Multifactor Authentication Is Being Targeted by Hackers
It was only a matter of time. While multifactor authentication (MFA) makes logging into systems safer, it doesn’t make it “safe.” As well-known hacker KnownBe4, showed in 2018 it’s easy to Proofpoint has found transparent reverse proxy. Typically transparent reverse proxies, such as the open source man-in-the-middle (MitM) attacks to steal credentials and session cookies. Why go to this trouble? Because, as an MFA company 78% of users now use MFA, compared to just 28% in 2017. That’s good news, but it’s also given cybercrooks the incentive they needed to target MFA. A Range of Kits To make it easy for wannabe hackers. Proofpoint found today’s phishing kits range from “simple open-source kits with human-readable code and no-frills functionality Continue reading
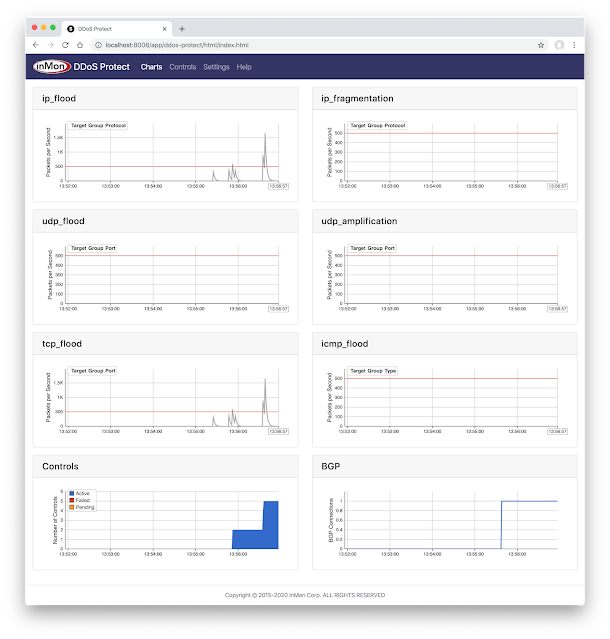
 There are various ways I can defend against this, but one (sorta ugly) option (I don’t actually recommend, read to the bottom to see my logic) is to create a blackhole aka a null route.
There are various ways I can defend against this, but one (sorta ugly) option (I don’t actually recommend, read to the bottom to see my logic) is to create a blackhole aka a null route.