Site Upgrades for September 2015
First, I want to apologize for not doing my job. Over the past couple years I’ve let this site become slightly stagnant. I won’t attempt to make excuses, but I will say that I’m in a much better place now. Hopefully inspiration will continue to strike, and I will continue to put pen to paper… or finger to keyboard?
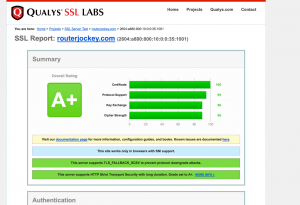 Over the past couple weeks I’ve put a fair amount of time and monetary resources into RouterJockey. I’ve fixed quite a few CSS bugs, without hopefully creating more. I purchased an SSL certificate and moved the site to HTTPS, which helps me more than it really does you… but in doing so, I’ve also enabled SPDY 3.1. SPDY should help load times, but Nginx was already doing a pretty good job. Oh, in order to get SPDY up to 3.1 I was forced to migrate away from the Ubuntu repo for Nginx.. but that’s not a huge deal.
Over the past couple weeks I’ve put a fair amount of time and monetary resources into RouterJockey. I’ve fixed quite a few CSS bugs, without hopefully creating more. I purchased an SSL certificate and moved the site to HTTPS, which helps me more than it really does you… but in doing so, I’ve also enabled SPDY 3.1. SPDY should help load times, but Nginx was already doing a pretty good job. Oh, in order to get SPDY up to 3.1 I was forced to migrate away from the Ubuntu repo for Nginx.. but that’s not a huge deal.
I’ve also spent some time redesigning the menu bar, adding new links, removing some useless ones, and writing an all new disclaimer. Please be sure to read and understand everything posted on that page before attempting to read any of my Continue reading
TM Forum Keeps its Head Above the Weeds on NFV Technology
 Operators don't want TM Forum to get lost in NFV technicalities. They want the focus on making money.
Operators don't want TM Forum to get lost in NFV technicalities. They want the focus on making money.
Some notes on NSA’s 0day handling process
The EFF got (via FOIA) the government's official policy on handling/buying 0days. I thought I'd write up some notes on this, based on my experience. The tl;dr version of this post is (1) the bits they redacted are the expected offensive use of 0days, and (2) there's nothing surprising in the redacted bits.Before 2008, you could sell 0days to the government many times, to different departments ranging from the NSA to Army to everybody else. These government orgs would compete against each other to see who had the biggest/best cyber-arsenal.
In 2008, there came an executive order to put a stop to all this nonsense. Vuln sellers now only sold 0days once to the government, and then the NSA would coordinate them with everyone else.
That's what this "VEP" (Vuln Equities Process) document discusses -- how the NSA distributes vulnerability information to all the other "stakeholders".
I use "stakeholders" loosely, because there are a lot of government organizations who feel entitled to being part of the 0day gravy train, but who really shouldn't be. I have the impression the NSA has two processes, the real one that is tightly focused on buying vulns and deploying them in the field, Continue reading
Intent-Based Networking Seeks Network Effect
 What's the latest on intent-based networking--the hot new topic in SDN.
What's the latest on intent-based networking--the hot new topic in SDN.
SDxCentral Weekly News Roundup — September 18, 2015
 Intel boosts IoT for cars; former Cisco and Time Warner CTOs intersect; Khosla Ventures funds Gitlab.
Intel boosts IoT for cars; former Cisco and Time Warner CTOs intersect; Khosla Ventures funds Gitlab.
iPexpert’s Newest “CCIE Wall of Fame” Additions 9/18/2015
Please join us in congratulating the following iPexpert students who have passed their CCIE lab!
This Week’s CCIE Success Stories
- Ajay Edara, CCIE #36424 (R&S & Wireless)
- Shiv Shankar, CCIE #43675 (Routing & Switching)
- Andy Harrison, CCIE #50052 (Routing & Switching)
- Mike Burk, CCIE #50207 (Wireless)
- Tony Ilorah, CCIE #50210 (Security)
- Ahmad Nawid Azizi, CCIE #50254 (Routing & Switching)
We Want to Hear From You!
Have you passed your CCIE lab exam and used any of iPexpert’s self-study products, or attended a CCIE Bootcamp? If so, we’d like to add you to our CCIE Wall of Fame!
Starbucks On Dune, WiFi Allergies: This Week On The Internet
From pumpkin spice on Dune to WiFi allergies to a giant robot fight and more, here's some interesting stories that crossed my browser this week.
The post Starbucks On Dune, WiFi Allergies: This Week On The Internet appeared first on Packet Pushers.
Featured Interview: Brocade’s Jon Hudson on the Current & Future State of SDN, NFV, & DevOps
 Brocade's Jon Hudson sat down with SDxCentral to discuss the current and future state of SDN, NFV, and DevOps.
Brocade's Jon Hudson sat down with SDxCentral to discuss the current and future state of SDN, NFV, and DevOps.
Optimize Open NX-OS with Cisco’s Network Programmability Tools
 Join the September 25th Cisco DemoFriday and learn how you can benefit from network programmability as you transition from legacy systems to open standard interfaces.
Join the September 25th Cisco DemoFriday and learn how you can benefit from network programmability as you transition from legacy systems to open standard interfaces.
F5 Certification Path – How to become F5 Certified
Original content from Roger's CCIE Blog Tracking the journey towards getting the ultimate Cisco Certification. The Routing & Switching Lab Exam
The F5 certification path is a series of exams administered by pearsonvue where you start of by passing 2 exams to become an F5 Certified Administrator and then depending on your specialist area you can add to that by becoming an F5 Certified Technology Specialist. The certification cost is $135 per exam which would be $170 […]
Post taken from CCIE Blog
Original post F5 Certification Path – How to become F5 Certified
Docker Global Hack Day #3: How to Submit Hacks
Thank you to everyone who already submitted awesome Docker hacks for Docker Global Hack Day #3 – we’re super excited to see the final submissions! Still looking for a project to join? Head to the Docker Global Hack Day #3 … ContinuedWhy DevOps Is the Imperative Companion to SDN & NFV
 Achieve the “big bang” transformation.
Achieve the “big bang” transformation.
Startup Cato Networks Calls SD-WAN ‘Short-Sighted’
 Is it the end for MPLS? Cato claims it's got a way to give MPLS-like performance to Internet links.
Is it the end for MPLS? Cato claims it's got a way to give MPLS-like performance to Internet links.
Stuff The Internet Says On Scalability For September 18th, 2015
Hey, it's HighScalability time:
- terabits: Facebook's network capacity; 56.2 Gbps: largest extortion DDoS attack seen by Akamai; 220: minutes spent usings apps per day; $33 billion: 2015 in-app purchases; 2334: web servers running in containers on a Raspberry Pi 2; 121: startups valued over $1 billion
- Quotable Quotes:
- A Beautiful Question: Finding Nature's Deep Design: Two obsessions are the hallmarks of Nature’s artistic style: Symmetry—a love of harmony, balance, and proportion Economy—satisfaction in producing an abundance of effects from very limited means
- @Carnage4Life: ad blocking Apple has done to Google what Google did to MSFT. Added a feature they can't compete with without breaking their biz model
- @shellen: FWIW - Dreamforce is a localized weather system that strikes downtown SF every year causing widespread panic & bad slacks.
- @KentBeck: first you learn the value of abstraction, then you learn the cost of abstraction, then you're ready to engineer
- @doctorow: Arab-looking man of Syrian descent found in garage building what looks like a bomb
- @kixxauth: Idempotency is not something you take a pill for. -- ZeroMQ
- Continue reading
What Does It Mean When A Project Has Been Forked?
Open source projects that involve lots of folks sometimes run into conflicts. Should the project go in direction X, or direction Y? Is feature A more important, or feature B? And so on. Sometimes the concerns around an open source project are more pragmatic than pedantic. Should we, as a commercial entity, continue to use this open source project as is, or go in our own direction with it? The keyword to look for in these circumstances is fork.PlexxiPulse—A Funding Frenzy
This week, we announced that we have raised a $35 million round of financing. The round was led by a new investor with participation from our existing investors (Lightspeed Venture Partners, Matrix Partners and North Bridge Venture Partners) bringing our total funding to $83 million. The capital raised will fuel the expansion of our sales, marketing, customer support, and research and development efforts. We’re so proud of what we’ve accomplished in this year and are eager to see what the rest of 2015 has in store for us. Take a look at this week’s blog post from our CEO Rich Napolitano on Plexxi’s continued momentum on the heels of our funding announcement.
Social media has been buzzing this week, see below! Have a great weekend.
The post PlexxiPulse—A Funding Frenzy appeared first on Plexxi.
