Feds May Have Caused Juniper’s Security Breach & Suffered From It Too
 If only the right hand knew what the left hand was doing.
If only the right hand knew what the left hand was doing.
 If only the right hand knew what the left hand was doing.
If only the right hand knew what the left hand was doing.
 Phew! It was a busy week in the realm of software defined networking (SDN) and network functions virtualization (NFV). Here’s a final roundup: Microsoft launched a technical preview of Azure Stack, software for running a private, on-premises cloud. This opens the possibility of running a hybrid cloud where the public and private halves both run on... Read more →
Phew! It was a busy week in the realm of software defined networking (SDN) and network functions virtualization (NFV). Here’s a final roundup: Microsoft launched a technical preview of Azure Stack, software for running a private, on-premises cloud. This opens the possibility of running a hybrid cloud where the public and private halves both run on... Read more →
This week, Plexxi co-founder Dave Husak hosted interactive discussion on the evolving role of network administrators, the future of cloud environments and bringing order to the chaos of software-defined networking, at a BOSNOG (Boston Network Operators Group) event. Dave and the team enjoyed connecting with other networking professionals in the area and listening to other viewpoints on the future of the network. Take a look at a few photos from the event below and keep an eye on the blog and Twitter for updates on future events.


Photo credit: Ethan Banks
Below please find a few of our top picks for our favorite news articles of the week.
ESG Global: Plexxi Draws Google’s Attention – and Money
By Steve Duplessie
Plexxi is one of those “intelligent infrastructure” companies I’ve been harping about as of late. And by intelligent, in this case I mean a network that can self-actualize and alter its very being based on real-time application and usage demands. It’s way cool. And because I love to tell you “I told you so”, which I did over a year ago, I now get to rub your noses in it. This stuff matters. Google Ventures just plopped some Continue reading
 CEO Chuck Robbins's team continues to take shape.
CEO Chuck Robbins's team continues to take shape.
 Telcos want open hardware in their data centers.
Telcos want open hardware in their data centers.
Dear all, I am happy to announce new release of phpipam IP address management – version 1.2.
For this release backend code was completely rewritten, for database connections now pdo has replaced mysqli, so make sure you php supports pdo and pdo_mysql before upgrading. It also fixes lots of bugs, parametized SQL queries and brings lots of new features, most important are:
And much more. You can find full changelog below, please read it.
If you find phpIPAM useful for your company donations would be highly appreciated 
You can demo it here: http://demo.phpipam.net/
You can download it on sourceforge site: phpipam-1.2 or on github.
Before upgrading make sure you first backup current database, you can follow upgrade guide on our site.
Some screenshots:
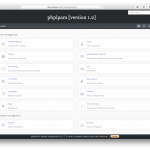
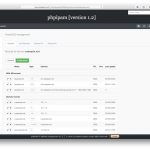
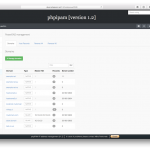
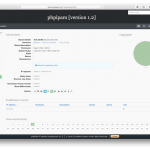
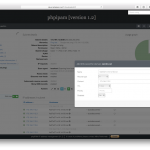
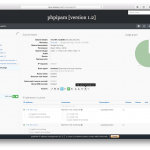
Special thanks to all the people submitting bug reports, translators and feature testers!
Full changelog for this release is:
== 1.20 New features: ------------ + Added multiple simultaneous authentication methods (Apache, AD, LDAP, Radius, NetIQ); + Added fping scanning support; + Added selectable scanning type (ping/pear/fping); + Added L2 Continue reading
On today's episode of the Weekly Show we talk with Big Switch Networks. Rob Sherwood, Big Switch CTO, joins us to discuss the latest capabilities in Big Monitoring Fabric and Big Cloud Fabric.
The post Show 273: Big Switch Networks: Product Updates & Free Editions (Sponsored) appeared first on Packet Pushers.
On today's episode of the Weekly Show we talk with Big Switch Networks. Rob Sherwood, Big Switch CTO, joins us to discuss the latest capabilities in Big Monitoring Fabric and Big Cloud Fabric.
The post Show 273: Big Switch Networks: Product Updates & Free Editions (Sponsored) appeared first on Packet Pushers.