Public Videos: Whole IPv6 Curriculum

Based on the feedback I received on LinkedIn and in private messages, I made all my IPv6 content public; you can watch those videos without an ipSpace.net account.
Want to spend more time watching free ipSpace.net videos? The complete list is here.
NB531: Cisco Spotlights AI, Unified Management at CLUS; Ultra Ethernet 1.0 Unveiled
Take a Network Break! Our Red Alert for the week is a remote code execution vulnerability in open-source XDR platform Wazuh. In tech news, we dig into several announcements from Cisco Live US including: unified management of Meraki and Catalyst gear, new switches, an AI Assistant for the Meraki dashboard, a Deep Network Model LLM,... Read more »Sandia Deploys SpiNNaker2 Neuromorphic System
Some heavy hitters like Intel, IBM, and Google along with a growing number of smaller startups for the past couple of decades have been pushing the development of neuromorphic computing, hardware that looks to mimic the structure and function of the human brain. …
Sandia Deploys SpiNNaker2 Neuromorphic System was written by Jeffrey Burt at The Next Platform.
netlab 25.06: Fixing Nokia SR-OS Configuration Templates
TL&DR: netlab release 25.06 was published last week.
Before discussing the new features, let’s walk the elephant out of the room: I changed the release versions to YY.MM scheme, so I will never again have to waste my time on the existential question of which number in the release specification to increase.
Now for the new features:
A QUIC Progress Report
There has been a major change in the landscape of the internet over the past few years with the progressive introduction of the QUIC transport protocol. Here I’d like to look at where we are up to with the deployment of QUIC on the public Internet. In so doing we also need to consider whether the DNS is ossifying in front of our eyes!QO100 early success
I have heard and been heard via QO-100! As a licensed radio amateur have sent signals via satellite as far away as Brazil.
What it is
QO-100 is the first geostationary satellite with an amateur radio payload. A “repeater”, if you will. Geostationary means that you just aim your antenna (dish) once, and you can use it forever.
This is amazing for tweaking and experimenting. Other amateur radio satellites are only visible in the sky for minutes at a time, and you have to chase them across the sky to make a contact before it’s gone.
They also fly lower, meaning they can only see a small part of the world at a time. QO-100 can at all times see and be seen by all of Africa, Europe, India, and parts of Brazil.
Needs a bit more equipment, though
Other “birds” (satellites) can be accessed using a normal handheld FM radio and something like an arrow antenna. Well, you should actually have two radios, so that you can hear yourself on the downlink while transmitting.
There are also linear amateur radio satellites. For them you need SSB radios, which narrows down which radios you can use. And you still need Continue reading
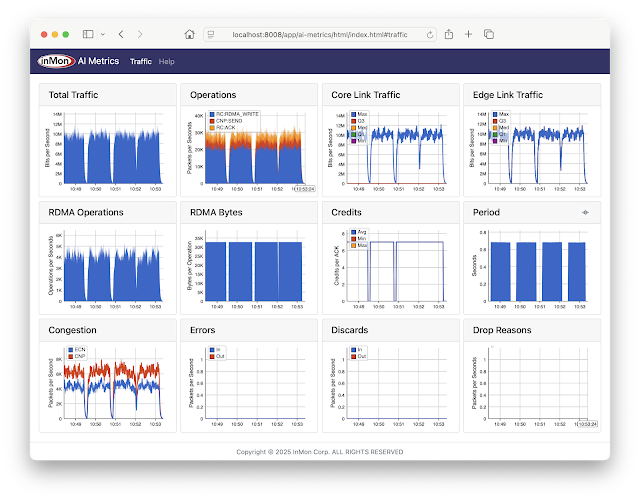
AI network performance monitoring using containerlab
AI Metrics is available on GitHub. The application provides performance metrics for AI/ML RoCEv2 network traffic, for example, large scale CUDA compute tasks using NVIDIA Collective Communication Library (NCCL) operations for inter-GPU communications: AllReduce, Broadcast, Reduce, AllGather, and ReduceScatter.The screen capture is from a containerlab topology that emulates a AI compute cluster connected by a leaf and spine network. The metrics include:
- Total Traffic Total traffic entering fabric
- Operations Total RoCEv2 operations broken out by type
- Core Link Traffic Histogram of load on fabric links
- Edge Link Traffic Histogram of load on access ports
- RDMA Operations Total RDMA operations
- RDMA Bytes Average RDMA operation size
- Credits Average number of credits in RoCEv2 acknowledgements
- Period Detected period of compute / exchange activity on fabric (in this case just over 0.5 seconds)
- Congestion Total ECN / CNP congestion messages
- Errors Total ingress / egress errors
- Discards Total ingress / egress discards
- Drop Reasons Packet drop reasons
Note: Clicking on peaks in the charts shows values at that time.
This article gives step-by-step instructions to run the demonstration.
git clone https://github.com/sflow-rt/containerlab.gitDownload the sflow-rt/containerlab project from GitHub.
git clone https://github.com/sflow-rt/containerlab.git cd containerlab ./run-clabRun the above commands Continue reading
Laser-Based Compute Promises To Light The Way To Faster Physics Sims
While the world continues to fixate on AI, there are still plenty of high performance computing workloads that need doing and a speedup to any one part can have a big impact, whether it be computational fluid dynamics, material analysis, or something else. …
Laser-Based Compute Promises To Light The Way To Faster Physics Sims was written by Tobias Mann at The Next Platform.
Hedge 271: AI and Creativity
AI chatbots and image creators are all the rage right now–we are using them for everything from coding to writing books to creating short movies. One question we do not ask often enough, though, is how this impact human creators. How will these tools shape creativity and thinking skills?
HN785: How To Take Your First Steps Into Network Automation
There’s an old saying that a journey of a thousand miles begins with the first step. On today’s show, we talk about taking your first step into network automation with guest Joseph Nicholson. He’s been automating at NTT Data for many years now and has some perspective to share. He’s a network engineer by trade,... Read more »Finding Source Routing Paths
In the previous blog post, we discussed the generic steps that network devices (or a centralized controller) must take to discover paths across a network. Today, we’ll see how these principles are applied in source routing, one of the three main ways to move packets across a network.
Brief recap: In source routing, the sender has to specify the (loose or strict) path a packet should take across the network. The sender thus needs a mechanism to determine that path, and as always, there are numerous solutions to this challenge. We’ll explore a few of them, using the sample topology shown in the following diagram.
Cloudflare service outage June 12, 2025
On June 12, 2025, Cloudflare suffered a significant service outage that affected a large set of our critical services, including Workers KV, WARP, Access, Gateway, Images, Stream, Workers AI, Turnstile and Challenges, AutoRAG, Zaraz, and parts of the Cloudflare Dashboard.
This outage lasted 2 hours and 28 minutes, and globally impacted all Cloudflare customers using the affected services. The cause of this outage was due to a failure in the underlying storage infrastructure used by our Workers KV service, which is a critical dependency for many Cloudflare products and relied upon for configuration, authentication and asset delivery across the affected services. Part of this infrastructure is backed by a third-party cloud provider, which experienced an outage today and directly impacted availability of our KV service.
We’re deeply sorry for this outage: this was a failure on our part, and while the proximate cause (or trigger) for this outage was a third-party vendor failure, we are ultimately responsible for our chosen dependencies and how we choose to architect around them.
This was not the result of an attack or other security event. No data was lost as a result of this incident. Cloudflare Magic Transit and Magic WAN, DNS, cache, proxy, Continue reading
IPB177: Introducing the IPv6 Compatibility Checker
The Hexabuild team is providing a new community resource, an IPv6 compatibility checker, for those trying to figure out IPv6 network hardware and software compatibility. It’s currently in an alpha version. We talk about what inspired it, what it does, and possible future updates. We also want to get your feedback on whether this is... Read more »AMD Plots Interception Course With Nvidia GPU And System Roadmaps
To a certain extent, Nvidia and AMD are not really selling GPU compute capacity as much as they are reselling just enough HBM memory capacity and bandwidth to barely balance out the HBM memory they can get their hands on, thereby justifying the ever-embiggening amount of compute their GPU complexes get overstuffed with. …
AMD Plots Interception Course With Nvidia GPU And System Roadmaps was written by Timothy Prickett Morgan at The Next Platform.
TNO032: Automation First: NetOps at Megaport
Today we chat with Megaport’s Mitchell Warden, Founding Engineer; and Alexis Bertholf, Global Technical Evangelist, to find out what NetOps is like at Megaport, a company that provides scalable internet connections for all types of organizations. We look at the origins of Megaport and how the company started with the intention of network automation from... Read more »It’s Been Three Years, So It’s Time For Another PCI-Express Speed Bump
PCI-SIG, the organization that oversees the roadmap for the critical PCI-Express peripheral attachment specification, is continuing to keep to its three-year drumbeat for releasing the next iteration of the interconnect spec and already has its sights on the one after that, expected to be released in 2028 and appear in devices in 2030 or so. …
It’s Been Three Years, So It’s Time For Another PCI-Express Speed Bump was written by Jeffrey Burt at The Next Platform.
N4N030: Network Shapes and Sizes
What shape is your network? In other words, what is its topology? On today’s episode, we discover the different types of network topologies and designs used in the enterprise, data center, and service provider networks. We cover leaf/spine, hub and spoke, point to point, mesh, and others. We also talk about how topologies affect traffic... Read more »Cisco’s Hyperscale And Cloud AI Push Will Give It Enterprise Clout
Much of the business that Cisco Systems and others have been doing in the AI infrastructure field since OpenAI lit the generative AI fuse with ChatGPT in November 2022 has been deploying hardware and software with the hyperscalers, a lucrative business that led company executives to promise to sell as much as $1 billion in back-end network technology by the end of its fiscal year and then to blow past that a quarter early. …
Cisco’s Hyperscale And Cloud AI Push Will Give It Enterprise Clout was written by Jeffrey Burt at The Next Platform.
Powering All Ethernet AI Networking
Artificial Intelligence (AI), powered by accelerated processing units (XPUs) like GPUs and TPUs, is transforming industries. The network interconnecting these processors is crucial for efficient and successful AI deployments. AI workloads, involving intensive training and rapid inferencing, require very high bandwidth interconnects with low and consistent latency, and the highest reliability to maximize XPU utilization and reduce AI job completion time (JCT). A best-of-breed network with AI-specific optimizations is critical for delivering AI applications, with any JCT slowdown leading to revenue loss. Typical workloads have fewer, very high-bandwidth, low-entropy flows that run for extended periods, exchanging large messages synchronously, necessitating advanced lossless forwarding and specialized operational tools. They differ from cloud networking traffic as summarized below: