Cisco ACI Integrates Security from Sourcefire
 ACI strengthens its security story with a next-generation firewall and IPS.
ACI strengthens its security story with a next-generation firewall and IPS.
 ACI strengthens its security story with a next-generation firewall and IPS.
ACI strengthens its security story with a next-generation firewall and IPS.
A fantastic overview of the Elastic Cloud project from Luca Relandini
http://lucarelandini.blogspot.com/2015/03/the-elastic-cloud-project-porting-to.html?
And don’t miss this excellent recent post which explains how to invoke UCS Director workflows via the northbound REST API.
http://lucarelandini.blogspot.com/2015/03/invoking-ucs-director-workflows-via.html
 Executive shakeup? Let's talk about OpenDaylight and intent-driven networking instead.
Executive shakeup? Let's talk about OpenDaylight and intent-driven networking instead.
When we started CloudFlare, we thought we were building a service to make websites faster and more secure, and we wanted to make the service as easy and accessible as possible. As a result, we built the CloudFlare interface to put basic functions front and center and designed it to look more like a consumer app than the UI for the powerful network it controlled.
Over time, we realized there was a lot more to CloudFlare. In 2011, we added the concept of Apps, and a myriad of additional performance and security features from Rocket Loader to Railgun were added too. All these additional settings got buried under a lowly gear menu next to each site in a customer's account.
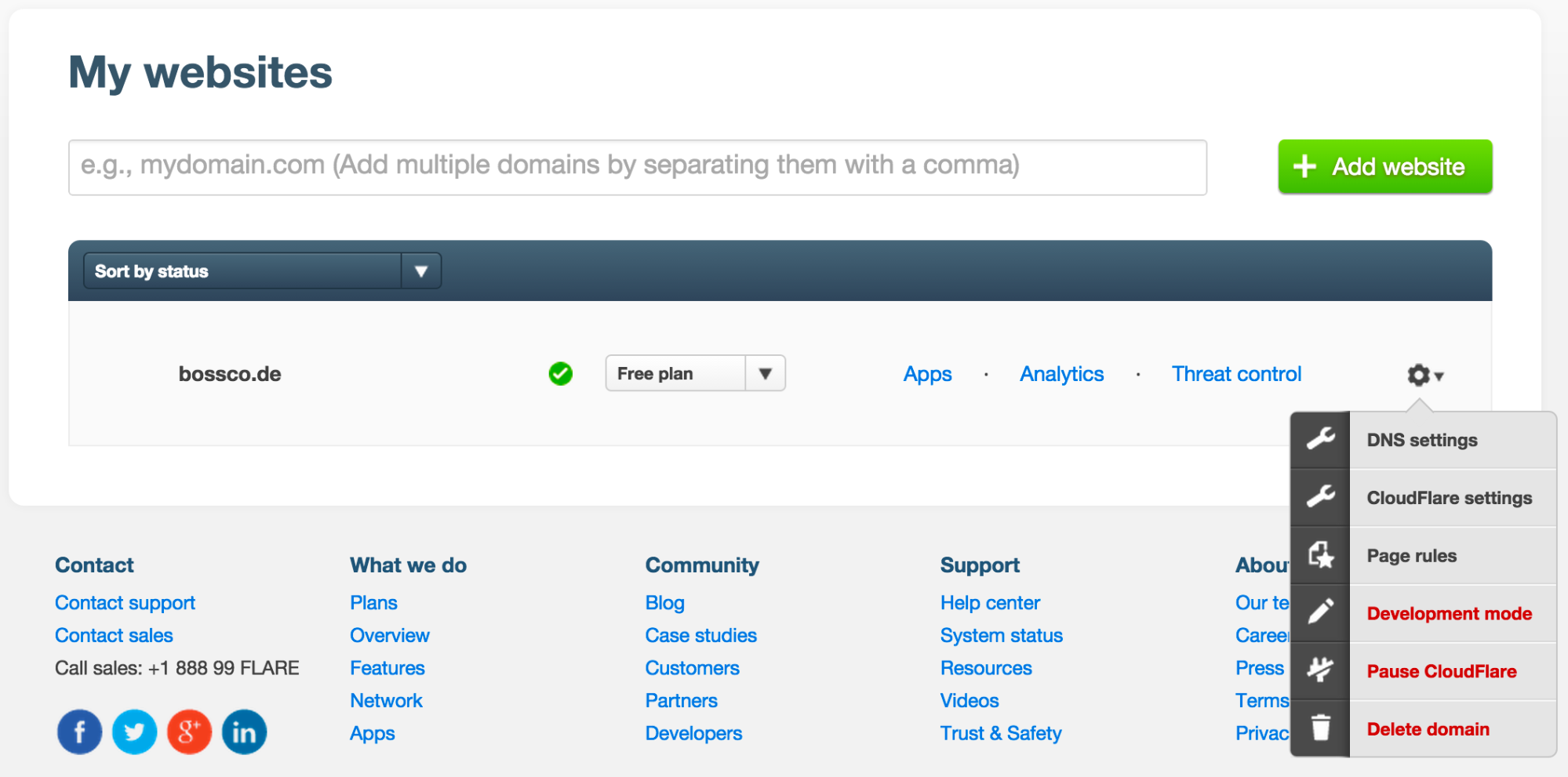
While still easier to navigate than the average enterprise app, using our UI could be a frustrating experience. For instance, imagine you wanted to turn on Rocket Loader for multiple sites. You'd have to go to My Websites, click the gear menu next to one of your domains, navigate to CloudFlare Settings, select the Performance Settings tab, scroll to Rocket Loader, then toggle it on. Then you had to go back to My Websites and repeat the process again for Continue reading