College students need food, sleep… and Wi-Fi. [VIDEO]
How important is Wi-Fi to education? When it comes to earning a college degree, reliable Wi-Fi is essential. Students want to be connected anywhere, any time in classrooms, dorm rooms, student centers, stadiums, or just walking across the quad. Reliable...SDN? I Still Don’t kNow what it is…

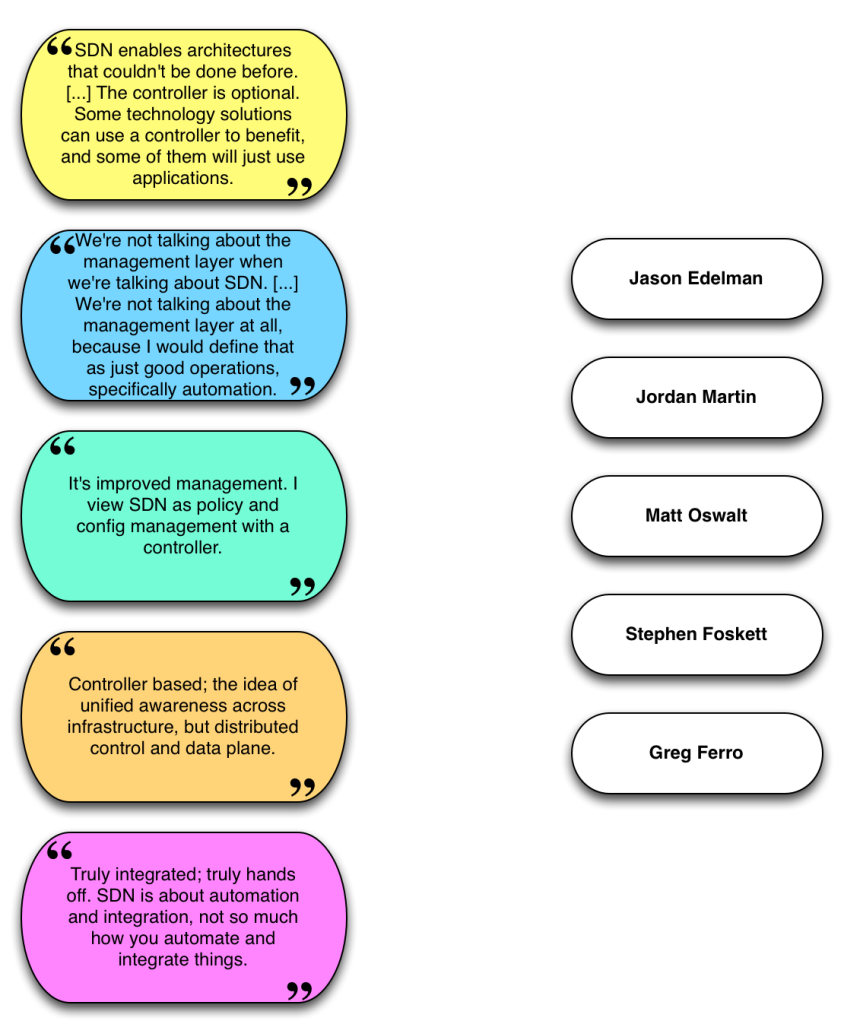
Today you get to play the SDN Definition Game: match the definition of Software Defined Neworking with the person who said it at the Networking Field Day 11 Delegate Roundtable. I’d make this exercise “drag and drop” but that sounds a bit complicated, so instead you’re on your honor not to cheat. Click on the image to see the answers in a new window.
SDN, Whatever That Is
I should note that the quotes I used were taken from conversation, so if I mis-transcribed anything or used it too far out of context I apologize to the speaker concerned. In actual fact though, who said what in this case doesn’t really matter. I shared the quotes to demonstrate that even when defined by a group of smart people like these, there doesn’t seem to be one definition of SDN that everybody can agree on. That has opened the door for marketing departments everywhere to use the SDN tag on anything and everything (aka “SDN Washing”) in the hopes that it sounds impressive and thus presumably increases sales. As a result, many people – both vendors and customers – believe that SDN is becoming a four letter word.
Buy the Solution, Continue reading
Six Practices Of A Great Manager
These six essential practices can help you become a better manager.
The post Six Practices Of A Great Manager appeared first on Packet Pushers.
Six Practices Of A Great Manager
These six essential practices can help you become a better manager.
The post Six Practices Of A Great Manager appeared first on Packet Pushers.
Machine to Machine Networking & IOT
The future of networking, and IT Infrastructure more generally, will be driven by machine to machine interactions.
The post Machine to Machine Networking & IOT appeared first on EtherealMind.
For Those Who Think Differently
A week ago Plexxi’s founder and CTO, Dave Husak presented at the Boston area networking Meetup called BOSNOG. This week Plexxi celebrates our five-year founding anniversary. I was at the Meetup with the Plexxi team and during the Q&A segment a question was asked that provoked some reflection on my part. The question was “what has been the biggest barrier to adoption for Plexxi?” A simple question, but the answer is not so simple.
The biggest barrier to Plexxi has been the ingrained acceptance of networking complexity and singular design to all networking requirements. Over the past five years, many companies brought to market solutions that added to this complexity with little if any underlying changes to the traditional network architecture. The past five years in networking has been witness to a multitude of technical attempts to change networking through the façade of automation, but none have tried to make it simpler and better. During these five years entire product lines from our competitors have achieved full cradle to end-of-life cycle in an attempt to “…harness the intelligent network through programmability and abstraction across multiple layers, offering a choice of protocols, industry standards, and usage-based deployment models” with the goal to Continue reading
Website Reborn and Migrated to Pelican
Hello and Welcome, again, to my newly brushed website !! After a long period of inactivity, I decided to resume my on-line activity and started by migrating away from Wordpress onto a new platform based on something that I use pretty often these days: Python !
Leave Your Gas Can at Home
Talking about current events with my dad recently, he gave me a sage piece of advice. He said, “Son, leave your gas can at home.” Now obviously we weren’t talking about IT, but it got me to thinking. There’s seems to be a lot of this same type of reasoning in our industry. Think about […]
The post Leave Your Gas Can at Home appeared first on Packet Pushers.
Leave Your Gas Can at Home
Talking about current events with my dad recently, he gave me a sage piece of advice. He said, “Son, leave your gas can at home.” Now obviously we weren’t talking about IT, but it got me to thinking. There’s seems to be a lot of this same type of reasoning in our industry. Think about […]
The post Leave Your Gas Can at Home appeared first on Packet Pushers.
The Next Level 4: Good Manager, Bad Manager
On today’s episode of The Next Level, we talk about IT management, what makes someone an effective leader, and strategies for improving your management skills. We delve into how communication preferences affect managers and their reports, how management style can affect employee motivation, and more.
The post The Next Level 4: Good Manager, Bad Manager appeared first on Packet Pushers.
The Next Level 4: Good Manager, Bad Manager
On today’s episode of The Next Level, we talk about IT management, what makes someone an effective leader, and strategies for improving your management skills. We delve into how communication preferences affect managers and their reports, how management style can affect employee motivation, and more.
The post The Next Level 4: Good Manager, Bad Manager appeared first on Packet Pushers.
MPLS Design Case Study
MPLS Design – MPLS Design Case Studies are the useful resources to learn the design details of MPLS. You will be provided a brief information about the business and technical requirements. You can share your answer at the comment section below. Note: This is only one of the case studies in the DesignWorld. DesignWorld provides […]
The post MPLS Design Case Study appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.
MPLS Design Case Study
MPLS Design – MPLS Design Case Studies are the useful resources to learn the design details of MPLS. You will be provided a brief information about the business and technical requirements. You can share your answer at the comment section below. Note: This is only one of the case studies in the DesignWorld. DesignWorld provides […]
The post MPLS Design Case Study appeared first on Orhanergun.