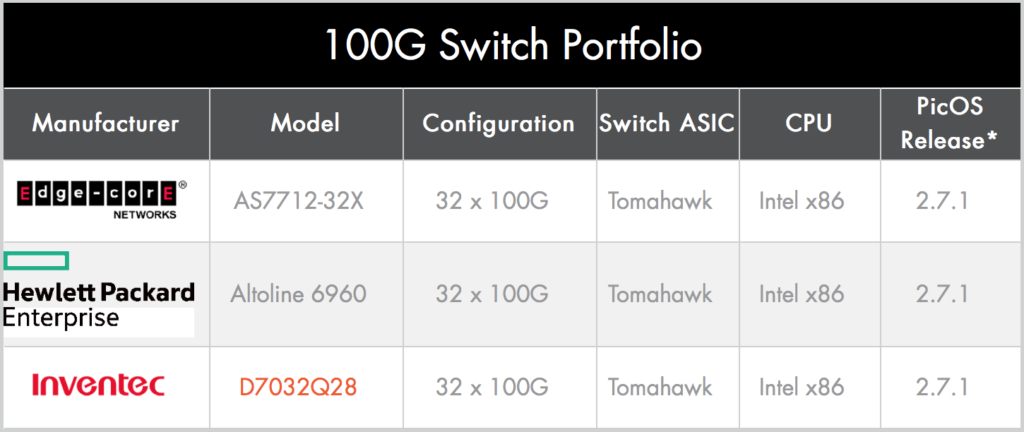
Currently the Hardware Compatibility List for 100G only features Broadcom-based switches but that will undoubtedly change as relative newcomer Cavium / XPliant continues to challenge Broadcom for speed, features and flexibility. I’m also curious to know whether in the future we’ll see hardware on that list using the Barefoot Tofino™ ASIC as well.
In addition to expanding the supported hardware offerings from HP Enterprise, the HCL now also features the first Dell platform to be certified. Dell and HPE are positioning themselves quite effectively as the branded whitebox solution of choice and their devices are supported by a number of software vendors now.
But why do we care about 100G Ethernet, PicOS and more advanced ASICs?

That’s right; because we always want more than we currently have. And, I suppose, because we keep on scaling our networks with more, faster servers. Sure, we’ll Continue reading
We are very excited to announce the private beta of Docker Store, a marketplace for trusted and validated dockerized software – free, open source and commercial.
Our goals with Docker Store are designed around bringing Docker users and ecosystem partners together.
The use and creation of dockerized content has grown exponentially in the last couple of years. This demand on content and the expanded use of Docker within the enterprise naturally led to the need for more content, entitlement, visibility into security profiles and compliance.
Docker Store builds on the Official Images and the popularity of the Docker Hub for community content by providing an official marketplace that provides workflows for those who wish to create and distribute content and those that wish to download content to build their Continue reading
Introducing Docker Datacenter AWS Quickstart and Azure Marketplace Templates production-ready, high availability deployments in just a few clicks.
The Docker Datacenter AWS Quickstart uses a CloudFormation templates and pre-built templates on Azure Marketplace to make it easier than ever to deploy an enterprise CaaS Docker environment on public cloud infrastructures.
The Docker Datacenter Container as a Service (CaaS) platform for agile application development provides container and cluster orchestration and management that is simple, secure and scalable for enterprises of any size. With our new cloud templates pre-built for Docker Datacenter, developers and IT operations can frictionlessly move dockerized applications to an Amazon EC2 or Microsoft Azure environment without any code changes. Now businesses can quickly realize greater efficiency of computing and operations resources and Docker supported container management and orchestration in just a few steps.
Docker Datacenter includes Docker Universal Control Plane, Docker Trusted Registry (DTR), CS Docker Engine with commercial support & subscription to align to your application SLAs:
Businesses today are digital and fundamentally powered by applications – software that drives revenue, engages with customers and runs their operations. The process of making that software has, until recently, been long and cumbersome. The addition of Docker and containerization, a new software supply chain is enabled to bring agility, portability and control together into the enterprise. From security and compliance to shipping more software faster to migrating workloads around sites for the best cost to performance ratio, Docker Datacenter is helping businesses transform their software supply chain.
At DockerCon in Seattle, business of all sizes are sharing their stories Dockering for transformation in development, CI and production environments for all kinds of apps. In this post, I wanted to highlight those companies who are using Docker Datacenter.
Healthdirect Australia was a long time open source Docker user who in the last year transitioned to a Docker Datacenter environment to gain the benefit of having out of the box integrations of a full Docker supported stack. Scott Coulton, the lead architect (and also Docker Captain and DockerCon speaker!) is the driving force behind deploying and running the applications Continue reading
 Session-aware and deterministic routers are the key.
Session-aware and deterministic routers are the key.
The post Worth Reading: One-fourth of malware comes from sharing appeared first on 'net work.