Response: Why On-Premises Software Will Die Sooner
This is the most compelling article I’ve ever read about why on-premises applications/software are less competitive. I am reasonably certain that private cloud infrastructure can be as efficient as public cloud and cheaper over some period. What I’m coming to understand is that many of types of cloud-based applications may be much more efficent than […]
The post Response: Why On-Premises Software Will Die Sooner appeared first on EtherealMind.
Is BGP Really that Complex?
Anyone following the popular networking blogs and podcasts is probably familiar with the claim that BGP is way too complex to be used in whatever environment. On the other hand, more and more smart people use it when building their data center or WAN infrastructure. There’s something wrong with this picture.
Read more ...Fortinet Weaves AccelOps Into Its Security Fabric
 The deal ties Fortinet into the SIEM crowd.
The deal ties Fortinet into the SIEM crowd.
Forensic Lab Game Zero – Level 1 Results
The goal of the post is to provide solutions for the first level of the game for "hackers" created by forensic lab of CESNET association. With this game CESNET introduces a work of forensic analysts and test your knowledge of Linux OS. They are several assignments and practical tasks included inside Debian image which is available for download here. The question / answer sheet is located inside the home directory of user kassad.
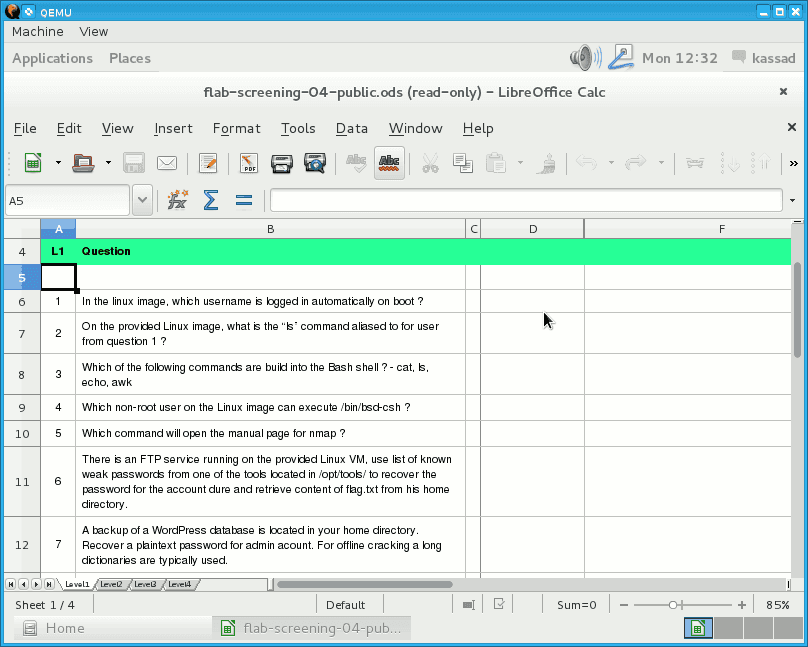
Picture 1 - Answer Sheet
1. In the Linux image, which username is logged in automatically on boot?
Check the desktop environment.
kassad@debian1989:~$ echo $DESKOP_SESSION
gnome-fallback
Check if automated login is enabled for Gnome desktop.
kassad@debian1989:~$ grep 'AutomaticLogin' /etc/gdm3/daemon.conf
AutomaticLoginEnable = true
AutomaticLogin = kassad
The automated login is enabled for the user kassad. Now we need to compute the sha1 hash for the result.
kassad@debian1989:~$ echo -n 'kassad' | sha1sum
fb1216c760d6c0996991108886d1797d8bd4ca27
2. On the provided Linux image, what is the “ls” command aliased to for user from question 1 ?
kassad@debian1989:~$ type ls
ls is aliased to `ls --color=auto'
We can get the result also by checking the content of the file /home/kassad/.bashrc.
kassad@debian1989:~$ grep 'alias ls' /home/kassad/.bashrc
alias ls='ls --color=auto'
kassad@debian1989:~$ echo -n 'ls --color=auto' Continue reading
South African Lengau System Leaps Towards Petaflops
There are plenty of people in industry, academia, and government that believe there is a direct correlation between the investment in supercomputing technologies and the healthy and vibrancy of the regional or national economy. So getting a big bump up in performance, as South Africa’s Center for High Performance Computing has just done this week, is a big deal.
Up until now, CHPC has had fairly modest sized systems, but thanks to Moore’s Law advancements that have radically brought down the cost of compute and a more aggressive plan to invest in HPC within South Africa, CHPC is breaking into …
South African Lengau System Leaps Towards Petaflops was written by Timothy Prickett Morgan at The Next Platform.
Verizon Data Center Sale Still Up in the Air
 Telco will decide in next three months whether or not to move ahead.
Telco will decide in next three months whether or not to move ahead.
Docker and HPE: Accelerating modern app architectures in enterprise datacenters
Docker has evolved tremendously over the last 3 years to empower developers and IT operations teams to maintain greater control over their own environments without sacrificing agility. From an ops tool used by the original dotCloud team, to Docker’s commercially supported Containers-as-a-Service (CaaS) platform, Docker Datacenter (DDC), Docker has been at the forefront of this evolution.
Today we are excited to announce the next evolution in the Docker story providing enterprises with infrastructure optimized for the Docker platform with the leading provider of cloud infrastructure – Hewlett Packard Enterprise (HPE). Together, Docker and HPE will deliver integrated and fully supported Docker ready HPE x86 servers, bundled with Docker’s commercially supported Engine (CS Engine) right out of the box.
TCP/IP Is Lossy Protocol
The foundation of TCP/IP design is that the network is unreliable and packets will be lost.
The post TCP/IP Is Lossy Protocol appeared first on EtherealMind.
What’s Fueling the Move to a Converged Data Platform?
The datacenter is going through tremendous change, and many long-held assumptions are now being called into question. Even the basic process of separating data onto a separate storage area network, growing it, and pulling it across the network and processing it, is no longer necessarily the best way to handle data. The separation between production and analytics, which has evolved into an art form, is also breaking down because it takes a day or longer to get operational data into analytic systems.
As a backdrop to all of these technology changes, organizations say they need more agility. The ability to …
What’s Fueling the Move to a Converged Data Platform? was written by Nicole Hemsoth at The Next Platform.
Verizon Uses Radisys & Mojatatu for SDN & NFV
 Mojatatu Who?
Mojatatu Who?
Worth Reading: IPv6 Link Local Addresses
The post Worth Reading: IPv6 Link Local Addresses appeared first on 'net work.
Supporting the transition to IPv6-only networking services for iOS
Early last month Apple announced that all apps submitted to the Apple Store June 1 forward would need to support IPv6-only networking as they transition to IPv6-only network services in iOS 9. Apple reports that “Most apps will not require any changes”, as these existing apps support IPv6 through Apple's NSURLSession and CFNetwork APIs.
Our goal with IPv6, and any other emerging networking technology, is to make it ridiculously easy for our customers to make the transition. Over 2 years ago, we published Eliminating the last reasons to not enable IPv6 in celebration of World IPv6 Day. CloudFlare has been offering full IPv6 support as well as our IPv6-to-IPv4 gateway to all of our customers since 2012.
Why is the transition happening?
IPv4 represents a technical limitation, a hard stop to the number of devices that can access the Internet. When the Internet Protocol (IP) was first introduced by Vint Cerf and Bob Kahn in the late 1970s, Internet Protocol Version 4 (IPv4) used a 32-bit (four-byte) number, allowing about 4 billion unique addresses. At the time, IPv4 seemed more than sufficient to power the World Wide Web. On January 31, 2011, the top-level pool of Internet Assigned Numbers Authority Continue reading