Cloud Engineering For The Network Pro: Part 2 – Virtual Network Architecture (Video)
Part 2 of this cloud engineering series by Michael Levan digs into the basic network services available in Azure and AWS. You can subscribe to the Packet Pushers’ YouTube channel for more videos as they are published. It’s a diverse a mix of content from Ethan and Greg, plus selected videos from our events. It’s […]
The post Cloud Engineering For The Network Pro: Part 2 – Virtual Network Architecture (Video) appeared first on Packet Pushers.
Millions Pay AWS To Give Amazon An Insurmountable IT Advantage
What company has the lowest IT spending budget in the world, but has also paradoxically spent more money than any company in history investing in creating a new, modern, cloud-native system that is capable of running just about any application at just about any necessary scale? …
Millions Pay AWS To Give Amazon An Insurmountable IT Advantage was written by Timothy Prickett Morgan at The Next Platform.
Heavy Networking 616: Do We Need An SMTP Alternative? TMTP And MNM Are Here To Find Out
The SMTP protocol isn't broken, but email kinda is. Spam, phishing, and other unwanted messages are easy to deliver and harder to stop. On today's Heavy Networking we discuss TMTP and mnm, a proposed new protocol and client that aim to preserve the benefits of email while eliminating vulnerabilities and offering a better experience. Our guest is Liam Breck, creator of TMTP and mnm.Heavy Networking 616: Do We Need An SMTP Alternative? TMTP And MNM Are Here To Find Out
The SMTP protocol isn't broken, but email kinda is. Spam, phishing, and other unwanted messages are easy to deliver and harder to stop. On today's Heavy Networking we discuss TMTP and mnm, a proposed new protocol and client that aim to preserve the benefits of email while eliminating vulnerabilities and offering a better experience. Our guest is Liam Breck, creator of TMTP and mnm.
The post Heavy Networking 616: Do We Need An SMTP Alternative? TMTP And MNM Are Here To Find Out appeared first on Packet Pushers.
Could Open Base Station SoCs Unleash A New Era In Mobile Infrastructure?
This article was originally published in Packet Pushers Ignition on March 23, 2021. Just as nature abhors a vacuum and seeks to fill it with any available matter, business abhors a single-source solution to wide scale problems. Competitors rush to fill the vacuum of choice with alternative, interchangeable products. The IT market typically fosters competition […]
The post Could Open Base Station SoCs Unleash A New Era In Mobile Infrastructure? appeared first on Packet Pushers.
Arm CPUs To Take A Bite Out Of The HPC Market
Arm-based servers have had a somewhat checkered history that has seen many abortive attempts to challenge the X86 processor hegemony, but the firm appears bullish about its chances in the high performance computing (HPC) sector, where it believes its licensing model and the energy efficiency of its architecture give it an edge. …
Arm CPUs To Take A Bite Out Of The HPC Market was written by Daniel Robinson at The Next Platform.
Backing Up the Dump Truck

Hello Ellen,
I have received a number of these spam messages over the past few weeks and I had hoped they would eventually taper off. However, it doesn’t appear that is the case. So I’ll take the direct approach.
I’m a member of the CCIE Advisory Council. Which means I am obligated to report any and all attempts to infringe upon the integrity of the exam. As you have seen fit to continue to email me to link to your site to promote your test dumps I think you should be aware that I will be reporting you to the CCIE team.
Good luck in your future endeavors after they shut you down for violating their exam terms and conditions. And do not email me again.
That’s an actual email that I sent TODAY to someone (who probably isn’t really named Ellen) that has been spamming me to link to their CCIE dump site. The spam is all the same. They really enjoy reading a random page on my site, usually some index page picked up by a crawler. They want me to insure a link to their site which is a brain dump site for CCIE Continue reading
Missing Manuals – io_uring worker pool
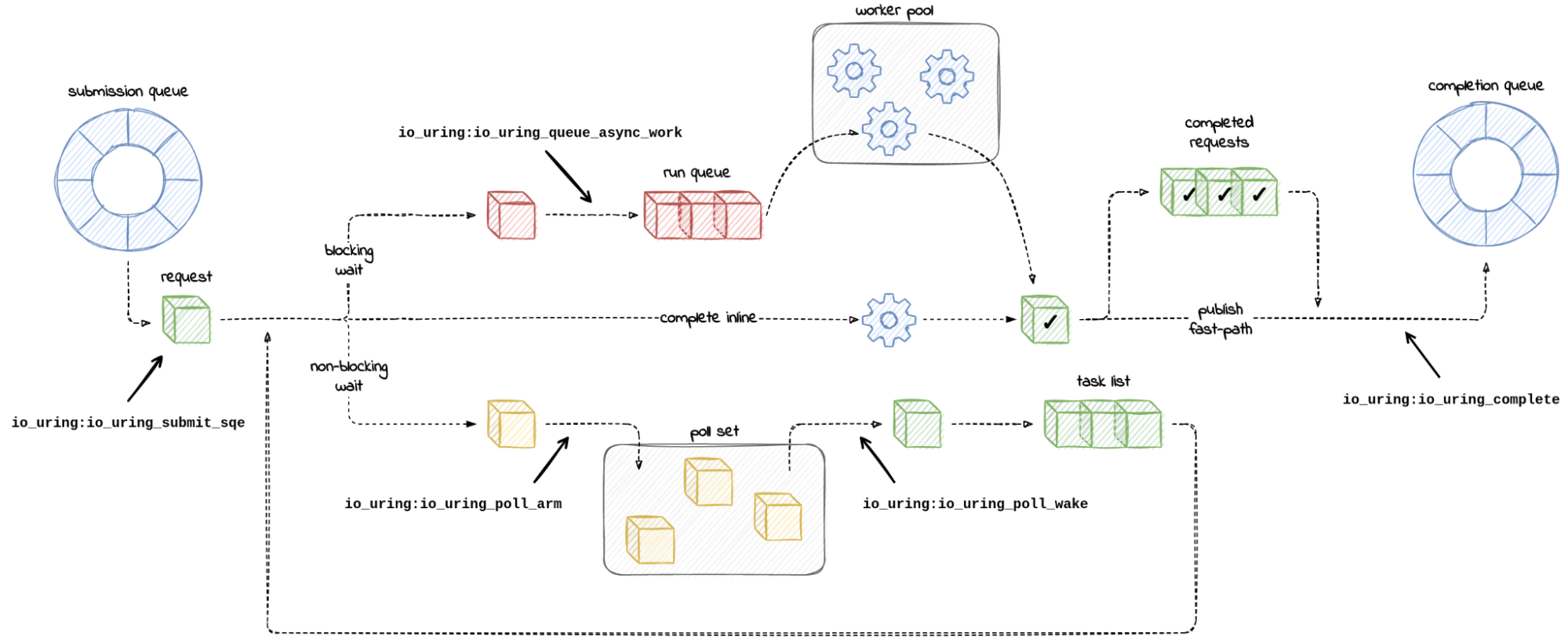
Chances are you might have heard of io_uring. It first appeared in Linux 5.1, back in 2019, and was advertised as the new API for asynchronous I/O. Its goal was to be an alternative to the deemed-to-be-broken-beyond-repair AIO, the “old” asynchronous I/O API.
Calling io_uring just an asynchronous I/O API doesn’t do it justice, though. Underneath the API calls, io_uring is a full-blown runtime for processing I/O requests. One that spawns threads, sets up work queues, and dispatches requests for processing. All this happens “in the background” so that the user space process doesn’t have to, but can, block while waiting for its I/O requests to complete.
A runtime that spawns threads and manages the worker pool for the developer makes life easier, but using it in a project begs the questions:
1. How many threads will be created for my workload by default?
2. How can I monitor and control the thread pool size?
I could not find the answers to these questions in either the Efficient I/O with io_uring article, or the Lord of the io_uring guide – two well-known pieces of available documentation.
And while a recent enough io_uring man page touches on the Continue reading
Lesson Learned: The Way Forward
I tried to wrap up my Lessons Learned presentation on a positive note: what are some of the things you can do to avoid all the traps and pitfalls I encountered in the almost four decades of working in networking industry:
- Get invited to architecture and design meetings when a new application project starts.
- Always try to figure out what the underlying actual business needs are.
- Just because you can doesn’t mean that you should.
- Keep it as simple as possible, but no simpler.
- Work with your peers and explain how networking works and why you face certain limitations.
- Humans are not perfect – automate as much as it makes sense, but no more.
Lesson Learned: The Way Forward
I tried to wrap up my Lessons Learned presentation on a positive note: what are some of the things you can do to avoid all the traps and pitfalls I encountered in the almost four decades of working in networking industry:
- Get invited to architecture and design meetings when a new application project is starting.
- Always try to figure out what the underlying actual business needs are.
- Just because you can doesn’t mean that you should.
- Keep it as simple as possible, but no simpler.
- Work with your peers, and explain how networking works and why you’re facing certain limitations.
- Humans are not perfect – automate as much as it makes sense but no more.
Just in Time Infrastructure: Infrastructure at the Speed of Business
IT must deliver infrastructure in a timely, just in time, manner these days to keep pace with the speed of modern business.Xilinx Works From The Edge Towards Datacenters With Versal FPGA Hybrids
The “Everest” family of hybrid compute engines made by Xilinx, which have lots of programmable logic surrounded by hardened transistor blocks and which are sold under the Versal brand, have been known for so long that we sometimes forget – or can’t believe – that Versal chips are not yet available as standalone products in the datacenter or within the Alveo line of PCI-Express cards from the chip maker. …
Xilinx Works From The Edge Towards Datacenters With Versal FPGA Hybrids was written by Timothy Prickett Morgan at The Next Platform.