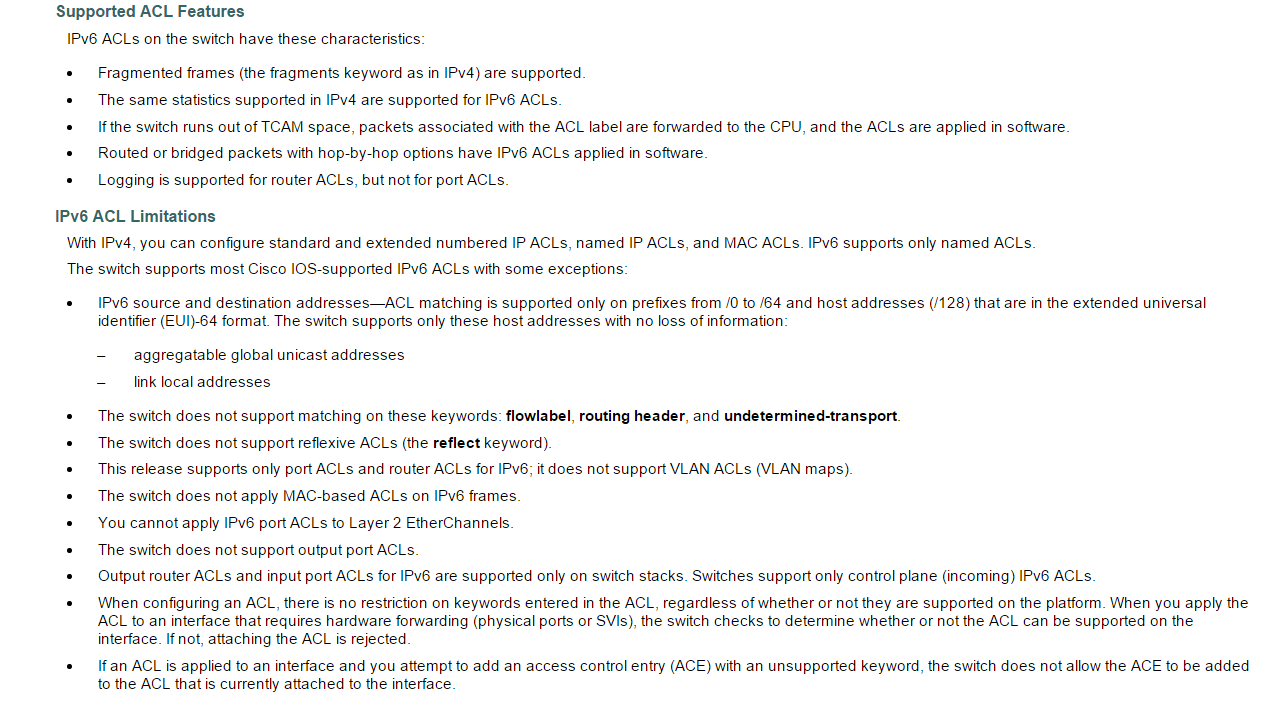
Catalyst 3750 IPv6 ACL Limitations
I recently ran into some limitations of IPv6 ACLs on the Catalyst 3750 platform. I had developed an ACL to protect from receiving traffic from unwanted address ranges such as ::, ::1, ::FFFF:0:0/96. The first address is the unspecified address, the second one is the loopback address and the last one is IPv4 mapped traffic. The ACL also contained an entry to deny traffic with routing-type 0.
Note that no error is output when adding the entries in the ACL, only when applying the ACL to an interface.
% This ACL contains following unsupported entries.
% Remove those entries and try again.
deny ipv6 any any routing-type 0 sequence 20
deny ipv6 host ::1 any sequence 290
deny ipv6 host :: any sequence 310
deny ipv6 ::FFFF:0.0.0.0/96 any sequence 330
% This ACL can not be attached to the interface.
SW1(config-if)#
%PARSE_RC-4-PRC_NON_COMPLIANCE: `ipv6 traffic-filter v6-ACL-IN in'
From the configuration guide, the following limitations apply to the Catalyst 3750 platform.
What this means is that we can’t match on flowlabel, routing-header and undetermined transport upper layer protocol. We also need to match on networks ranging from /0 to /64 and host addresses that are belonging to global unicast Continue reading
Super Smartphone Apps For Network Administrators
These mobile apps can improve productivity and save precious time for IT pros managing and troubleshooting networks.ONOS’ Drake Release Doesn’t Try to be SDN for Everybody
 Ericsson and Huawei pitch in for the fourth ONOS code release in 10 months.
Ericsson and Huawei pitch in for the fourth ONOS code release in 10 months.
Peeking at Pkybot
For the past few months ASERT has been keeping an eye on a relatively new banking malware (“banker”) known as “Pkybot”. It is also being classified as a variant of “Bublik”, but the former is much more descriptive of the malware. This post will take a peek at some of the bits and pieces of […]Peeking at Pkybot
For the past few months ASERT has been keeping an eye on a relatively new banking malware (“banker”) known as “Pkybot”. It is also being classified as a variant of “Bublik”, but the former is much more descriptive of the malware.
This post will take a peek at some of the bits and pieces of Pkybot and the campaign using it. The visibility provided can help organizations better understand, detect, and protect against this current threat.
Sample
One of the recent samples analyzed by ASERT has the following hashes:
MD5: 9028d9b64a226b750129b41fbc43ed5e
SHA256: 38eb7625caf209ca2eff3fa46b8528827b7289f1
At the time of this writing it has a VirusTotal detection ratio of 16/57 with just about all the detections being generic in nature. One positive for reverse engineers though is that this sample comes unpacked.
Pkybot
While there’s been some research into the malware already [1] [2], a review and fleshing out never hurts.
Encrypted Bits
Pkybot contains a number of interesting items that are encrypted with the XTEA encryption algorithm. The key used is generated at runtime from a hardcoded seed value (DWORD):
It can also be generated using this Python code snippet. Along with the generated XTEA key, this IDA Continue reading
Renewing ipSpace.net Subscription before It Expires
One of my subscribers asked me: “My subscription is valid till early December. How could I renew it now (due to budgetary reasons)?”
While I already had the process to do just that, there was no link that one could use (you had to know the correct URL). I’ve fixed that – you’ll find the renewal link on the first page of my.ipSpace.net
Open Virtual Network (OVN)
Open Virtual Network (OVN) is an open source network virtualization solution built as part of the Open vSwitch (OVS) project. OVN provides layer 2/3 virtual networking and firewall services for connecting virtual machines and Linux containers.
OVN is built on the same architectural principles as VMware's commercial NSX and offers the same core network virtualization capability — providing a free alternative that is likely to see rapid adoption in open source orchestration systems, Mirantis: Why the Open Virtual Network (OVN) matters to OpenStack.
This article uses OVN as an example, describing a testbed which demonstrates how the standard sFlow instrumentation build into the physical and virtual switches provides the end-to-end visibility required to manage large scale network virtualization and deliver reliable services.
Open Virtual Network
The Northbound DB provides a way to describe the logical networks that are required. The database abstracts away implementation details which are handled by the ovn-northd and ovn-controllers and presents an easily consumable network virtualization service to orchestration tools like OpenStack.
The purple tables on the left describe a simple logical switch LS1 that has two logical ports LP1 and LP2 with MAC addresses AA and BB respectively. The green tables on the right show Continue reading
More Sites Turn Up With Cisco Router Malware
 SYNful Knock has been found at 199 IP addresses so far.
SYNful Knock has been found at 199 IP addresses so far.
Using POX components to create a software defined networking application
When network engineers are learning the concepts of software defined networking and SDN controllers, they may want to experiment with SDN network scenarios before learning to write programs to be used by the SDN controllers.
POX is a simple-to-use SDN controller that is bundled with the Mininet SDN network emulator and is used in education and research as a learning and prototyping tool. POX components are Python programs that implement networking functions and can be invoked when POX is started. POX comes with a few stock components ready to use.

In this tutorial, we will use stock POX components to implement basic switching functionality with loop prevention in a software defined network, without writing any code. Then, we will explore how the SDN controller programs the OpenFlow-enabled switched in a network created using the Mininet network emulator.
Prerequisite knowledge required
This tutorial assumes you already have the the prerequisite knowledge defined in the list below. If you need to understand more about any of the topics listed below, the list provides links to resources that offer enough information to prepare you to work through this tutorial.
- You have a basic understanding of Ethernet networks, IP networking, and software Continue reading
Spousetivities at VMworld EMEA
Spousetivities returns to VMworld EMEA this year with a new set of activities. If you haven’t registered yet, here’s a quick look at the pretty impressive set of tours and activities that are planned.
- Montserrat and Wine Country: The famous Monastery of Montserrat, one of the black Madonnas of Europe, Santa Cova, a fantastic lunch of local Catalan country cuisine, and wine tasting. What more could one want?
- Costa Brava and Medieval Girona: It’s not every day you get the opportunity to tour a medieval walled city founded by the Romans in the 1st century.
- Wines of Catalunya: Personal tours with local, resident wine makers arranged exclusively for Spousetivities participants.
- Medieval mountain village and panoramic trails: Cobblestone streets and stone houses in a medieval mountain village, then a four-course lunch in a traditional Catalan country restaurant followed by a light hike to some great look-outs, streams, rivers, and waterfalls.
For more detailed descriptions of the activities, I encourage you to visit the Spousetivities site. When you’re ready to get signed up, head on over to the registration page. These are some pretty great activities!
Zerodium’s million dollar iOS9 bounty
Zerodium is offering a $1 million bounty for a browser-based jailbreak. I have a few comments about this. The two keywords to pick up on are "browser-based" and "untethered". The word "jailbreak" is a red-herring.It's not about jailbreaks. Sure, the jailbreak market is huge. It's really popular in China, and there are reports of $1 million being spent on jailbreaks. But still, actually getting a return on such an investment is hard. Once you have such a jailbreak, others will start reverse engineering it, so it's an extremely high risk. You may get your money back, but there's a good chance you'll be reverse-engineered before you can.
The bigger money is in the intelligence market or 0days. A "browser-based" jailbreak is the same as a "browser-based" 0day. Intelligence organizations around the world, from China, to Europe, and most especially the NSA, have honed their tactics, techniques, and procedures around iPhone 0days. Terrorist leaders are like everyone else, blinging themselves out with status displays like iPhones. Also, iPhone is a lot more secure than Android, so it's actually a good decision (intelligence organizations have hacked Android even more).
Every time Apple comes out with a new version (like iOS9), they Continue reading