Satoshi: That’s not how any of this works
In this WIRED article, Gaven Andresen says why he believes Craig Wright's claim to be Satoshi Nakamoto:“It’s certainly possible I was bamboozled,” Andresen says. “I could spin stories of how they hacked the hotel Wi-fi so that the insecure connection gave us a bad version of the software. But that just seems incredibly unlikely. It seems the simpler explanation is that this person is Satoshi.”That's not how this works. That's not how any of this works.
The entire point of Bitcoin is that it's decentralized. We don't need to take Andresen's word for it. We don't need to take anybody's word for it. Nobody needs to fly to London and check it out on a private computer. Instead, you can just send somebody the signature, and they can verify it themselves. That the story was embargoed means nothing -- either way, Andresen was constrained by an NDA. Since they didn't do it the correct way, and were doing it the roundabout way, the simpler explanation is that he was being bamboozled.
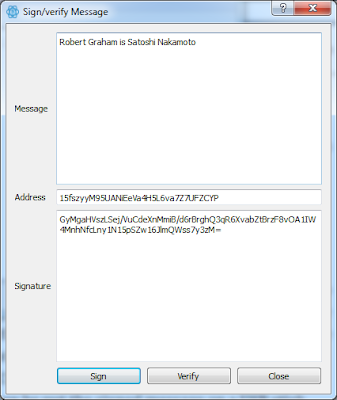
Below is an example of this, using the Electrum Bitcoin wallet software:
This proves that the owner of the Bitcoin Address has signed the Message Continue reading
 Microsoft Azure's IoT philosophy is to support different operating systems and hardware.
Microsoft Azure's IoT philosophy is to support different operating systems and hardware. Every six months or so, the OpenStack community seems to swing between euphoria and despair – depending on the amount of progress being made in deploying OpenStack in production environments.
Every six months or so, the OpenStack community seems to swing between euphoria and despair – depending on the amount of progress being made in deploying OpenStack in production environments.

