Tools: Conn-check
conn-check – A deployment utility to check connectivity between services conn-check is a small utility, written in Python using the Twisted network library, that verifies outgoing connections from your application servers to services it depends on, e.g. databases, caches, web service APIs, etc.conn-check is used not only to verify network dependency changes at deploy time, […]
The post Tools: Conn-check appeared first on EtherealMind.


 CloudFlare is excited to announce the launch of our newest data center in Perth, Australia. This expands the breadth of our global network to span 80 unique cities across 41 countries, and is our fourth data center in the Oceania region, joining existing data centers in Sydney, Melbourne and Auckland.
CloudFlare is excited to announce the launch of our newest data center in Perth, Australia. This expands the breadth of our global network to span 80 unique cities across 41 countries, and is our fourth data center in the Oceania region, joining existing data centers in Sydney, Melbourne and Auckland.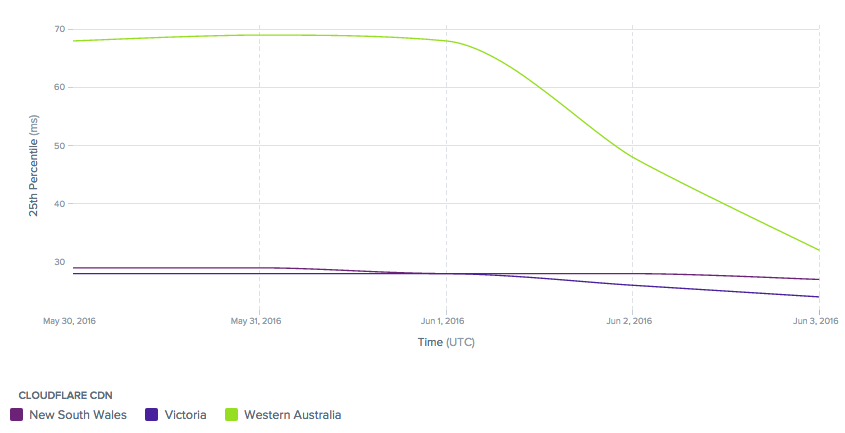
 Former Air Force officers now hunt for malware.
Former Air Force officers now hunt for malware. Torus almost rhymes with CoreOS...
Torus almost rhymes with CoreOS...