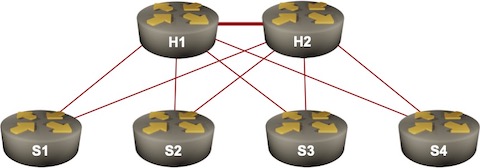
Hedge 122: The Internet Architecture Board

What is the Internet Architecture Board (IAB) of the IETF? What role does the IAB play in the larger ecosystem of building and deploying standard protocols? In this episode of the Hedge, Tom and Ethan “flip roles” with Russ to ask these questions.